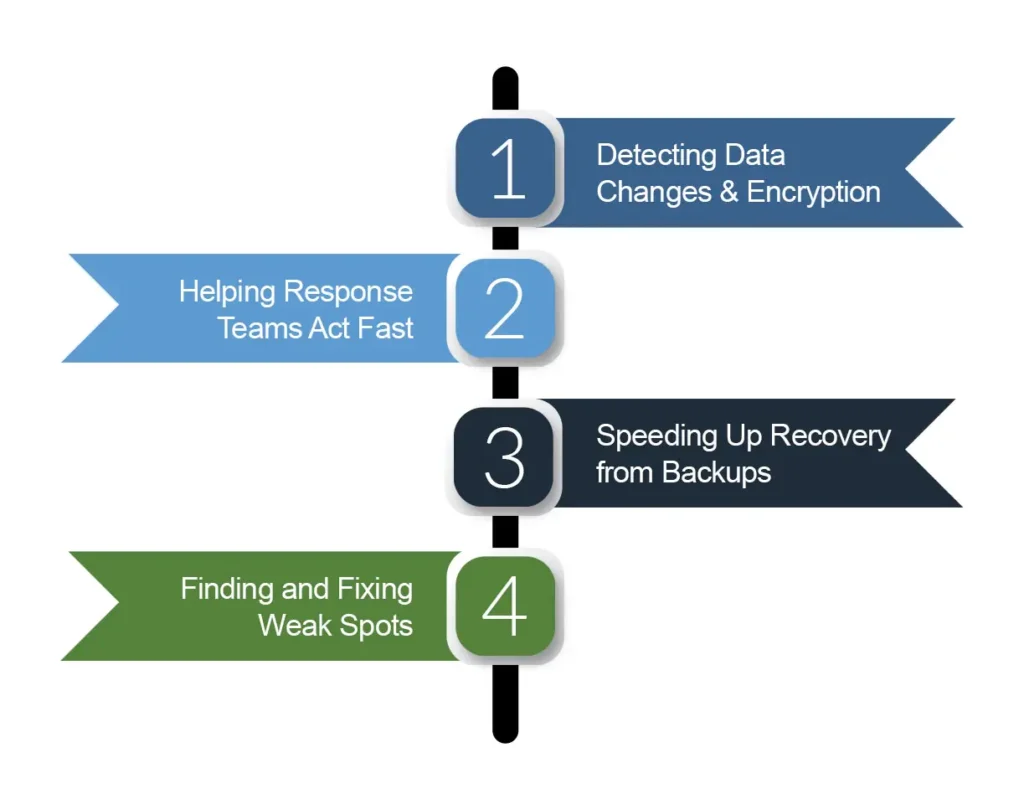
Fighting Ransomware: Using DLP Solutions to Protect Your Organization
Ransomware has evolved over the years and is now targeting organizations of all sizes with both […]

Russian hackers abuse Cloudflare tunneling service to drop GammaDrop malware
In a new campaign, a Russia-backed advanced persistent threat (APT) group is seen abusing Cloudflare tunnels […]

FCC calls for urgent cybersecurity overhaul amid Salt Typhoon espionage case
In the wake of the Salt Typhoon cyberespionage campaign allegedly linked to China, Federal Communications Commission […]

Struggling to Find Your Next Job in Cybersecurity?
Finding your next job in cybersecurity can feel like navigating a maze. If you are beginning […]

8 biggest cybersecurity threats manufacturers face
The manufacturing sector’s rapid digital transformation, complex supply chains, and reliance on third-party vendors make for […]

Sind Macs noch sicher?
MacOS galt lange als „Malware-frei“. Eine Studie legt nahe: Diese Zeiten sind längst vorbei. Zyracuze | […]

Data deletion enters the ransomware chat
Ransomware remains one of the biggest cyber threats to companies today. In a survey by security provider […]

Die besten Hacker-Filme
Vorsicht, dieses Film-Listicle kann zu Prokrastination verführen! Nomad Soul | shutterstock.com Security-Profis und -Entscheider mit Hang […]

CISOs still cautious about adopting autonomous patch management solutions
Failing to patch vulnerabilities keeps biting CISOs. The most recent evidence: Last month, the Five Eyes […]

Securing cloud-native applications: Why a comprehensive API security strategy is essential
Despite their capabilities and benefits, cloud-native applications also present several security challenges. Application programming interfaces (APIs) […]
