The Business Case for Investing in Cybersecurity is Now
In the digitalized, hyper connected economy that the modern world has become, cybersecurity is no longer […]

SonicWall VPNs face a breach of their own after the September cloud-backup fallout
Just weeks after SonicWall disclosed an incident that exposed data from its MySonicWall cloud backup platform, […]

Oracle issues second emergency patch for E-Business Suite in two weeks
Oracle has issued its second emergency security update in less than two weeks for its E-Business […]

Vom CISO zum Chief Risk Architect
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2666021407.jpg?quality=50&strip=all 7000w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2666021407.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2666021407.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2666021407.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2666021407.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2666021407.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2666021407.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2666021407.jpg?resize=150%2C84&quality=50&strip=all 150w, […]

CISOs must rethink the tabletop, as 57% of incidents have never been rehearsed
Nearly three out of every five (57%) significant cyber incidents involve attacks the cybersecurity team had […]

Cyberangriff auf Bundesagentur: Tatverdächtige gefasst
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2605814619.jpg?quality=50&strip=all 4500w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2605814619.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2605814619.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2605814619.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2605814619.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2605814619.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2605814619.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/10/shutterstock_2605814619.jpg?resize=150%2C84&quality=50&strip=all 150w, […]

EU to sign UN Convention on Cybercrime
The Council of Europe has authorized the European Commission and member states to sign the United […]
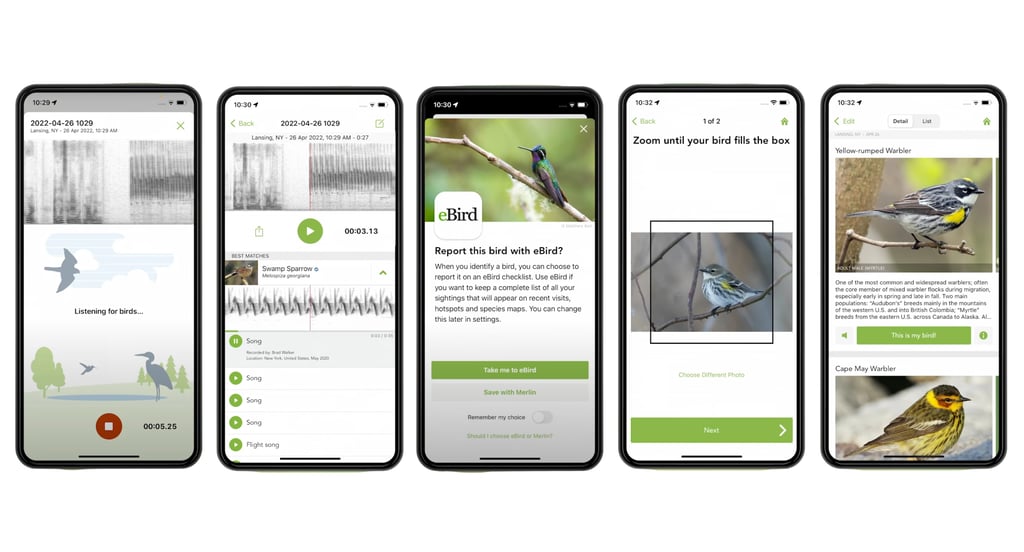
Best AI Tools for Birders
For birders, spotting a flash of feathers and not knowing its name can be frustrating, especially […]
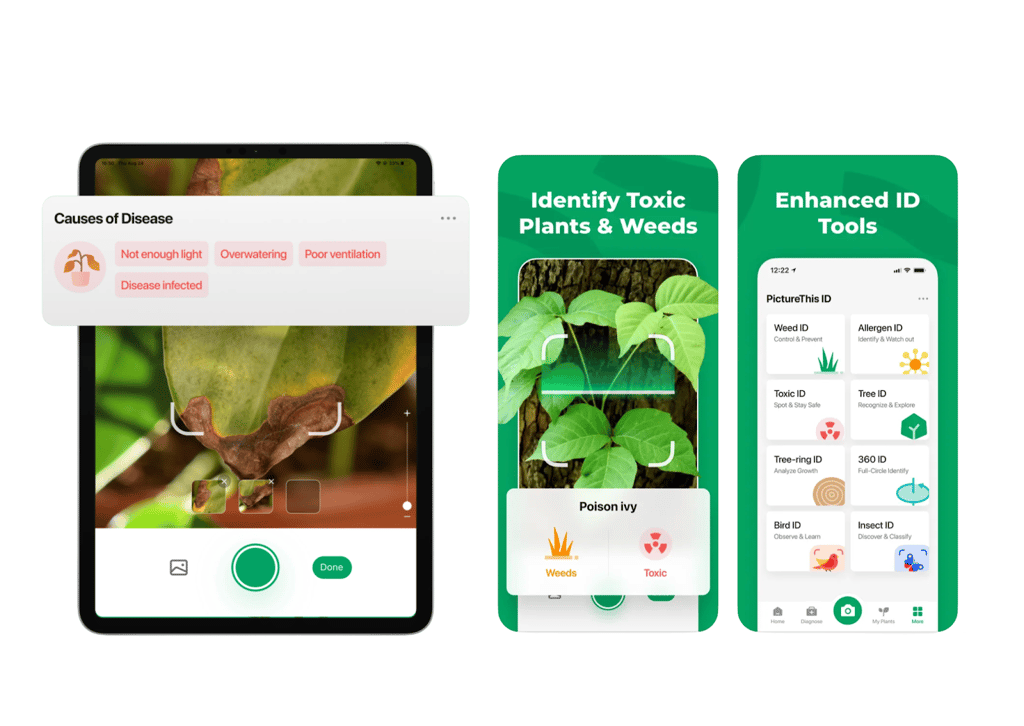
Best AI Tools for Gardening
For people like me who don’t have a green thumb, gardening can feel overwhelming. Here’s the […]

Is Figure 03 the ‘Model T’ moment for robots?
Figure AI just dropped Figure 03, and holy moly: this might be the first humanoid robot […]
