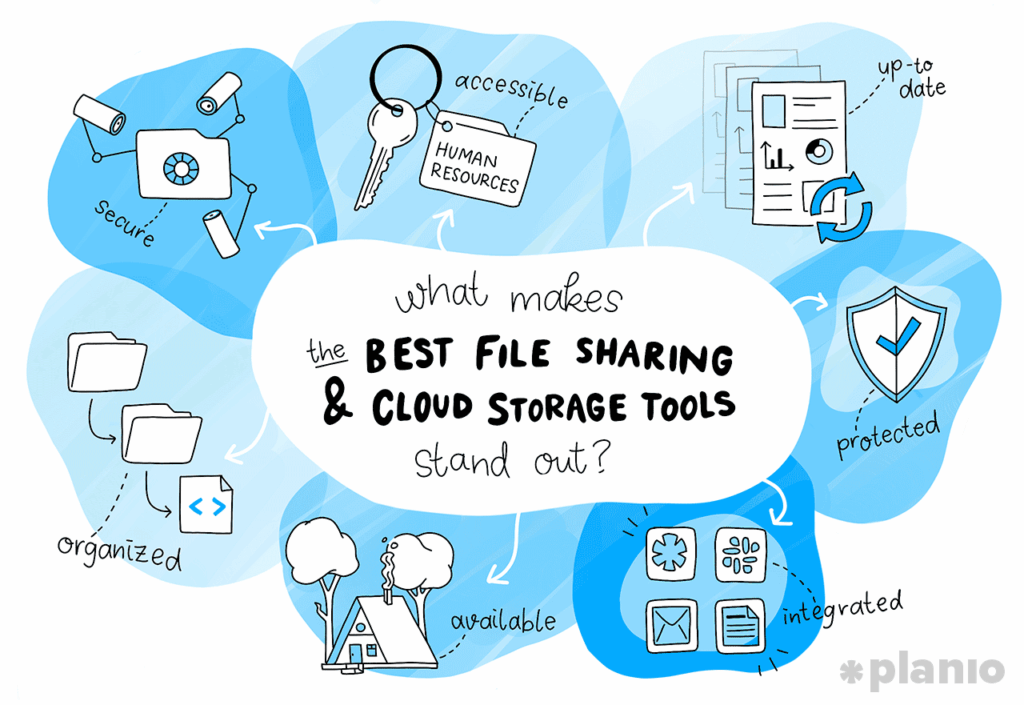
The Digital Handshake: Best File Sharing Apps for Seamless Collaboration
Remember the days of carrying around a physical USB drive like it was a sacred relic? […]

Win the Morning, Win the Day: The Ultimate Daily Morning Routine for Success
We’ve all been there: the alarm blares at 7:00 AM, you hit snooze three times, and […]

North Korean actors blend ClickFix with new macOS backdoors in Crypto campaign
A financially motivated threat actor tracked as UNC1609 is using a ClickFix-style social engineering campaign to […]

EU clears Google’s $32B Wiz acquisition, intensifying cloud security competition
Google has secured unconditional EU antitrust approval for its $32 billion acquisition of cloud security firm […]

The hard part of purple teaming starts after detection
In my recent articles for CSO, I’ve talked about the limits of current SOC models and […]

CISOs must separate signal from noise as CVE volume soars
In 2026, the cybersecurity industry is expected to cross a threshold it has never reached before: […]

Vorgetäuschte PDFs bergen neue Gefahren
loading=”lazy” width=”400px”>Cyberkriminelle verschicken ihre Malware als PDF-Dateien getarnt. IDG Der Security-Anbieter Malwarebytes hat kürzlich vor einer […]

Der Kaufratgeber für Breach & Attack Simulation Tools
Breach & Attack Simulation Tools geben Aufschluss darüber, wie gut (oder schlecht) Ihre Sicherheitskontrollen funktionieren. Roman […]

February 2026 Patch Tuesday: Six new and actively exploited Microsoft vulnerabilities addressed
Microsoft highlighted six new and actively exploited vulnerabilities among the 60 fixes issued in today’s February […]

BeyondTrust fixes critical RCE flaw in remote access tools
Companies using self-hosted versions of BeyondTrust Remote Support (RS) or Privileged Remote Access (PRA) should deploy […]
