Trapping attackers and catching them red-handed before they even enter your network is the ultimate defense strategy.
There is no doubt that traditional security systems are efficient in handling threats—but known threats! What if the attacker finds a new and unimaginable way to intrude into your network?
This is where we need deception technology!
Let’s go through both methods and find the differences in detail.
Traditional Security Measures
Check the main traditional threat detection technologies companies use.
Security MeasureFeatures
Firewalls
Filters incoming and outgoing traffic based on security rules.
Blocks known threats and prevents unauthorized access.Antivirus and Antimalware Software
Scans files and programs for known malicious signatures.
Helps prevent common and known malware.Intrusion Detection and Prevention Systems (IDS/IPS)
Monitors network traffic for malicious activity and prevent intrusions.
Detects known attack patterns and monitors network traffic in real time.Encryption
Manages and verifies who can access what in the network.
Prevents unauthorized access based on role and permissions.
Overall, traditional systems work more like a ‘Closed’ sign on a storefront: once it’s up, the threat is stopped immediately. But when you detect the threat and catch the attacker, they change their tactics and find a different way to intrude. Skilled attackers may simply change their IP address and try again. Handling such clever attackers requires advanced technology.
This is where deception technology comes into play.
What Is Deception Technology?
Deception technology involves intentionally misleading attackers by creating false appearances or resources that attract and trap them. The concept is just like a fake military unit placed in a war zone to mislead enemies while protecting their real targets.
This will also help the militant track the movements of enemies and understand their mode of attack without any trouble to the actual target. Similarly, deception-based threat detection not only detects attacks and attackers, it even collects the details like the attacker behavior, IP address, tools used, and tactics. This will be useful for proactive and early threat detection in the future, improving the organization’s security posture.
How Deception Works
Businesses set up fake systems, data, and devices that mimic real ones within the network. These are often referred to as decoys.
Examples include fake files, credentials, or devices such as printers, servers, and IoT devices. These fake systems are made to look vulnerable and attract attackers. When an attacker interacts with them, an alert is triggered, revealing their position and intentions.
Additionally, businesses use breadcrumbs in their deception systems. Breadcrumbs are fake clues—such as files, fake login credentials, or documents—that guide attackers toward the decoys, luring them into engaging with the deceptive resources.
Explore how deception technology can help you:
Improve threat detection and containment.
Tailor deployment to your environment and resources.
Reduce time and effort with automation.
Build an effective detection and response strategy.
Why Deception Is Effective?
The more attackers interact with decoys, the more you can learn and strengthen your defenses.
Integration with Other Security Systems
Flexible Integration
Deception doesn’t replace existing security tools. It can be added to any system (e.g., SIEM, SOAR) to enhance detection and response capabilities.
Collaboration with Other Tools
It connects with other security systems like EDR to improve the accuracy of alerts and responses.
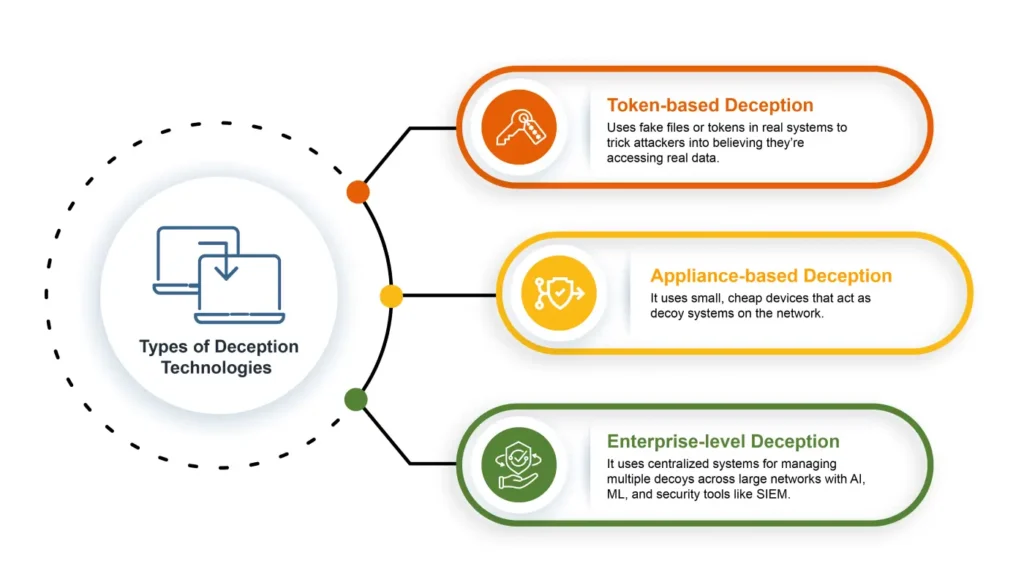
Types of Deception Technologies
Now, let’s get to the main point. Traditional security measures vs. deception!
Traditional security measures vs. deception
AspectTraditional Security MeasuresDeception Technology
Detection SpeedCan be slow, especially with signature-based detection.Detects attacks in real-time as attackers engage with decoys.ApproachReactive: Waits for an attack to happen and then responds.Proactive: Misleads and traps attackers before they cause harm.Effectiveness Against Advanced Persistent Threat (APTs)Struggles to detect advanced, multi-stage threats (APTs).Very effective against APTs, catching attackers early in the attack chain.Cost of DeploymentHigh: Expensive infrastructure and maintenance for tools like firewalls and antivirus.Cost-effective: Lower long-term costs by reducing the need for frequent updates.Resource UseHigh: Consumes significant system resources and personnel time.Low: Lightweight decoys that don’t interfere with regular operations.False PositivesHigh: Often flags legitimate activity as threats.Low: Only malicious behavior triggers alerts.
Benefits of Deception Technology Over Traditional Security Measures
These are the main factors where deception technology can outperform traditional systems:
Early Detection
Deception helps spot attacks early as it traps attackers with fake resources. This reduces dwell time, that is the time attackers spend in the network. This quick detection and prevention help in less damage and fast response, which traditional systems may struggle with.
Accurate Alerts
Tools like firewalls may trigger false positives or miss some threats. The deception technique spots genuine patterns by identifying the real threat actors who engage with decoys. This reduces security teams’ time working on false positive alerts.
Collect Threat Intelligence
Traditional tools often offer limited insights about the attack and attacker, while deception systems gather detailed information about the threat actors. This information includes how they interact with the decoys, their origin, tools, and methods, which can help improve future security strategies and prepare for better responses and advanced threat detection and defense.
Prevent Attacks
Traditional systems often react only after the threat enters the network, but deception tricks attackers with decoys, which slow down the movement and destroy their attacking plans. By learning their attack methods and patterns, companies can further make improvements in their strategies.
Finding a robust deception tool will be the right idea for decision-makers to implement this method of protecting your critical assets, digital systems, and network.
Fidelis Deception®: A Robust Cyber Deception Tool
Fidelis Deception® provides a proactive approach to cybersecurity that detects, deceives, and neutralizes attackers. It traps attackers, alerting cyber defenders quickly.
Here’s how Fidelis Deception® stands out:
Fake Assets/Decoy Traps: These decoys are designed to look like valuable resources, tricking attackers into thinking they’ve found real assets.
Detection Mechanisms: The decoys actively detect adversaries as they attempt to engage with fake systems.
Early Warning System: Fidelis Deception alerts defenders as soon as attackers interact with the decoys, providing early detection.
Reduction of False Positives: High-fidelity alerts ensure that only real cyber threats are detected, minimizing the noise from false alarms.
How Fidelis Deception® Works:
Automatic Deployment of Deception Layers
Ensures that decoys are automatically deployed throughout your network, ensuring comprehensive coverage against attacks.
High-Fidelity Alerts
Ensures only actual threats trigger alerts, reducing false positives and enhancing the accuracy of your defense using advanced detection algorithms.
Active Sandbox Analysis
It analyzes threats in a safe environment, protecting your network and giving insights into the attacker’s methods.
Maintained Business Continuity
Minimizes disruptions even while deceiving attackers and keeps business operations secure.
Threat Protection Capabilities of Fidelis Deception®
Credential Theft Detection
Fidelis deploys decoy credentials to attract attackers based on their search patterns.
Fake credentials help reveal attackers’ motives and methods, enabling a quicker response.
Lateral Movement Detection
Decoys and breadcrumbs are placed in key areas (e.g., Active Directory) to detect unauthorized movements.
Tracks attacker movements before accessing sensitive data.
Deception for Active Directory
Fidelis deploys decoy items in AD to identify suspicious activity.
Actively checks logs for unauthorized activity, allowing quick threat neutralization.
Fidelis speeds up detection from weeks or months to hours or minutes, helping businesses stop attacks early. It also provides custom cybersecurity solutions on-premises and in the cloud, ensuring flexibility and scalability.
Discover how deception technology can help you:
Gain the upper hand in the asymmetry between attackers and defenders.
Improve detection capabilities and limit damage.
Develop a methodical strategy for effective deception.
Integrate cyber deception with robust incident-handling processes.
In Conclusion
Traditional security measures are useful but can’t track complex or unexpected attacks. Robust tools like Fidelis Deception® lure attackers with decoys, revealing their tactics and details to strengthen your security. With fewer false positives, faster response times, and stronger protection, deception technology is essential for enhancing your cybersecurity.
Frequently Ask Questions
How is deception technology different from traditional security?
Traditional security systems react after an attack happens, usually by blocking known threats, while deception technology proactively tricks attackers with decoys and helps in threat hunting and trapping them before they escalate.
What are the main benefits of deception technology?
Can deception technology work with my current security tools?
Yes, deception technology can be integrated with existing security systems like SIEM, EDR, and other security systems.
How does Fidelis Deception® detect and stop attacks?
Fidelis Deception® uses decoys to attract attackers and triggers alerts when they interact with them. It tracks their actions, helping defenders stop threats before they spread.
The post Deception vs. Traditional Threat Detection: A Detailed Comparison appeared first on Fidelis Security.
No Responses