
CSO Awards winners highlight security innovation and transformation
The task of securing an organization’s data and systems has become increasingly complex. It has also […]
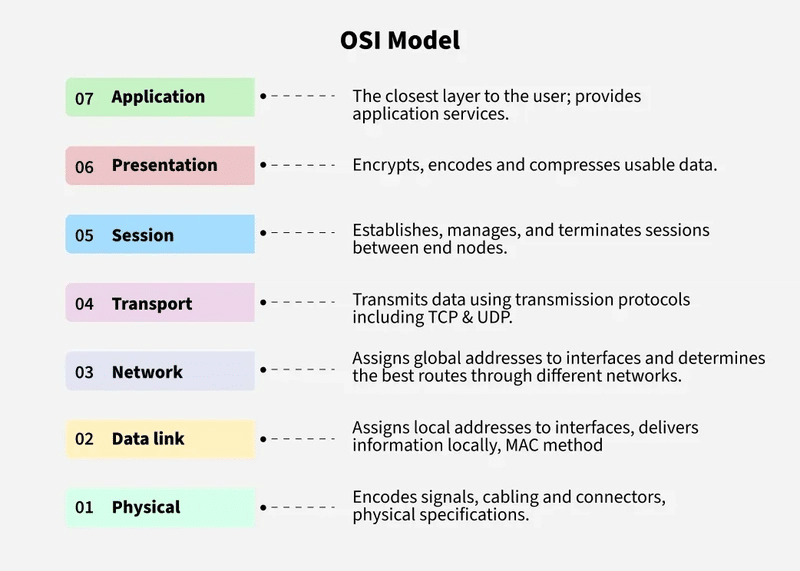
Network Forensics 101
There are many systems that track and record network activities and data. However, there are still […]
Why ethics must drive AI adoption in finance
Global Finance The field of Artificial Intelligence (AI) is transforming the world of finance and informing […]

Agentic AI – der neue Horror für Sicherheitsentscheider?
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/05/AI-product-or-feature-shutterstock_2626499403.jpg?quality=50&strip=all 3976w, https://b2b-contenthub.com/wp-content/uploads/2025/05/AI-product-or-feature-shutterstock_2626499403.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/05/AI-product-or-feature-shutterstock_2626499403.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/05/AI-product-or-feature-shutterstock_2626499403.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/05/AI-product-or-feature-shutterstock_2626499403.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/05/AI-product-or-feature-shutterstock_2626499403.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/05/AI-product-or-feature-shutterstock_2626499403.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/05/AI-product-or-feature-shutterstock_2626499403.jpg?resize=150%2C84&quality=50&strip=all 150w, […]

Fortra patches critical GoAnywhere MFT flaw akin to past ransomware exploits
Users of Fortra’s GoAnywhere MFT solution are urged to patch a critical vulnerability that could allow […]
Italy Leads EU With First National AI Law
Italy has become the first country in the European Union to pass a national law regulating […]
Self-Driving Cars UK Startup in Talks for $500M Investment From Nvidia
Fresh off announcing a surprising $5B investment in Intel, Nvidia is in talks to invest $500 […]
‘Horrified’ Pope Leo XIV Rejects AI Virtual Pope Plan
Pope Leo XIV has rejected a proposal to create an AI-powered “virtual pope,” saying he was […]

How Does Fidelis NDR Use Machine Learning to Detect Threats Earlier and Respond Faster?
You face more signals than your SOC can triage and more lateral movement than your legacy […]
ChatGPT Hits 838M Global Users
ChatGPT now commands 838 million unique users globally, processes more than one billion messages daily, and […]
