
CISOs should address identity management ‘as fast as they can’ says CrowdStrike exec
CISOs should be moving “as fast as they can” to close holes in their identity and […]

US Cybercom, CISA retreat in fight against Russian cyber threats: reports
Two reports published on Friday signaled the Trump administration may no longer consider Russia the US […]

Download the AI Risk Management Enterprise Spotlight
Download the March 2025 issue of the Enterprise Spotlight from the editors of CIO, Computerworld, CSO, […]

Download the UEM vendor comparison chart, 2025 edition
From the editors of our sister publication Computerworld, this vendor comparison chart helps IT and security […]

Forscher entdecken LLM-Sicherheitsrisiko
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/03/shutterstock_2450854311.jpg?quality=50&strip=all 6000w, https://b2b-contenthub.com/wp-content/uploads/2025/03/shutterstock_2450854311.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/03/shutterstock_2450854311.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/03/shutterstock_2450854311.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/03/shutterstock_2450854311.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/03/shutterstock_2450854311.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/03/shutterstock_2450854311.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/03/shutterstock_2450854311.jpg?resize=150%2C84&quality=50&strip=all 150w, […]

Ransomware access playbook: What Black Basta’s leaked logs reveal
Black Basta, one of the most successful ransomware groups over the past several years, had a […]

Why cyber attackers are targeting your solar energy systems — and how to stop them
High energy costs and concerns over the stability and capacity of electric grids are leading businesses […]
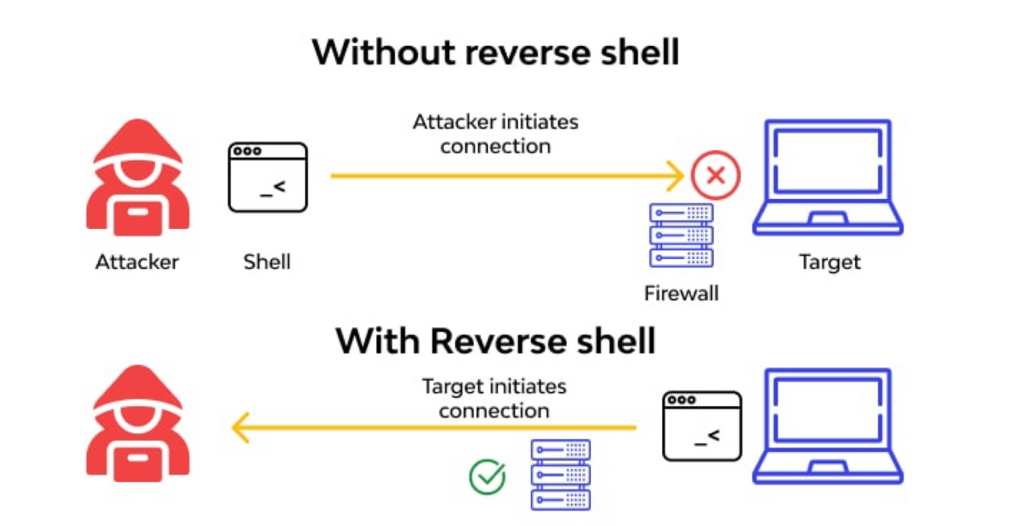
Building a Custom Python Backdoor
Hey guys! Rocky here. So, you wanna learn how to build a custom backdoor in Python? […]

Building a Custom Python Backdoor
Hey guys! 👋 Rocky here. So, you wanna learn how to build a custom backdoor in […]

Building a Custom Python Backdoor
Hey guys! 👋 Rocky here. So, you wanna learn how to build a custom backdoor in […]