The Ultimate Guide to Transforming Your Old Machine into a VPS Server
Hey guys, Rocky here! 👋 So you’ve got a dusty old laptop or computer taking up […]
The Ultimate Guide to Transforming Your Old Machine into a VPS Server
Hey guys, Rocky here! So you’ve got a dusty old laptop or computer taking up space […]

Building Malware with Python: Writing Ransomware, Keyloggers & Reverse Shells from Scratch
Hey guys, Rocky here! 👋 So you’re curious how malware actually works? Maybe you’re wondering why […]

Building Malware with Python: Writing Ransomware, Keyloggers & Reverse Shells from Scratch
Hey guys, Rocky here! 👋 So you’re curious how malware actually works? Maybe you’re wondering why […]

Building Malware with Python: Writing Ransomware, Keyloggers & Reverse Shells from Scratch
Hey guys, Rocky here! So you’re curious how malware actually works? Maybe you’re wondering why ransomware […]
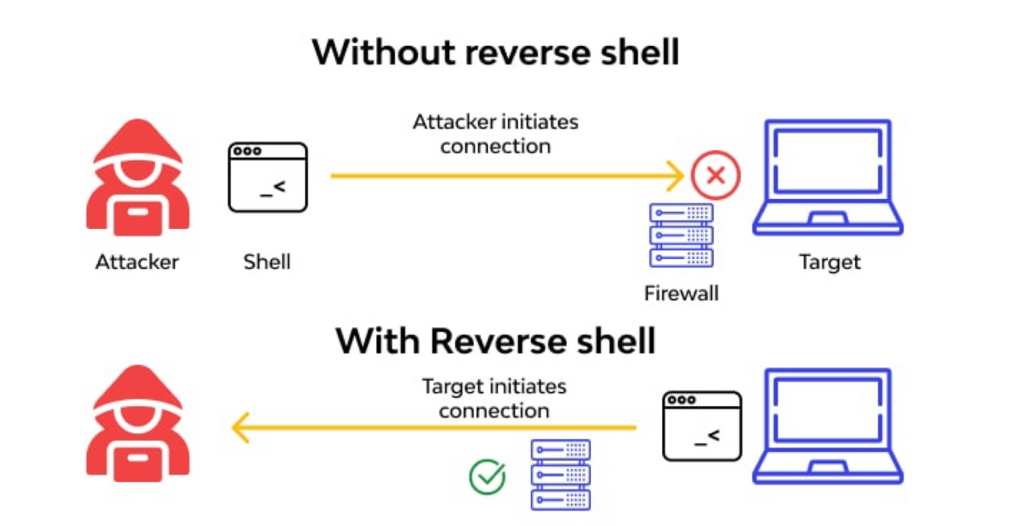
Building a Custom Python Backdoor
Hey guys! 👋 Rocky here. So, you wanna learn how to build a custom backdoor in […]

Building a Custom Python Backdoor
Hey guys! 👋 Rocky here. So, you wanna learn how to build a custom backdoor in […]

Building a Custom Python Backdoor
Hey guys! Rocky here. So, you wanna learn how to build a custom backdoor in Python? […]
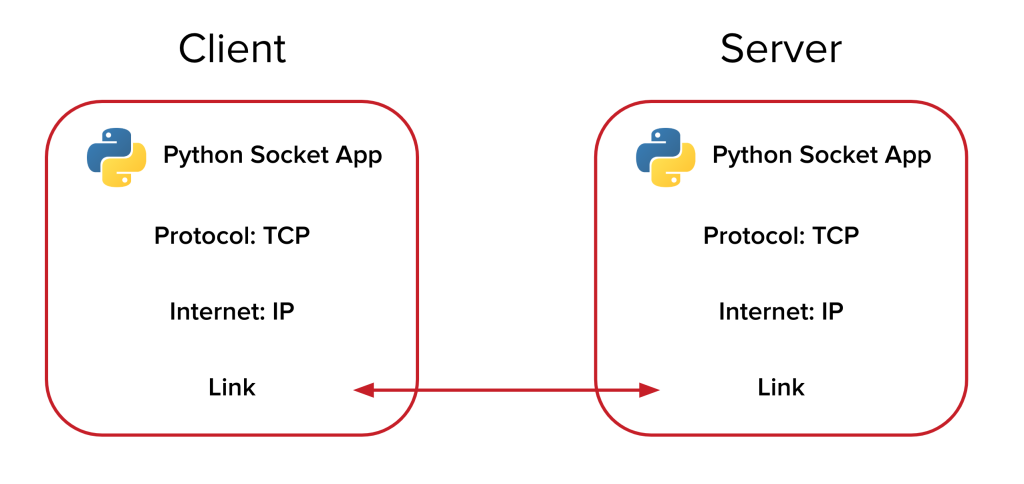
🚨 Building a Malicious Backdoor & C2 Server in Python! 💻🔥
Malicious backdoors and Command & Control (C2) servers are tools commonly employed in cyberattacks to enable […]

🚨 Building a Malicious Backdoor & C2 Server in Python! 💻🔥
Malicious backdoors and Command & Control (C2) servers are tools commonly employed in cyberattacks to enable […]