
Why cyber attackers are targeting your solar energy systems — and how to stop them
High energy costs and concerns over the stability and capacity of electric grids are leading businesses […]

Die besten XDR-Tools
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/02/original2cso_ArtemisDiana.jpg?quality=50&strip=all 6500w, https://b2b-contenthub.com/wp-content/uploads/2025/02/original2cso_ArtemisDiana.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/02/original2cso_ArtemisDiana.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/02/original2cso_ArtemisDiana.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/02/original2cso_ArtemisDiana.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/02/original2cso_ArtemisDiana.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/02/original2cso_ArtemisDiana.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/02/original2cso_ArtemisDiana.jpg?resize=150%2C84&quality=50&strip=all 150w, […]
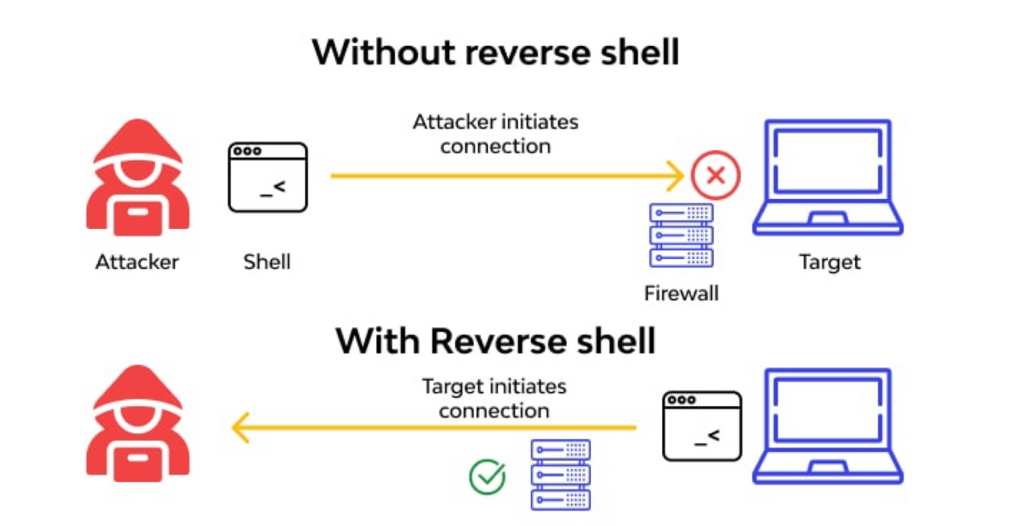
Building a Custom Python Backdoor
Hey guys! Rocky here. So, you wanna learn how to build a custom backdoor in Python? […]

Building a Custom Python Backdoor
Hey guys! 👋 Rocky here. So, you wanna learn how to build a custom backdoor in […]

Building a Custom Python Backdoor
Hey guys! 👋 Rocky here. So, you wanna learn how to build a custom backdoor in […]
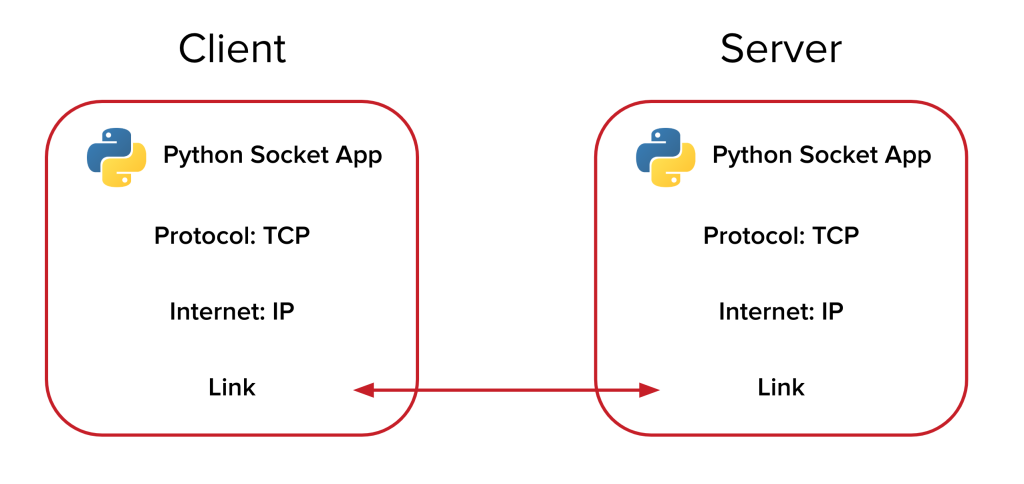
🚨 Building a Malicious Backdoor & C2 Server in Python! 💻🔥
Malicious backdoors and Command & Control (C2) servers are tools commonly employed in cyberattacks to enable […]

🚨 Building a Malicious Backdoor & C2 Server in Python! 💻🔥
Malicious backdoors and Command & Control (C2) servers are tools commonly employed in cyberattacks to enable […]
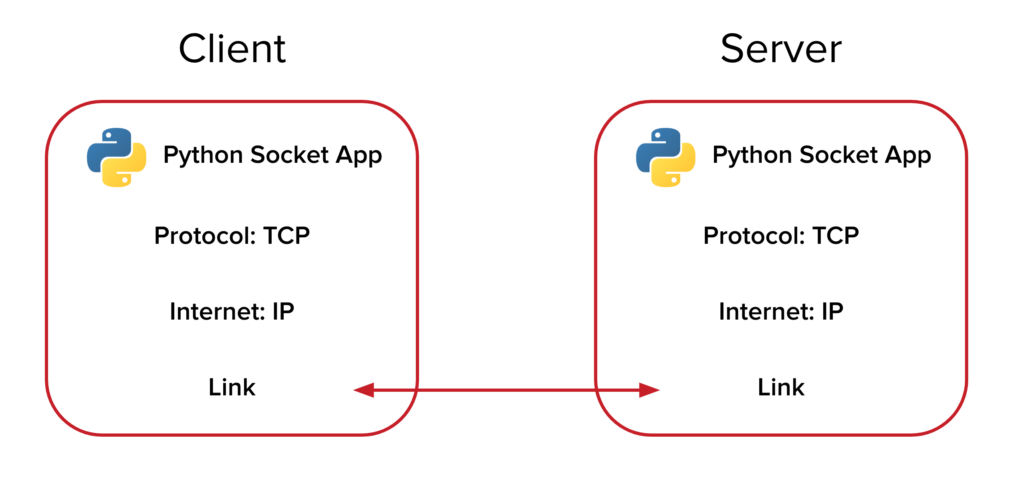
Building a Malicious Backdoor & C2 Server in Python
Backdoors and Command & Control (C2) servers are some of the tools used in cyberattacks to […]
Mastering Linux: The Top Commands Every Server Administrator Should Know
As a Linux system administrator, you must understand how to configure and manage your Linux servers […]

Microsoft files lawsuit against LLMjacking gang that bypassed AI safeguards
Microsoft has filed a civil lawsuit against an international gang of cybercriminals that exploited stolen credentials […]
