Mastering Exploit Development: The Key Skill for Professional Cybersecurity Practitioners
Have you read about hackers breaking into gateway systems and stealing proprietary information, or even shutting […]
Mastering Exploit Development: The Key Skill for Professional Cybersecurity Practitioners
Have you read about hackers breaking into gateway systems and stealing proprietary information, or even shutting […]
Exploit Development Made Easy: Generating Payloads In Metasploit
When developing exploits, creating shellcode is a necessary step. Metasploit provides an easy way to generate […]
Exploit Development Made Easy: Generating Payloads In Metasploit
When developing exploits, creating shellcode is a necessary step. Metasploit provides an easy way to generate […]
Exploit Development Made Easy: Generating Payloads In Metasploit
When developing exploits, creating shellcode is a necessary step. Metasploit provides an easy way to generate […]
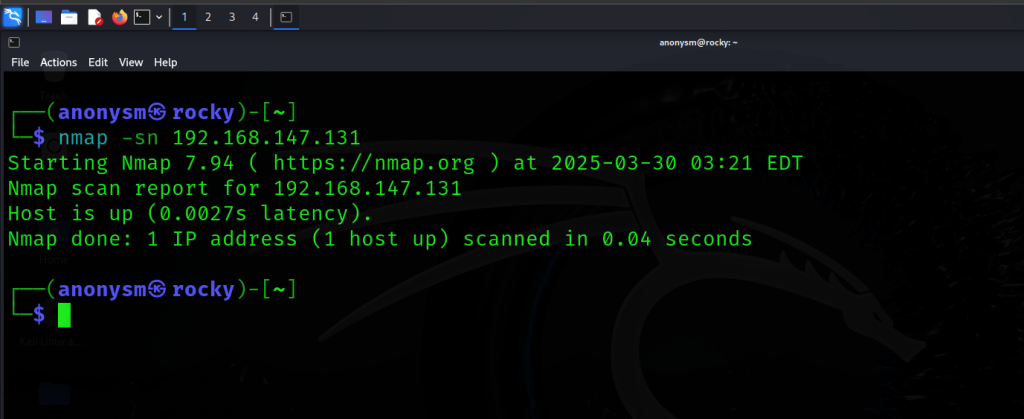
The Ultimate Nmap Guide: Master Network Scanning, Scripting, and Security Audits
Hey guys, Rocky here! 👋 Welcome to your ultimate guide to Nmap—the Swiss Army knife of […]

The Ultimate Nmap Guide: Master Network Scanning, Scripting, and Security Audits
Hey guys, Rocky here! 👋 Welcome to your ultimate guide to Nmap—the Swiss Army knife of […]

The Ultimate Nmap Guide: Master Network Scanning, Scripting, and Security Audits
Hey guys, Rocky here! Welcome to your ultimate guide to Nmap—the Swiss Army knife of networking […]
Hacking like a Pro: The Ultimate Guide to Penetration Testing with Kali Linux Tools in 2025
Penetration testing is an essential part of any comprehensive security program, and Kali Linux is a […]
Hacking like a Pro: The Ultimate Guide to Penetration Testing with Kali Linux Tools in 2025
Penetration testing is an essential part of any comprehensive security program, and Kali Linux is a […]