Exploring the Benefits of Payment HSM: Enhancing Security in a Cashless World
In today’s digital era, cashless transactions have become the norm. With the convenience of online payments, […]
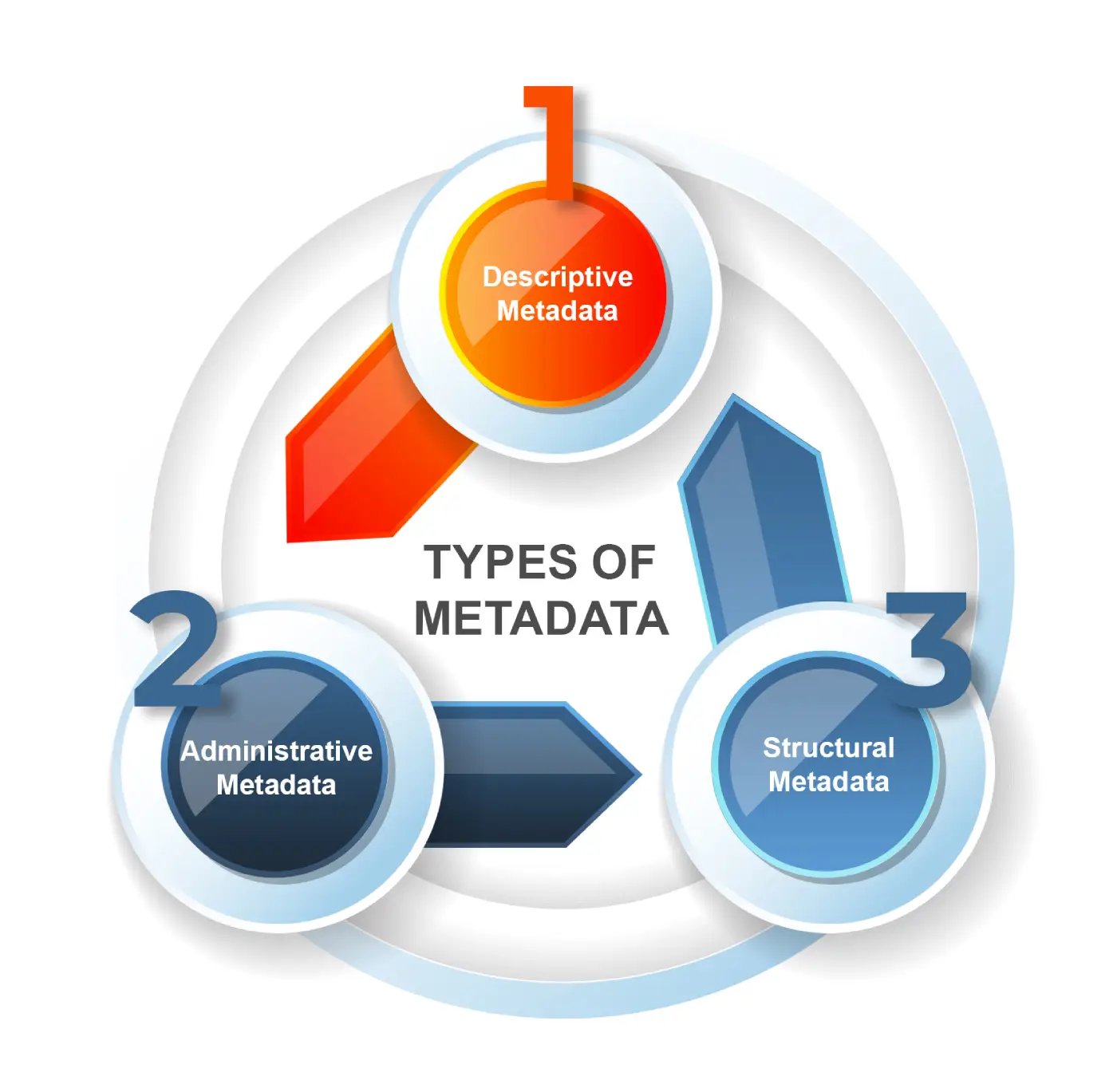
Using Metadata for Proactive Threat Hunting
Organizations want to stay on top of cyber threats and detect them even before they occur. […]

Sicherheitsrisiko: Microsoft entfernt VSCode-Erweiterungen
Forscher haben herausgefunden, dass zwei VSCode-Erweiterungen mit Schadcode infiziert sind. VZ_Art – Shutterstock.com Die IT-Forscher Amit […]
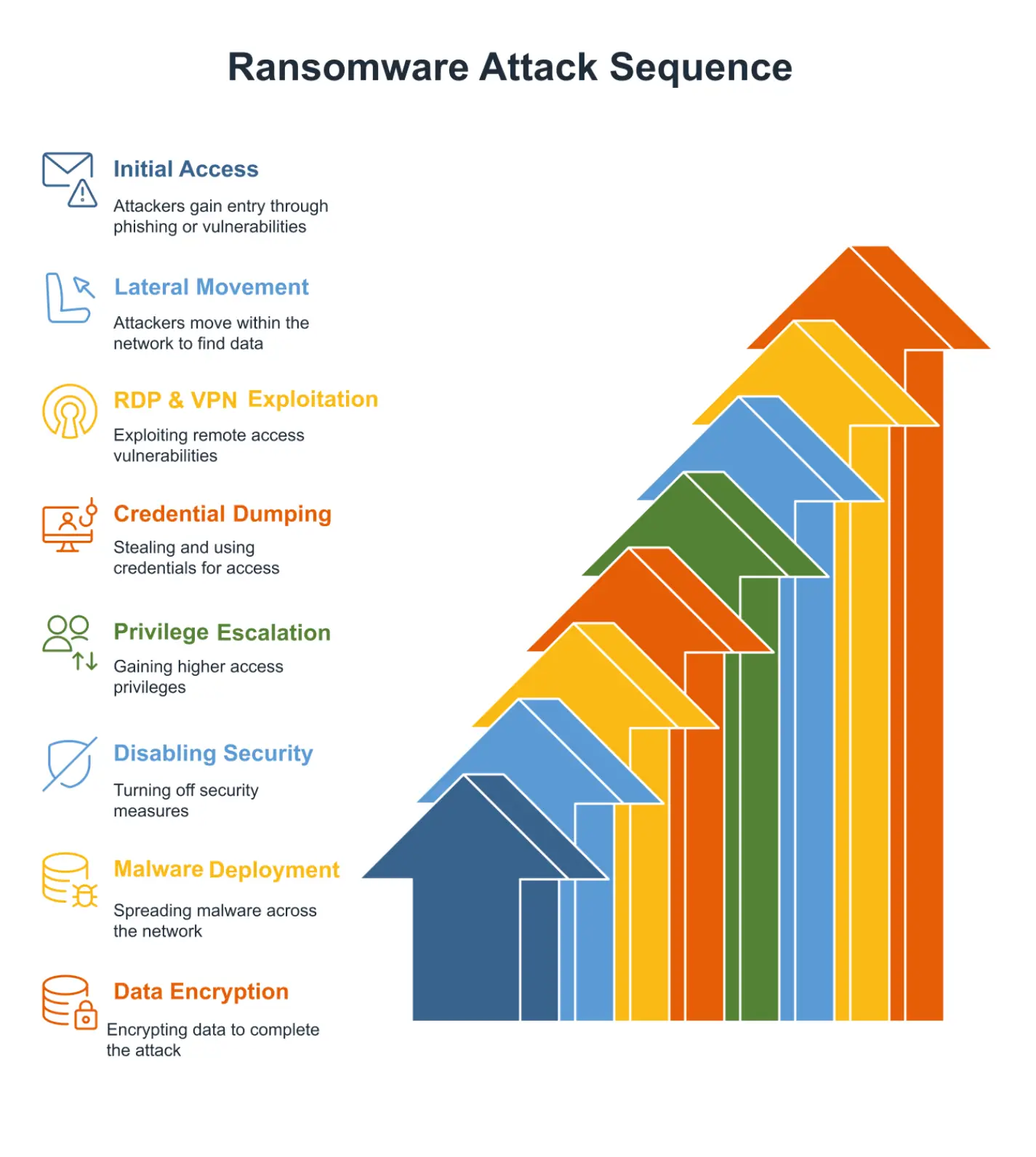
NDR for Ransomware Attack: How Tools Defend Against It
“It takes 18 days on average for organizations to recover from a ransomware attack” – IBM […]

Critical Microsoft Partner Center vulnerability under attack, CISA warns
A critical vulnerability in Microsoft’s Partner Center platform is under attack, enabling unauthenticated attackers to escalate […]

Orange Group von Datenleck betroffen
Die Orange Group wurde von einer Ransomware-Attacke getroffen. JeanLucIchard – Shutterstock.com Ein Mitglied der Ransomware-Bande HellCat […]

So You Want to Be a Hacker: 2025 Edition
Growing up in the 90s inundated me with images of hackers portrayed as mysterious, hoodie-clad figures […]

How to configure OAuth in Microsoft 365 Defender and keep your cloud secure
Cloud authentication provides so many advantages in business. It can allow your users to seamlessly authenticate […]

5 things to know about ransomware threats in 2025
Ransomware attacks continue to be one of the most significant cybersecurity threats organizations and cybersecurity leaders […]