
Why identity recovery is now central to cyber resilience
Ransomware has permanently changed how security leaders think about risk. Verizon’s 2025 Data Breach Investigations Report […]

Unplug to Recharge: 5 Digital Detox Tips for Better Mental Health in 2026 🧘♂️✨
Think back to the last time you sat in silence for ten minutes—no phone, no tablet, […]

Finding Your Zen: The Best Meditation Apps to Quiet the Noise in 2026 🧘♂️✨
In a world that seems to be moving at 100 miles per hour, finding a moment […]

The Freedom Revolution: Navigating the Best Freelancing Platforms in 2026 🌍✨
The traditional 9-to-5 is no longer the only path to a successful career. We are living […]

The Digital Pocket: Why Best Loan Apps in India Are Your New Best Friends 💸
Remember the days when getting a loan meant standing in endless bank queues, wrestling with a […]
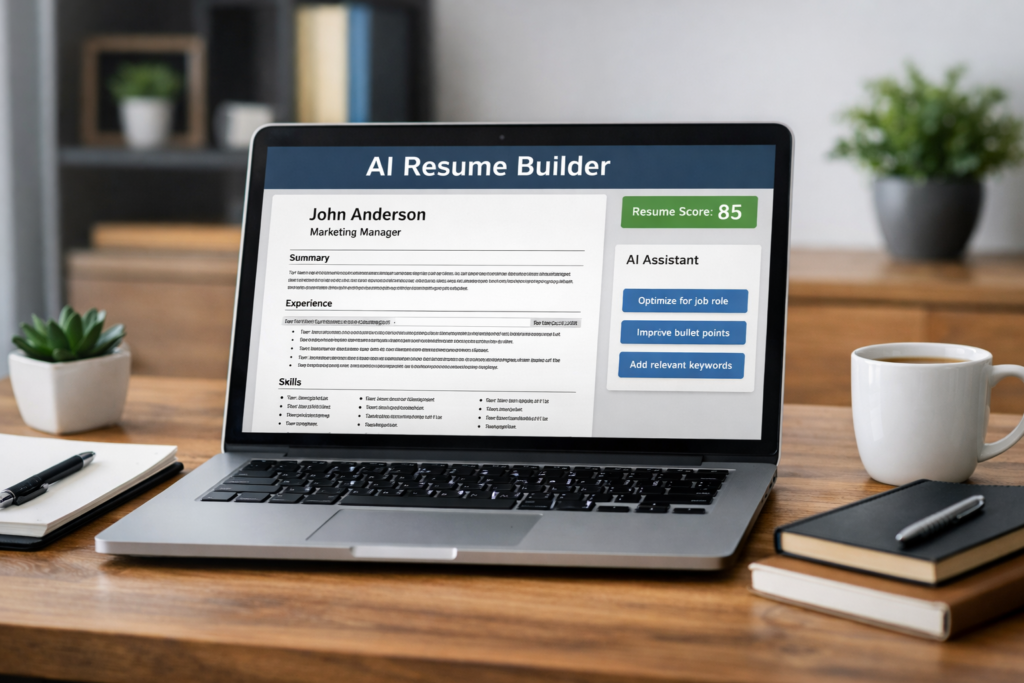
The Future is Now: Unlocking Your Potential with the Best AI Resume Builders 🚀
Let’s face it, crafting a resume can feel like an archaeological dig – sifting through old […]

‘Dead’ Outlook add-in hijacked to phish 4,000 Microsoft Office Store users
A blind spot in Microsoft’s app and add-in marketplace security allowed an eagle-eyed hacker to hijack […]

Neue Warn-App für Cybervorfälle gestartet
Die neue CYROS-App verknüpft Sicherheitswarnungen von Behörden und Fachquellen, um über Cybersicherheitsvorfälle zu informieren. Rawat Yapathanasap […]

Phishing campaign chains old Office flaw with fileless XWorm RAT to evade detection
Fortinet researchers have disclosed a new phishing campaign delivering the commercially available XWorm malware, chaining a […]

Palo Alto closes privileged access gap with $25B CyberArk acquisition
Cybersecurity company Palo Alto Networks has completed its $25 billion acquisition of Israel-based identity security firm […]
