
The Rise of Autonomous AI Agents: How LLMs Are Transforming the Digital Workforce
In a world increasingly run by artificial intelligence, autonomous AI agents have emerged as one of […]
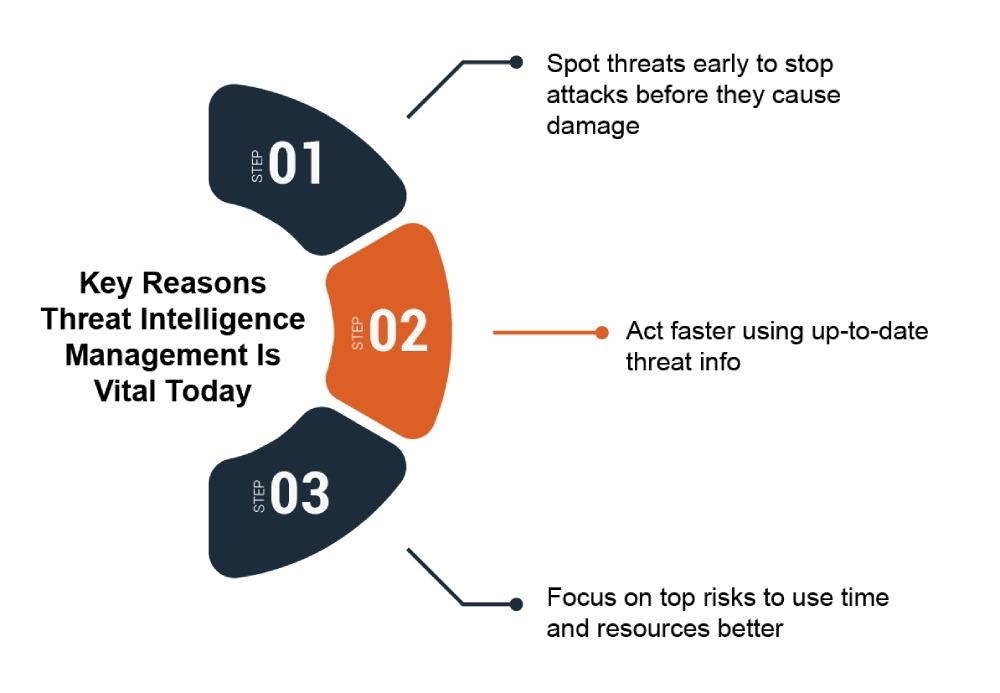
Building a Threat Intelligence Management Strategy with XDR
Is your security team stopping threats before they enter, or just reacting after damage happens? Because […]

How Can Building a Real-Time Asset Inventory Strengthen Your Threat Detection?
Organizations often lack a complete, up-to-date inventory of their IT assets – servers, endpoints, cloud instances, […]

The Rise of 6G Technology – What You Need to Know
Introduction 6G technology is on the horizon, and while 5G networks are still being rolled out, […]
AI and Machine Learning Advancements in 2025
Introduction Artificial Intelligence (AI) and Machine Learning (ML) are no longer just buzzwords—they are shaping the […]

Shifting from Reactive to Proactive Cybersecurity Defense Strategy
In today’s digital landscape, the importance of adopting a proactive approach to cybersecurity, which involves predictive […]

OT Asset Discovery Using XDR: From Blind Spots to Full Visibility
Operational Technology (OT) environments are increasingly under pressure from evolving cyber threats. With digital transformation accelerating […]
How Retrospective Analysis Powers Faster Incident Response
Cyber attackers hide in enterprise networks for 277 days on average before anyone spots them. Once […]
How Can You Master the Incident Response Lifecycle with an XDR Solution?
Today’s advanced threats move faster and cost more—average data breach costs exceed $3.8 million—while defenders struggle […]
SSL Inspection in NDR: Unlocking Threats Hidden in Encrypted Traffic
Did you know that more than 90% of web traffic is now encrypted?1 Encryption makes online […]