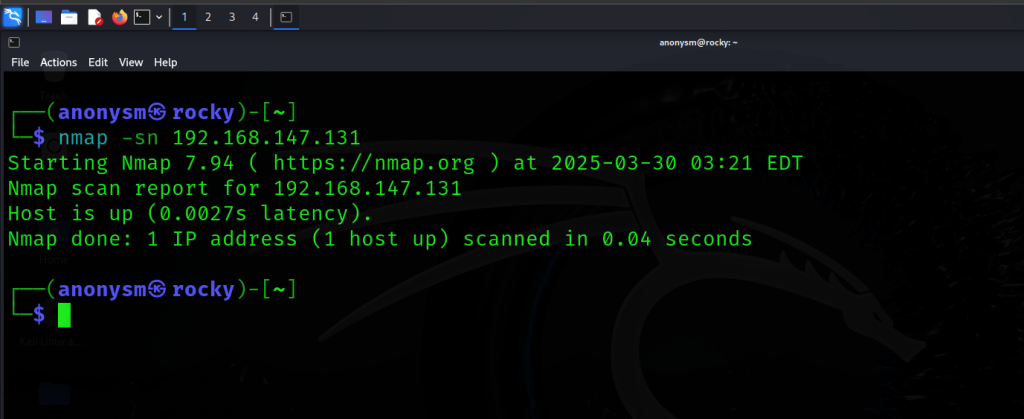
The Ultimate Nmap Guide: Master Network Scanning, Scripting, and Security Audits
Hey guys, Rocky here! 👋 Welcome to your ultimate guide to Nmap—the Swiss Army knife of […]

The Ultimate Nmap Guide: Master Network Scanning, Scripting, and Security Audits
Hey guys, Rocky here! 👋 Welcome to your ultimate guide to Nmap—the Swiss Army knife of […]

The Ultimate Nmap Guide: Master Network Scanning, Scripting, and Security Audits
Hey guys, Rocky here! Welcome to your ultimate guide to Nmap—the Swiss Army knife of networking […]
Hacking like a Pro: The Ultimate Guide to Penetration Testing with Kali Linux Tools in 2025
Penetration testing is an essential part of any comprehensive security program, and Kali Linux is a […]
Hacking like a Pro: The Ultimate Guide to Penetration Testing with Kali Linux Tools in 2025
Penetration testing is an essential part of any comprehensive security program, and Kali Linux is a […]
Hacking like a Pro: The Ultimate Guide to Penetration Testing with Kali Linux Tools in 2025
Penetration testing is an essential part of any comprehensive security program, and Kali Linux is a […]
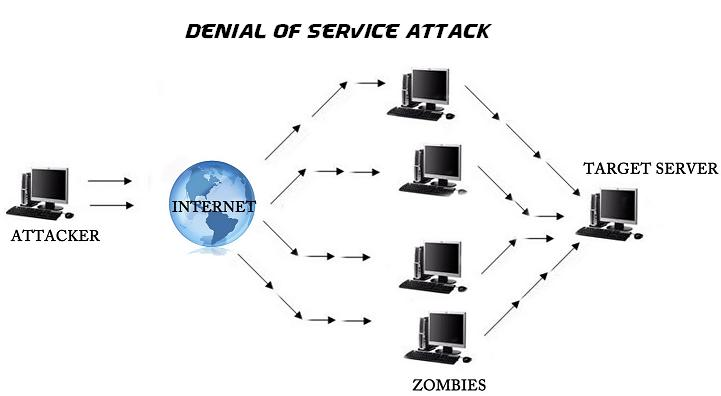
SSH DDoS Attack Simulation Using Python: A Comprehensive Guide
Hey guys! 👋 Rocky here. Let’s talk about something wild but super important: DDoS attacks targeting […]

SSH DDoS Attack Simulation Using Python: A Comprehensive Guide
Hey guys! 👋 Rocky here. Let’s talk about something wild but super important: DDoS attacks targeting […]

SSH DDoS Attack Simulation Using Python: A Comprehensive Guide
Hey guys! Rocky here. Let’s talk about something wild but super important: DDoS attacks targeting SSH—and […]
The Ultimate Guide to Transforming Your Old Machine into a VPS Server
Hey guys, Rocky here! 👋 So you’ve got a dusty old laptop or computer taking up […]