
European law enforcement breaks high-end encryption app used by suspects
A group of European law enforcement agencies were able to crack a high-level encryption app that […]

Fortinet offers integrated cloud app security service
Fortinet has melded some of its previously available services into an integrated cloud package aimed at […]

Security teams should act now to counter Chinese threat, says CISA
Security teams and individuals across the US need to take immediate precautions to counter the surveillance […]

Neue AWS-KI-Rezepte gegen Cloud-Bedrohungen
Amazon Web Services erweitert seine Cloud-Security-Angebote um KI- und ML-Funktionalitäten. Gorodenkoff / Shutterstock Wenn zunehmend komplexe […]

Russland knöpft sich Exil-Wodka vor
Russische Behörden und Hacker treiben Die unliebsame Exil-Firma in den Ruin. Alex Alaks/shutterstock.com Die US-Unternehmen der […]
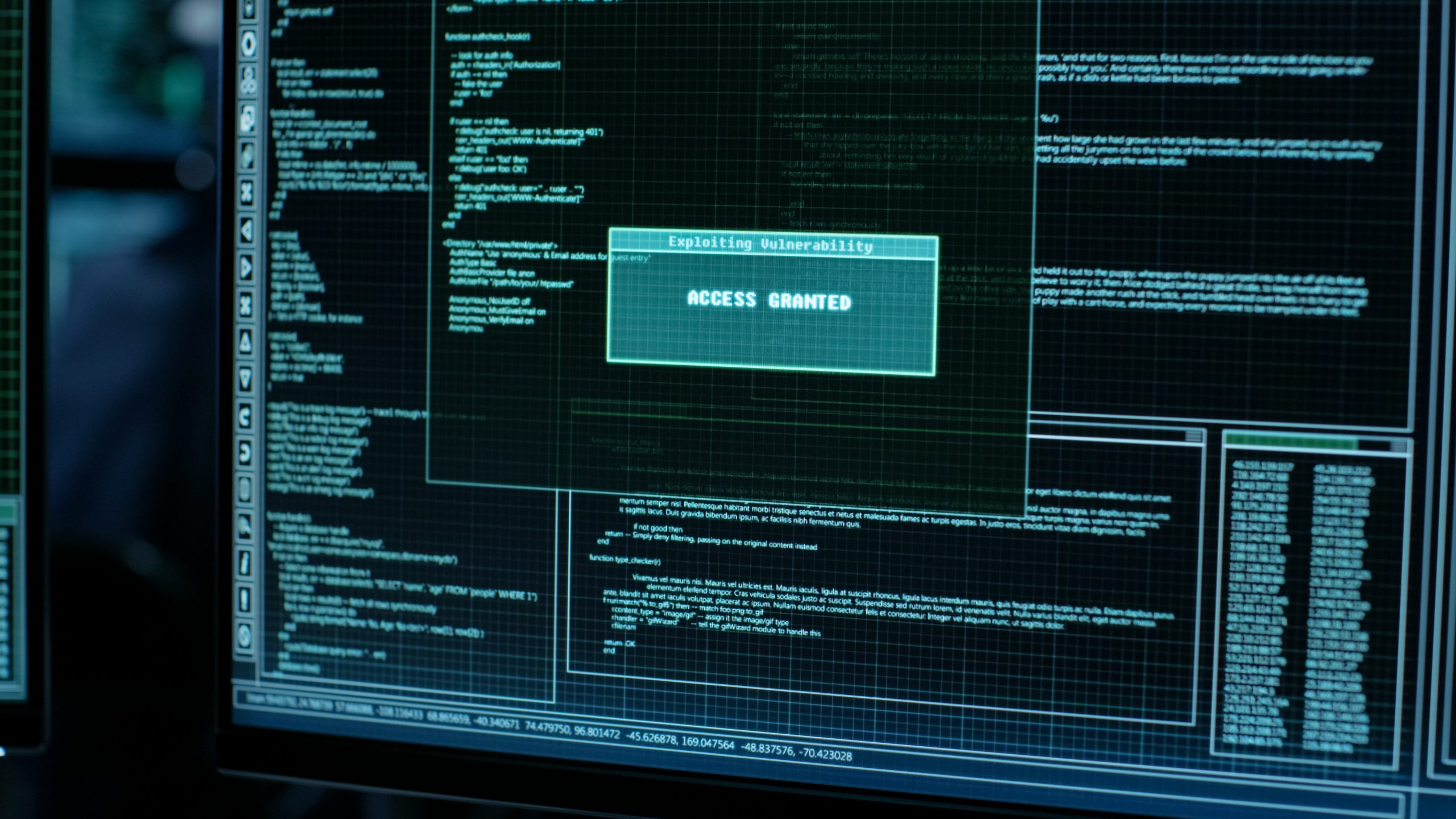
Veeam issues patch for critical RCE bug
Veeam is warning its customers of two vulnerabilities, of which one is a critical RCE bug, […]

Erstes Linux-UEFI-Bootkit ist Studentenprojekt
Bootkits sind kein Windows-exklusives “Feature” mehr. isarisphotography | shutterstock.com Forscher des Sicherheitsanbieters ESET hatten Ende November […]

63% of companies plan to pass data breach costs to customers
Consumers may be more on the hook for paying for the rising costs of data breaches […]

Talent overlooked: embracing neurodiversity in cybersecurity
In cybersecurity, diverse perspectives help in addressing complex, emerging threats. Increasingly, there’s a push to recognize […]
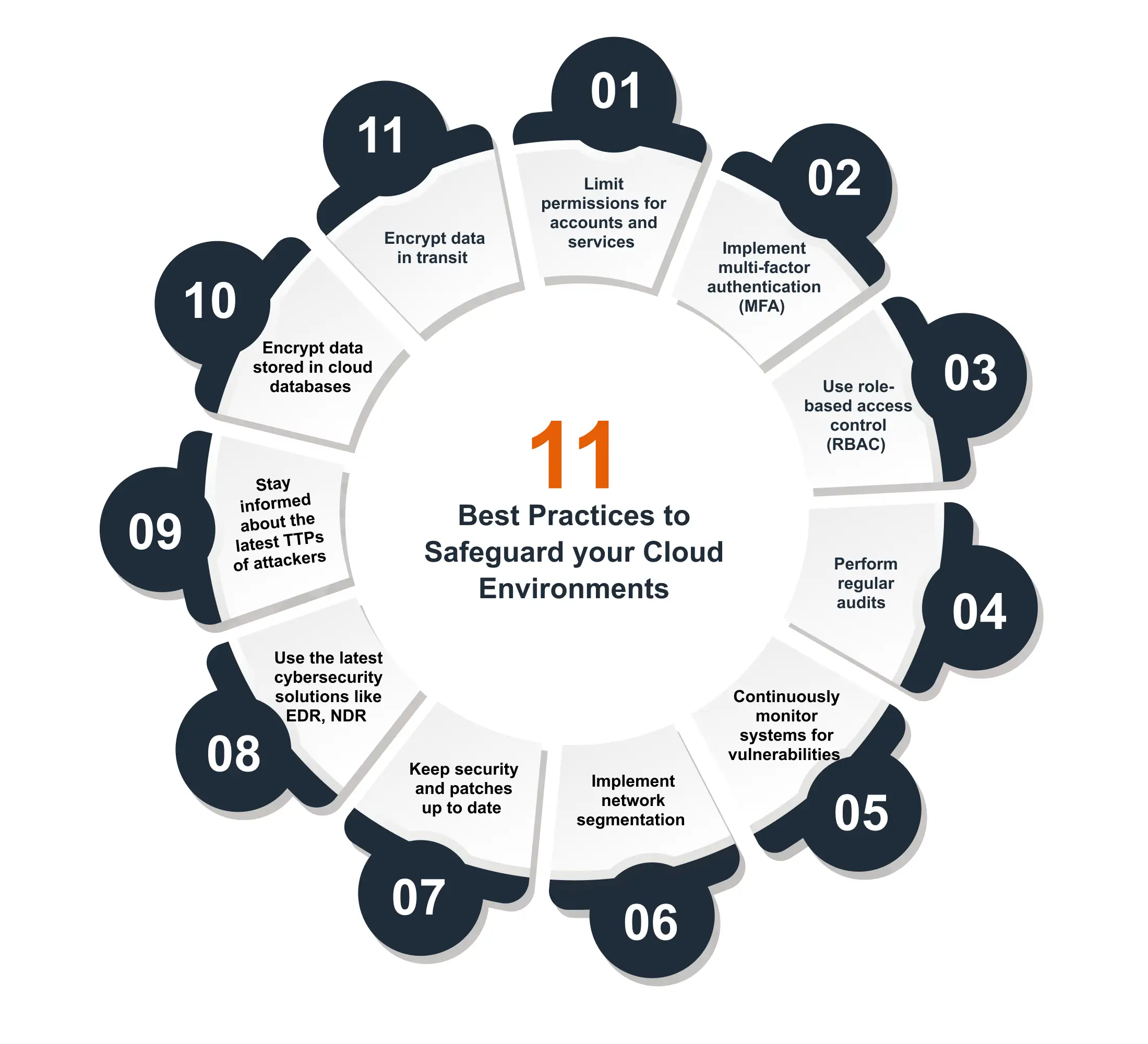
Lessons to Learn from TeamTNT: Best Practices for Securing Cloud Environments
Is your system being used for crypto mining without your consent? This might sound unlikely to […]
