
Gladinet servers file-sharing servers allow remote code execution
Enterprises relying on Gladinet’s file-sharing services are faced with another round of zero-day patching, this time […]

Zero-Trust-Umsetzung: Die richtige Kommunikation zählt
Möchten CISOs neue Strategien wie Zero Trust einführen, ist die richtige Kommunikation entscheidend. HZ Creations – […]

Cyberangriff auf Rathaus: Hacker veröffentlichen Daten im Darknet
Cyberkriminelle haben Daten bei der Gemeindeverwaltung Untereisesheim gestohlen und im Darknet veröffentlicht. BeeBright – shutterstock.com Mitte […]
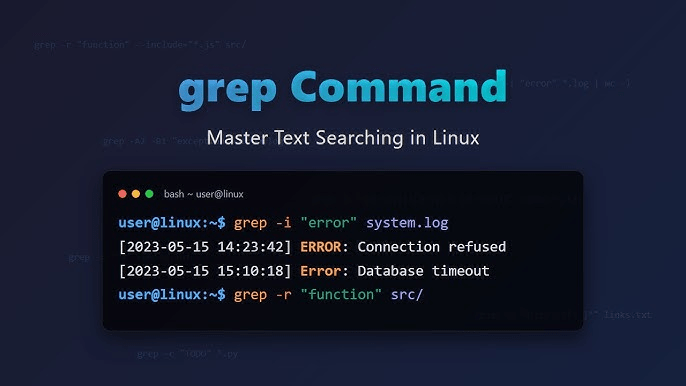
10 Essential Linux Commands to Boost Productivity and Save Hours Weekly
Ever feel like you’re doing the same boring computer tasks over and over? Clicking through folders […]

How to simplify enterprise cybersecurity through effective identity management
Identifying and securing ownership of assets can be a challenging task. In addition to multifactor authentication, […]

OpenAI expands ‘defense in depth’ security to stop hackers using its AI models to launch cyberattacks
OpenAI is preparing for the possibility that threat groups will try to abuse its increasingly powerful […]

Meet ConsentFix, a new twist on the ClickFix phishing attack
A new variation of the ClickFix scam tries to get around phishing defenses by capturing an […]

Wie im Netz gezielt manipuliert wird
Cyberkriminelle nutzen SIM-Karten vom Graumarkt für virtuelle Bot-Armeen. K2LStudio – shutterstock.com Ein umfangreicher internationaler Graumarkt mit […]

SAML authentication broken almost beyond repair
Researchers have uncovered fresh techniques for breaking SAML-based authentication, further undermining the security assurances offered by […]

Battering RAM hardware hack breaks secure CPU enclaves
Confidential computing, powered by hardware technologies such as Intel SGX (Software Guard Extensions) and AMD SEV […]
