Malware continues to evolve with greater sophistication. Sandbox malware analysis offers a secure testing ground to detect and study potential threats before they impact production systems. According to MarketWatch, the network sandbox market’s growth reflects this technology’s rising importance, with projections reaching $5.1B by 2025. Advanced malware presents new challenges because it can now detect sandbox environments during analysis.
This piece dives into sandbox analysis fundamentals and their role in cybersecurity. You’ll learn about its main benefits for detecting zero-day exploits and advanced persistent threats. We’ll also get into the latest methods that help overcome sandbox evasion tactics and show you how companies can build stronger security through effective sandboxing solutions.
What is Sandbox Analysis
Sandbox analysis is a vital cybersecurity technique that creates an isolated, controlled environment to safely run and get into potentially malicious code. Picture it as a digital quarantine area where you can open and analyze suspicious files without damaging your actual systems or network.
The core idea behind sandbox malware analysis is simple yet powerful. It contains potentially harmful code in a virtual space that mirrors a real operating system and watches malware behavior to detect malicious intent. This method helps cybersecurity professionals learn about how malware works without putting production environments at risk.
Security teams monitor these behaviors during sandbox analysis for malware detection:
Network communication patterns File system modifications Registry changes Memory usage patterns System call activities
This behavioral monitoring shows what malware’s true intentions and methods are. To name just one example, sandbox analysis environments can reveal how a piece of malware works, what vulnerabilities it targets, and its persistence mechanisms.
Sandboxing’s value shines when dealing with zero-day threats – unknown malware that bypasses traditional signature-based detection methods. By focusing on behavior instead of known signatures, sandbox environments can spot new threats before they harm your systems.
Fidelis Security’s Network® solution uses advanced sandbox analysis to provide dynamic malware examination capabilities. Our dynamic approach runs suspicious files in safe environments to capture complete behavioral profiles, which improves detection of sophisticated threats by a lot.
Threats contained in the sandbox become valuable learning opportunities. Security teams study these threats to spot patterns that attackers might use again, which then deepens their commitment to protect against emerging threats.
Key components of effective sandbox environments
A sandbox environment needs several key parts to analyze potential threats and isolate them properly. These systems must keep host systems completely isolated while security teams examine suspicious files thoroughly.
The ability to isolate threats serves as the foundation of any working sandbox. Security teams can safely “detonate” suspicious files that deploy malicious payloads without damaging production environments. Teams can implement this in three main ways:
Complete system emulation – simulating physical hardware including CPU and memory Operating system emulation – emulating the end user’s OS without accurately simulating hardware Virtualization/containerization – using virtual machines or containers for isolated execution
Detection accuracy plays a vital role in the sandbox’s success. The most resilient solutions need these important elements:
The system must support many file formats to analyze executables, DLLs, PDFs, Microsoft Office documents, scripts, archives, and URLs. This flexibility prevents overlooking potential threat vectors.
Fidelis Security’s Network® solution combines these vital sandbox components with advanced behavioral analysis. We analyze malware in environments that match production systems exactly. This ensures accurate detection and captures detailed behavioral data that reveals malware’s true purpose – even with sophisticated threats.
How Sandbox Analysis for Malware Detection Works?
The malware sandbox analysis process uses a clear method to examine suspicious files. We at Fidelis Security have fine-tuned this approach to catch more threats with fewer false alarms. Let me show you how this process works.
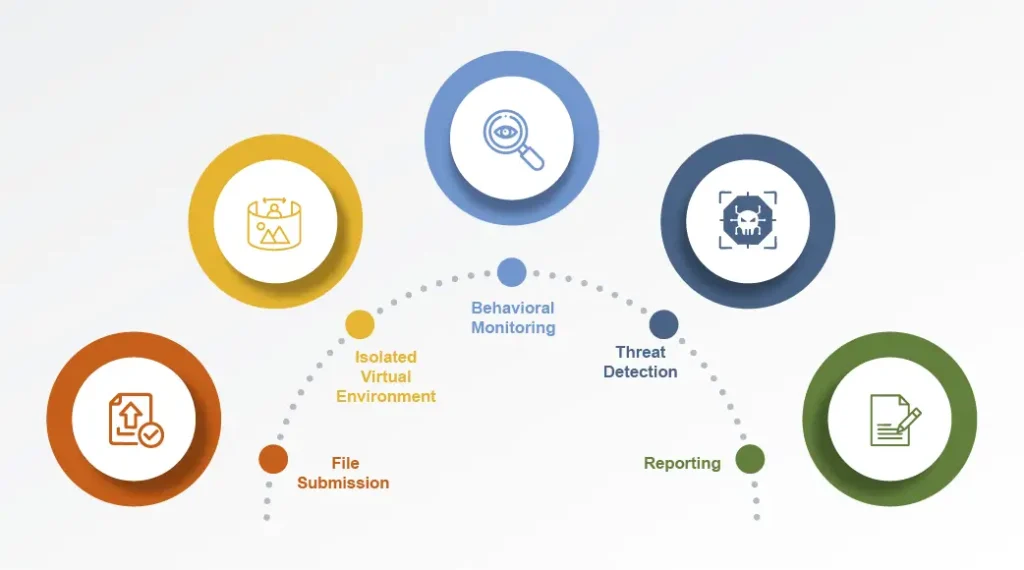
File submission to the sandbox
Suspicious files make their way into the sandbox through different routes. Security tools flag content that looks unusual, and users can also submit files directly. The system gives each file a unique ID and queues it for processing. Fidelis Network® makes this better by pulling files straight from network traffic and analyzing them automatically. This gives us live protection from new threats.
Execution in a virtualized environment
The sandbox builds an isolated virtual environment that looks just like a real system after submission. This setup has operating systems, applications, and network services that appear genuine. The system runs the suspicious file with the right permissions so any malicious code will show itself. The sandbox stays completely isolated to keep production systems safe.
Behavior monitoring (e.g., network activity, file changes, registry modifications)
The sandbox watches the file’s behavior in several ways as it runs:
Network communications – tracks connection attempts, DNS queries, and data transfers
File system interactions – records created, modified, or deleted files
Registry changes – documents modifications to system settings
Process activities – notes process creation, termination, and injection attempts
Memory operations – watches allocation patterns and code injection
Analysis and reporting
The sandbox creates a detailed report after execution finishes. This report shows everything the file did, points out suspicious actions, and gives it a threat score based on malicious indicators. Yes, it is these reports that give security teams useful information to understand attack methods and build proper defenses. Fidelis Network® combines this analysis with its detection system and automatically links findings with other security data. This creates context-rich alerts that help teams respond faster.
How Sandbox Analysis Detects Advanced Threats
Advanced threat detection needs methods that work better than traditional signature-based approaches. Modern cybersecurity practices use sandbox analysis as a pioneering way to identify and neutralize sophisticated threats.
Dynamic vs. static malware analysis techniques
Sandbox environments run suspicious code in controlled conditions to observe actual behavior and interactions through dynamic malware analysis. Static analysis looks at code structure and components without running them. The visibility from dynamic analysis shows how malware works in real-time and reveals evasive techniques that point to malicious intent. Dynamic analysis shows what malware does, while static analysis reveals what it is.
Both approaches work together effectively. Static analysis gives quick results in fractions of a second. Dynamic analysis provides a complete detection system that catches polymorphic threats static methods might miss.
Behavioral analysis in sandbox environments
Sandbox environments monitor these critical system interactions:
System calls and activity monitoring
Network traffic patterns and external communications
Dynamic code execution paths
Memory analysis to detect hidden malicious activities
This all-encompassing approach helps examine how potential threats interact with systems. Advanced sandbox solutions now use AI and machine learning to set normal application behavior baselines. These baselines make it easier to spot subtle changes that point to malicious activity.
Identifying zero-day threats through sandboxing
Zero-day threats create major problems for traditional security approaches because they exploit unknown vulnerabilities. Sandboxing catches these threats by analyzing behavior instead of matching signatures. Sandbox environments spot malicious behavior from brand new threats by watching execution patterns.
Protect your network from the inside out:
Enforce least-privilege access
Block unauthorized devices
Detect and stop hidden threats
Benefits of Sandbox Analysis for Malware Detection
Sandbox analysis for malware detection brings substantial advantages to modern security operations. It addresses major weaknesses in traditional security approaches. The system adds a defensive layer that analyzes actual behavior instead of just relying on known signatures.
Proactive Detection: Security teams can stay ahead of emerging threats through early identification. Sandbox malware analysis helps identify malicious activity before it reaches production environments, unlike reactive approaches that respond after infections occur. Fidelis Security’s sandboxing capabilities automatically analyze suspicious files. This provides immediate protection against evolving attack vectors.
Zero-Day Protection: The greatest benefit of sandbox analysis comes from its power to identify unknown threats. Malware sandbox environments detect unusual behaviors that signal malicious intent, even without existing signatures. This becomes vital when dealing with sophisticated attacks designed to bypass traditional security solutions. The Fidelis Network® platform uses automated malware analysis sandbox technology to spot threats that signature-based systems don’t catch.
Reduced False Positives: Alert fatigue from too many false positives is a common challenge for security teams. Malware analysis sandbox systems make detection more accurate by analyzing file behavior instead of relying on surface-level characteristics. This detailed analysis provides clear evidence of malicious activity. Security analysts can then focus their resources on real threats.
Keyword Integration: Modern sandbox solutions use keyword monitoring to detect suspicious communications. The system tracks command and control traffic, data theft attempts, and other text-based indicators of compromise. Security teams can quickly spot potential threats by monitoring specific terms linked to malicious activity.
Scalability: Sandboxing malware solutions grow as attack surfaces expand. Modern sandbox environments process increasing file volumes without losing detection capabilities. Organizations maintain complete protection despite growing data flows. Fidelis Network® provides expandable sandboxing that adapts to changing traffic patterns while keeping detailed analysis capabilities in distributed environments.
Overcoming Sandbox Evasion Techniques
Malware creators keep finding new ways to hide from sandbox analysis tools. Their sneaky methods make it harder for regular detection systems to work. Security teams need smarter tools to stay ahead of these evolving threats.
Common anti-sandbox strategies used by malware
Modern malware uses several tricks to spot when it’s being analyzed in a sandbox. Many versions look at hardware details to spot differences between real and virtual systems. They check things like CPU cores, disk space, and RAM size. Some malware looks for virtual machine traces or signs that show a sandbox is watching.
Time tricks are another popular way malware tries to escape detection. Bad code often uses these methods:
Long sleep commands that wait out the sandbox Specific dates and times to start running Heavy CPU tasks that create delays
Some malware watches how users behave. It checks mouse clicks, typing patterns, and browser history because automated systems rarely show these human actions. Smart malware creators now stack multiple hiding techniques to make their code harder to catch.
Advanced countermeasures for evasive malware
The best sandbox tools must look like ground environments while hiding their tracking features. Regular platforms like VMware or KVM don’t work well anymore because malware knows how to spot them. Custom-built systems made just for malware analysis work better at staying hidden.
Good sandboxes don’t change the system they’re watching. They skip the hooks and monitoring that malware can spot. Using real system copies instead of basic templates helps because they match what malware expects to see.
Our Fidelis Network® solution at Fidelis Security watches malware from outside the test environment. This keeps the malware from spotting us while we record everything it does. We also speed up system clocks so malware triggers faster during testing.
Automated systems can fake mouse moves and keyboard clicks to trick malware that looks for human users. Memory scanning catches hiding tricks before they start. These tools work together to protect against even the smartest threats.
Conclusion
Sandbox analysis is the life-blood of modern cybersecurity defense. It helps organizations detect and stop advanced threats before they can affect production systems. Our team at Fidelis Security has seen how sandbox environments boost security by a lot in companies of all sizes.
Dynamic analysis, behavioral monitoring, and sophisticated anti-evasion techniques work together to stop today’s evolving threats. This approach works especially well against zero-day exploits and advanced persistent threats that often slip past traditional security measures.
Fidelis Network® takes these capabilities further with automated file extraction, live analysis, and complete behavioral monitoring. The advanced sandbox technology tests suspicious files in environments that match production systems exactly. This ensures accurate threat detection and gives a clear picture of how malware behaves.
Security teams using our Network Detection and Response (NDR) solution get:
Automated threat detection and analysis Live protection against emerging threats Detailed behavioral analysis reports Continuous connection with existing security infrastructure
Companies looking to strengthen their security defenses should think over adding reliable sandbox analysis capabilities. Fidelis Network® provides the complete protection needed to guard critical assets against sophisticated cyber threats.
Uncover and stop what others miss:
Deep packet inspection for full visibility
Real-time threat detection & response
Automated network traffic analysis
The post The Role of Sandbox Analysis in advanced Malware Detection appeared first on Fidelis Security.
No Responses