
How to hack a website with Metasploit
Normally, a penetration tester or hacker uses Metasploit to exploit vulnerable services in a target server […]
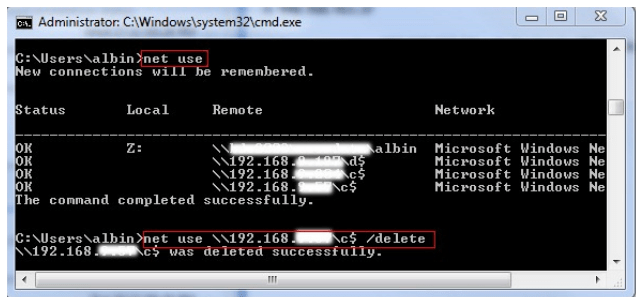
Hunt Evil Your Practical Guide to Threat Hunting – Part 2
As we discussed in the Part 1 , adversaries will come in many forms and will […]
Hunt Evil Your Practical Guide to Threat Hunting – Part 1
You might have heard a lot of buzz around this topic of “Threat Hunting” and want […]
New Front in Cyber Espionage: Chinese Hackers and AI Agents Target Global Cloud and Telecom Infrastructure
A perfect storm is brewing in cyberspace as sophisticated Chinese state-sponsored actors escalate attacks on cloud […]
AI Hacking Teams Now Autonomously Exploit “Zero-Day” Vulnerabilities, Research Reveals
A groundbreaking new study demonstrates that teams of LLM agents can find and exploit previously unknown […]
Level Up Your SOC Skills: A Deep Dive into The SOC Playbook
In today’s world, cyber threats are everywhere — and they’re getting smarter every day. That’s where […]
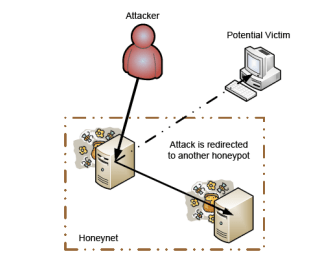
A Practical Guide to Honeypots
In this section, we describe Network Intrusion Detection Systems (IDS)—the traditional approach to network security.We also […]
Python for Cybersecurity: Practical Applications and Beginner Projects
Python has become one of the most popular programming languages in the world—and it’s a favorite […]
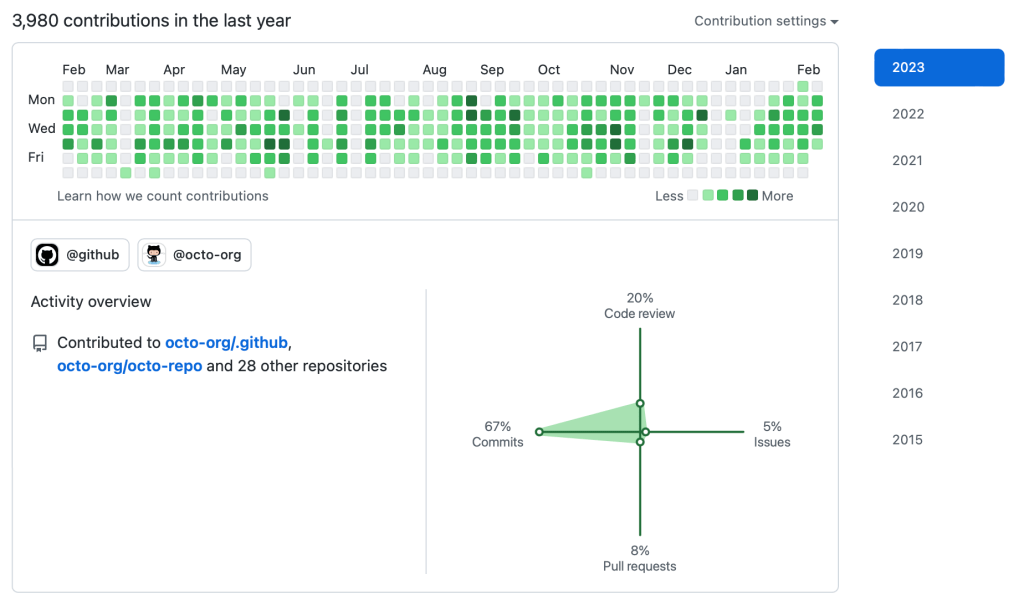
GitHub Recon: The Underrated Technique to Discover High-Impact Leaks in Bug Bounty
When it comes to bug bounty hunting or red teaming, most folks start with the usual […]
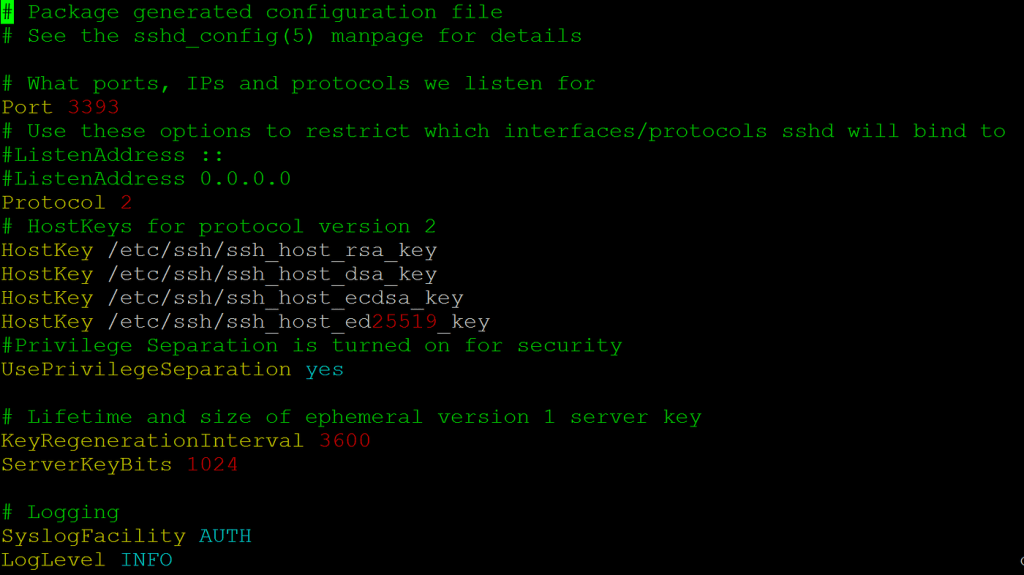
How to Make a Professional Honeypot to Defend Your Network
In cybersecurity, a honeypot isn’t a jar of honey – it’s a decoy system designed to […]