
7 Green Flags to Look for When Choosing a Software QA Company
Choosing the right software QA company isn’t just about ticking boxes—it’s about finding a partner who […]

Governments won’t like this: encrypted messaging between Android and iOS devices coming, says GSMA
Imagine a world of the near future where Android and Apple iOS users can message one […]

Report on ransomware attacks on Fortinet firewalls also reveals possible defenses
A new ransomware gang is quickly exploiting two authentication bypass vulnerabilities in Fortinet firewalls, researchers say. […]
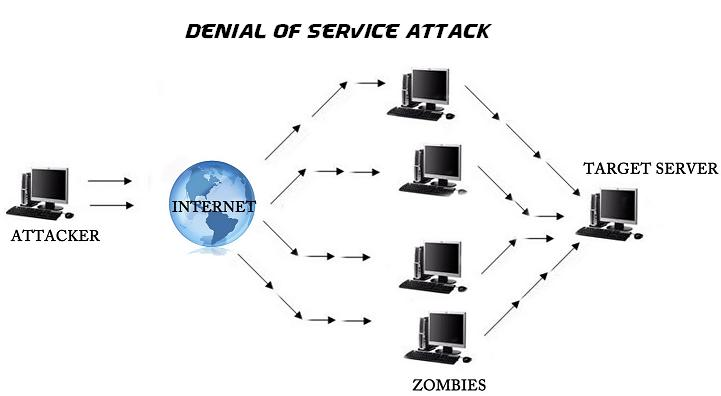
SSH DDoS Attack Simulation Using Python: A Comprehensive Guide
Hey guys! Rocky here. Let’s talk about something wild but super important: DDoS attacks targeting SSH—and […]

SSH DDoS Attack Simulation Using Python: A Comprehensive Guide
Hey guys! 👋 Rocky here. Let’s talk about something wild but super important: DDoS attacks targeting […]

SSH DDoS Attack Simulation Using Python: A Comprehensive Guide
Hey guys! 👋 Rocky here. Let’s talk about something wild but super important: DDoS attacks targeting […]

Europäische Unternehmen haben keinen (Krisen)-Plan
Eine aktuelle Studie zeigt Defizite im Risikomanagement von Unternehmen auf beiden Seiten des Atlantiks. rawf8 – […]

Cybersecurity in Kommunen: Eigeninitiative gefragt
width=”2480″ height=”1395″ sizes=”(max-width: 2480px) 100vw, 2480px”> Deutsche Kommunen erscheinen in Sachen Cybersicherheit eine leichte Beute zu […]
Protecting Data Across Industries: Best Practices for Compliance and Security
Data is the backbone of modern enterprises, fueling strategic decisions, operational efficiencies, and customer experiences. However, […]

Fast 1 Million Geschäfts- und Privat-PCs kompromittiert
Ein Bericht von Microsoft zeigt, wie wichtig es für CISOs ist, das Sicherheitsbewusstsein ihrer Mitarbeiter zu […]
