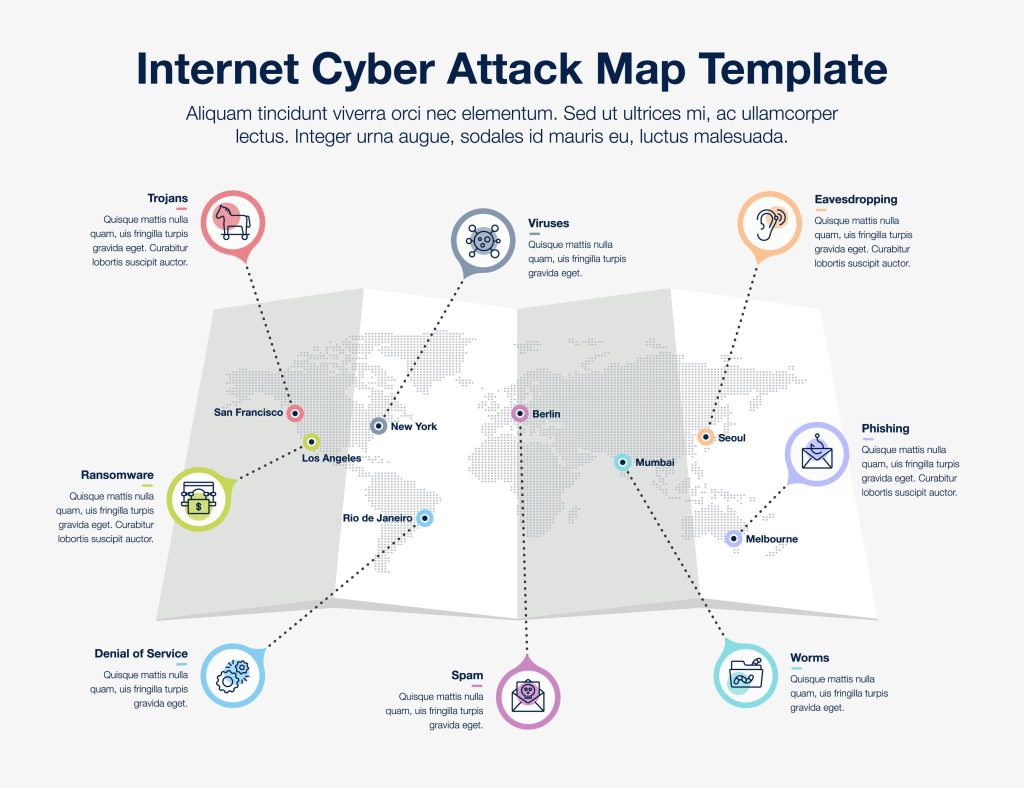
Shocking 12 Recent Major Cyber Attacks 2026 That Are Reshaping Global Security
The year 2026 has already witnessed an alarming rise in cybercrime activity worldwide. From large-scale ransomware […]

Is Local Hardware is All You Need?
While majority of the GenAI investment / capex is focused on new datacenters, GPUs and hardware, […]
Breaking the JARs: Security Issues in Java ARchives
“This building is protected by a very secure system … But like all systems it has […]
12 ~/.bashrc Hacks Hackers Can’t Live Without
Introduction Hook: Your terminal is your home. Why live in a shack when you can build […]
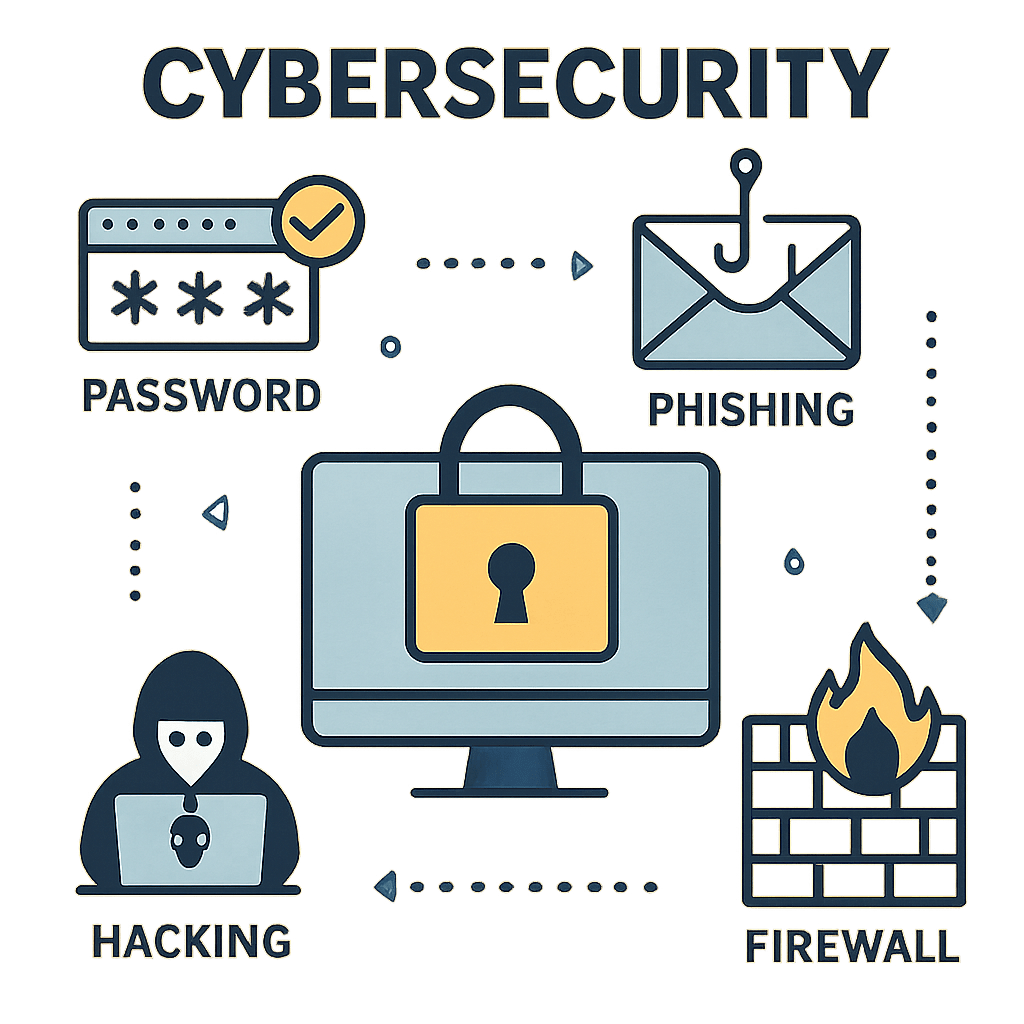
Learn Cybersecurity: Essential Skills for Beginners
In today’s digital age, cybersecurity is more important than ever. With increasing cyber threats, the demand […]
Linux Security in 2026: Threat Landscape, Trending Attacks, and How to Harden Your Servers
Linux underpins cloud infrastructure, containers, edge devices, and supercomputers — and while it’s long been regarded […]

Pentesting Is Decision-Making, Not Scanning
Most newcomers to cybersecurity, and even some seasoned professionals, fundamentally misunderstand what a penetration test actually […]

How to Get Into Cybersecurity and Carve a Career Path (Without Lying to Yourself)
Let’s start with the hard truth you already suspect: most advice about starting a cybersecurity career is […]
Why Tool Collectors Fail at Pentesting
Here is the real talk: your giant GitHub folder of 500 tools, your Kali box, loaded […]
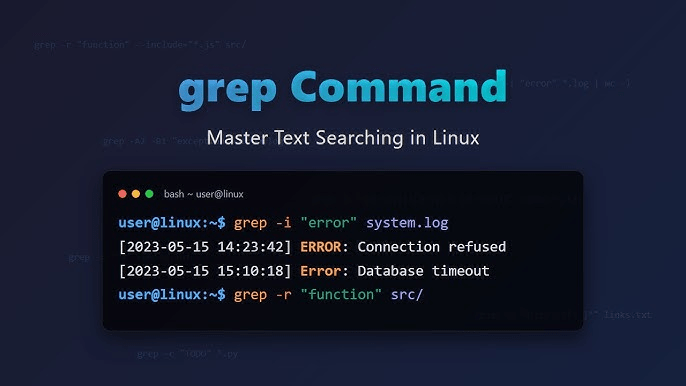
10 Essential Linux Commands to Boost Productivity and Save Hours Weekly
Ever feel like you’re doing the same boring computer tasks over and over? Clicking through folders […]