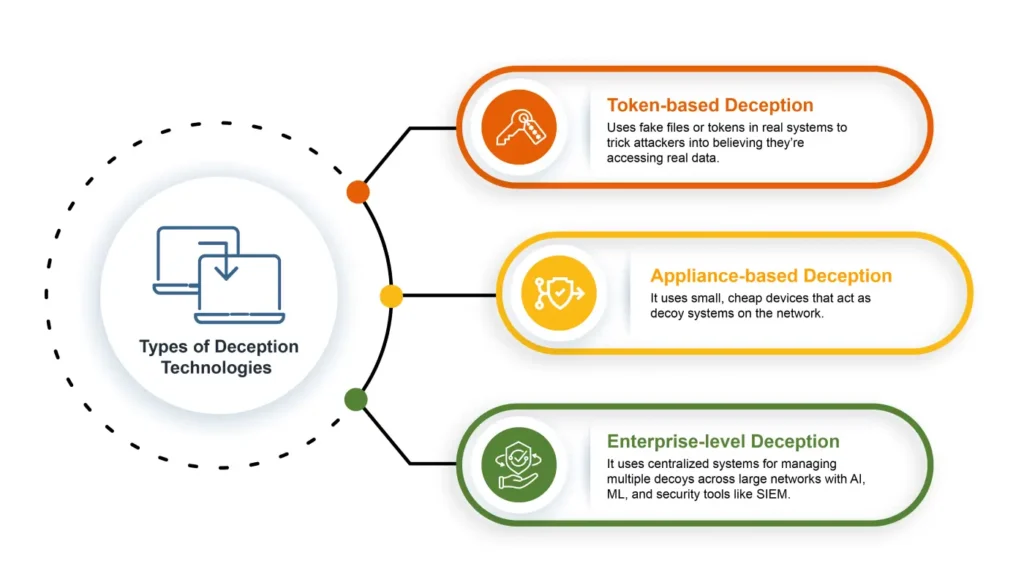
Deception vs. Traditional Threat Detection: A Detailed Comparison
Trapping attackers and catching them red-handed before they even enter your network is the ultimate defense […]
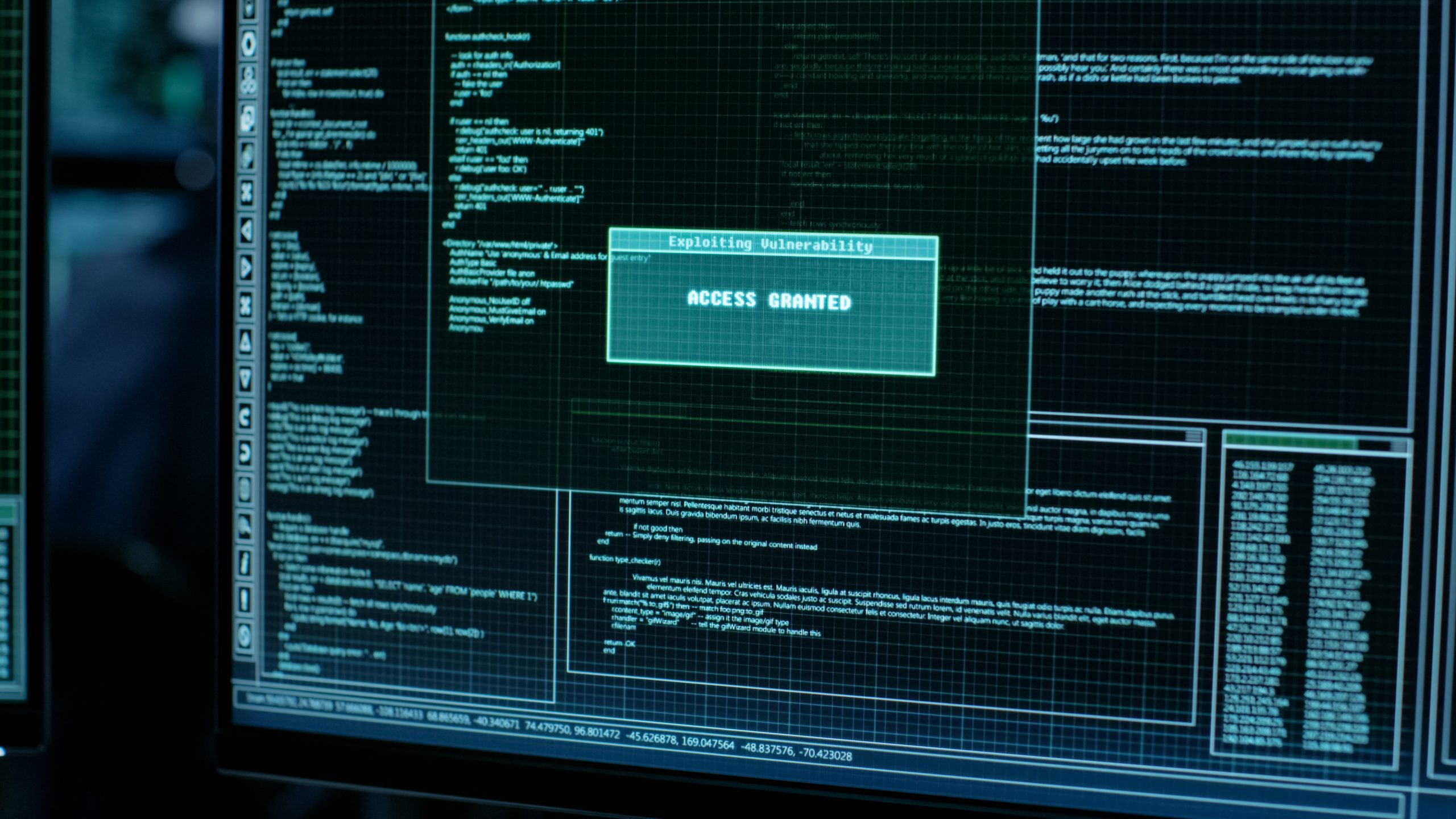
Tomcat PUT to active abuse as Apache deals with critical RCE flaw
Apache Software’s open-source web container for handling Java-based web applications, Tomcat, is under active attacks through […]

Alphabet in advanced talks to buy Israel’s Wiz, expanding cloud security reach
Alphabet is in advanced negotiations to acquire Israeli cybersecurity firm Wiz for over $30 billion, a […]

Attack time frames are shrinking rapidly. Here’s how cyber teams can cope
Times are tough for cyber pros, quite literally. Two common malware time scale metrics — dwell […]

Not all cuts are equal: Security budget choices disproportionately impact risk
Inadequate security budgets to support technology upgrades, security training, and business initiatives have a disproportionate impact […]

5 Top Cybersecurity-Zertifizierungen: So pushen Sie Ihre CISO-Karriere
Lesen Sie, welche Cybersecurity-Zertifizierungen Ihrer Karriere als CISO einen Schub geben. Foto: Elnur – shutterstock.com Zertifizierungen […]

White House exempts cyber pros from mass layoffs; Judge reinstates CISA firings
The tide may be turning for US federal cybersecurity professionals who have faced job cuts or […]

Thousands of open source projects at risk from hack of GitHub Actions tool
App development teams who use a popular utility in the GitHub Actions continuous integration and continuous […]
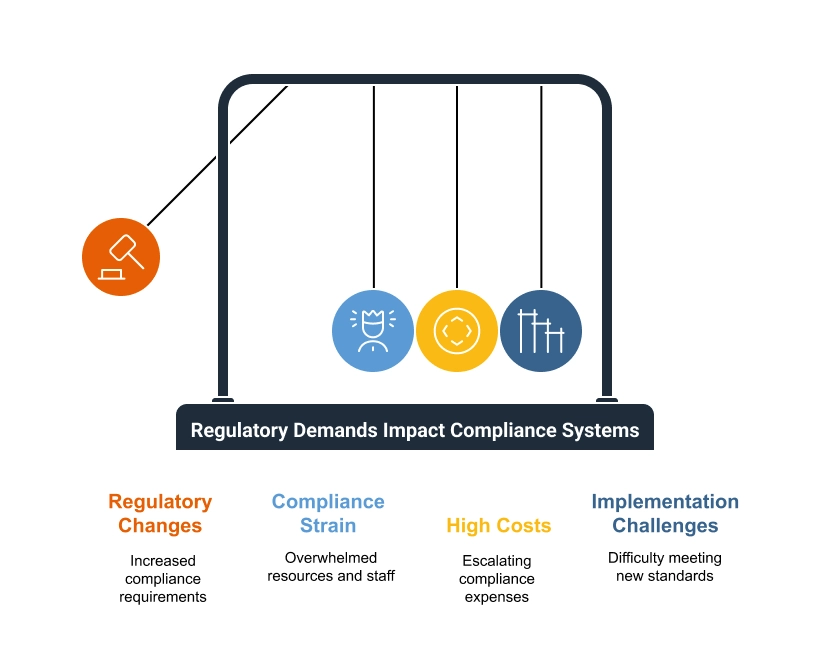
Building a Strong Security Approach for Financial Institutions
The security landscape for financial institutions has changed dramatically in recent years. Banks and credit unions […]
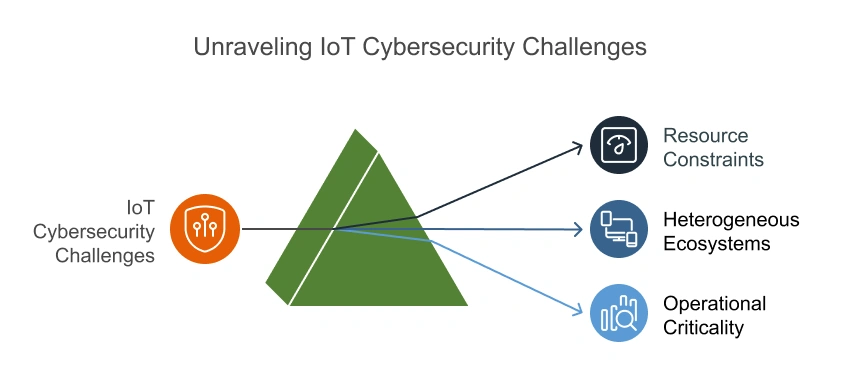
Anomaly Detection in IoT Networks: Securing the Unseen Perimeter
The explosion of Internet of Things (IoT) devices has transformed our world in countless ways, from […]
