
Volume of attacks on network devices shows need to replace end of life devices quickly
Two of the top three vulnerabilities that threat actors tried to leverage in 2024 were in […]

Hackerangriff auf MAN-Tochter
Cyberkriminelle haben offenbar die Systeme einer MAN-Tochter geknackt. Die Zentrale in München ist nach eigenen Angaben […]

Hacker wollten Arbeitslosengeld ergaunern
width=”1936″ height=”1089″ sizes=”(max-width: 1936px) 100vw, 1936px”>Die Bundesagentur hat Strafanzeige gestellt. Bundesagentur für Arbeit Bei der Bundesagentur […]

How CISOs can balance business continuity with other responsibilities
Cyber incidents, especially ransomware, are changing the way businesses assess risk and resiliency. As a result, […]

The CSO guide to top security conferences
There is nothing like attending a face-to-face event for career networking and knowledge gathering, and we […]

Authentifizierungslösungen: 10 Passwordless-Optionen für Unternehmen
Um Passwörter hinter sich zu lassen, gibt es bessere Lösungen. Wir zeigen Ihnen zehn. Foto: Raffi […]
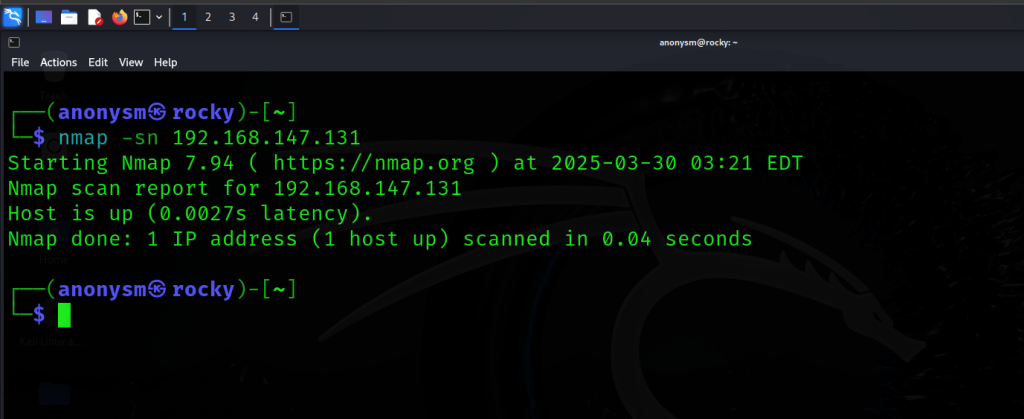
The Ultimate Nmap Guide: Master Network Scanning, Scripting, and Security Audits
Hey guys, Rocky here! Welcome to your ultimate guide to Nmap—the Swiss Army knife of networking […]

The Ultimate Nmap Guide: Master Network Scanning, Scripting, and Security Audits
Hey guys, Rocky here! 👋 Welcome to your ultimate guide to Nmap—the Swiss Army knife of […]

The Ultimate Nmap Guide: Master Network Scanning, Scripting, and Security Audits
Hey guys, Rocky here! 👋 Welcome to your ultimate guide to Nmap—the Swiss Army knife of […]
The Digital Personal Data Protection (DPDP) Act 2023: Key Challenges and Compliance Framework
The Digital Personal Data Protection Act 2023 (DPDP Act) marks a transformative shift in India’s data […]
