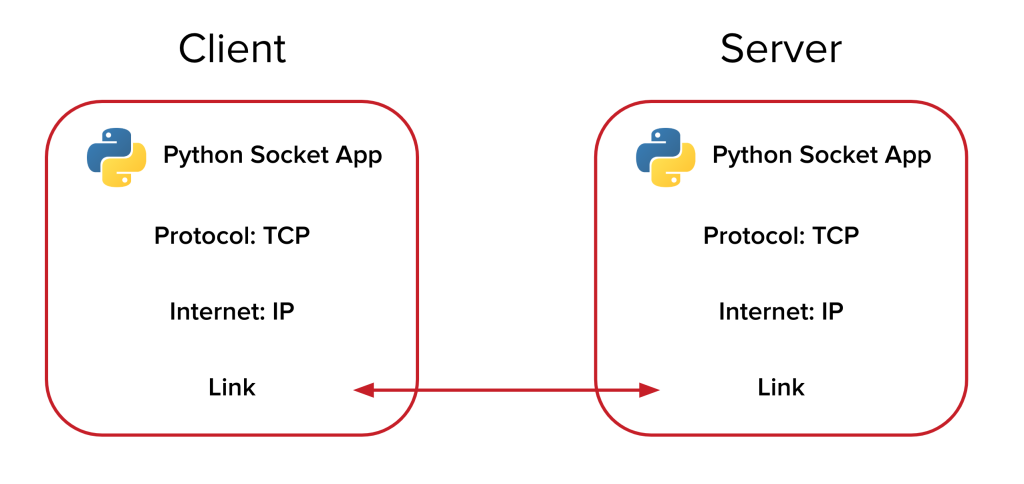
🚨 Building a Malicious Backdoor & C2 Server in Python! 💻🔥
Malicious backdoors and Command & Control (C2) servers are tools commonly employed in cyberattacks to enable […]

🚨 Building a Malicious Backdoor & C2 Server in Python! 💻🔥
Malicious backdoors and Command & Control (C2) servers are tools commonly employed in cyberattacks to enable […]
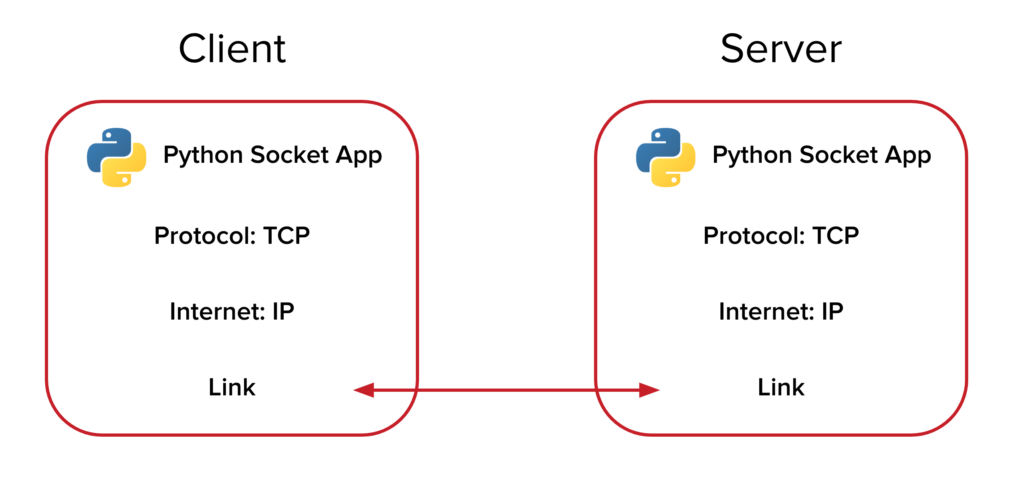
Building a Malicious Backdoor & C2 Server in Python
Backdoors and Command & Control (C2) servers are some of the tools used in cyberattacks to […]
Mastering Linux: The Top Commands Every Server Administrator Should Know
As a Linux system administrator, you must understand how to configure and manage your Linux servers […]

Microsoft files lawsuit against LLMjacking gang that bypassed AI safeguards
Microsoft has filed a civil lawsuit against an international gang of cybercriminals that exploited stolen credentials […]

Is your enterprise ‘cyber resilient’? Probably not. Here’s how other boards fixed that
In the escalating battle against cyberthreats, most businesses pour more security resources into prevention and detection: […]
MITRE ATT&CK Use Cases: Essential Security Tactics for 2025 Threats
The MITRE ATT&CK framework documents 196 individual techniques and 411 sub-techniques that help organizations understand and […]
DPDP Act Compliance Checklist for Businesses
The Digital Personal Data Protection (DPDP) Act, 2023, is a landmark legislation aimed at regulating the […]

Hacker verschlüsseln Daten von rund 12.000 Patienten
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2321046757_71010c.jpg?quality=50&strip=all 16634w, https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2321046757_71010c.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2321046757_71010c.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2321046757_71010c.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2321046757_71010c.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2321046757_71010c.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2321046757_71010c.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/02/shutterstock_2321046757_71010c.jpg?resize=150%2C84&quality=50&strip=all 150w, […]
Top Strategies for Effective Cobalt Strike Detection in Your Network
What is Cobalt Strike? Cobalt Strike is a penetration testing tool designed for adversary simulation and […]