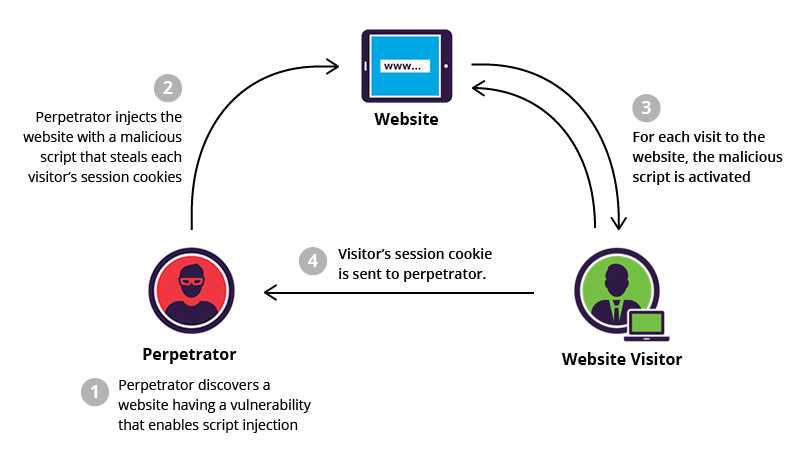
XSS 101: Understanding the Basics of Cross-Site Scripting (XSS) Vulnerabilities
Yooo mates, it’s Rocky here! Hope you’re all pumped up because today we’re diving into another […]
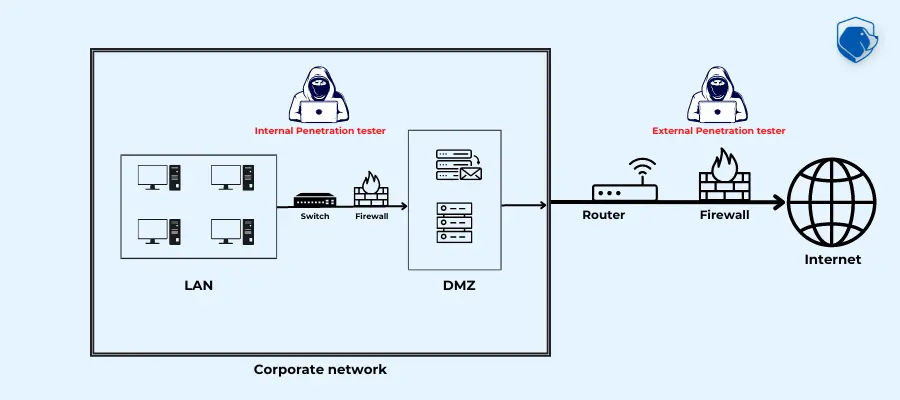
Automated Pentesting: The Future of Network Security
Greetings to all! Welcome to our exploration of network security’s future, with a particular focus on […]

SAP systems increasingly targeted by cyber attackers
A review of four years of threat intelligence data, presented Friday at Black Hat by Yvan […]

PUMA creeps through Linux with a stealthy rootkit attack
A new loadable kernel module (LKM) rootkit has been spotted in the wild compromising Linux systems […]

How to turn around a toxic cybersecurity culture
A toxic cybersecurity culture affects team turnover, productivity, and morale. Worse yet, it places enterprise systems […]
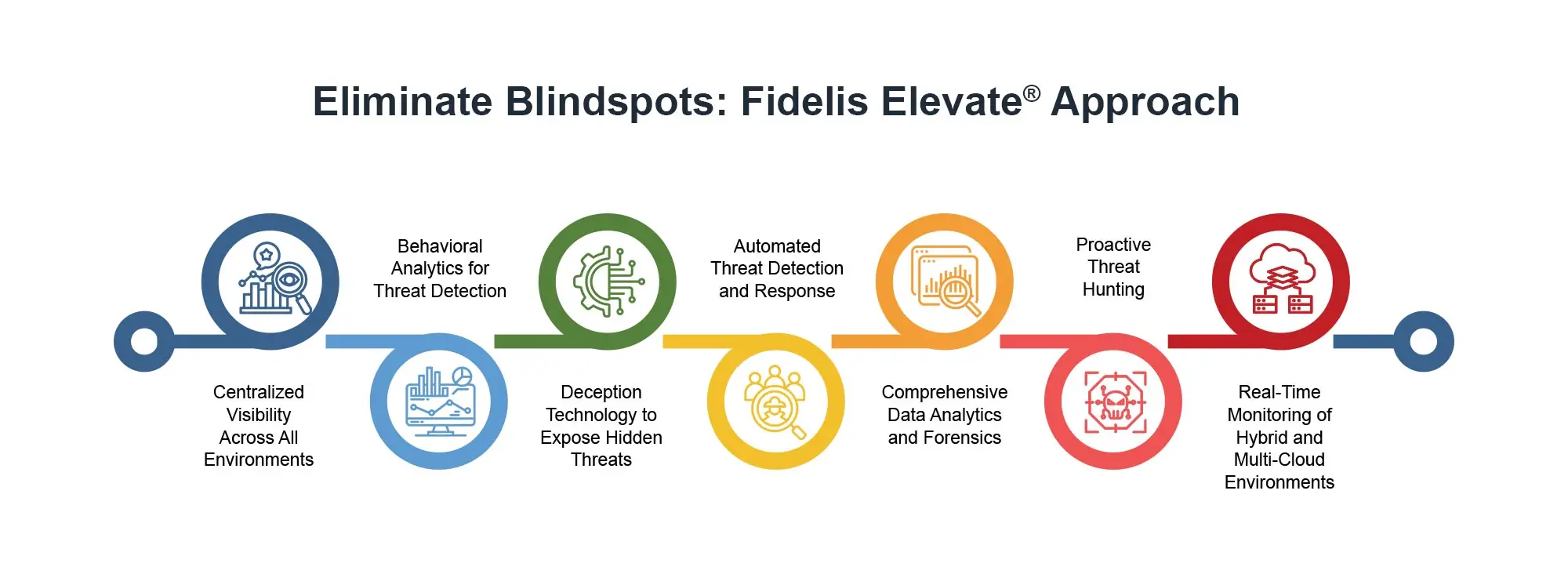
Fidelis Elevate® (XDR): A Proactive Way to Eliminate Blind Spots
The growing complexity of IT environments—across cloud, IoT, and hybrid settings—has ushered in new opportunities for […]

10 wichtige Security-Eigenschaften: So setzen Sie die Kraft Ihres IT-Sicherheitstechnik-Teams frei
Lesen Sie, worauf es bei der Zusammenarbeit zwischen Ihrem IT-Security- und Engineering-Team ankommt. Foto: Lipik Stock […]

Security researchers find deep flaws in CVSS vulnerability scoring system
The industrywide method for assessing the severity of vulnerabilities in software and hardware needs to be […]

Europol shutters 27 DDoS sites in major crackdown
Europol has announced that it has carried out a major crackdown on cybercriminal actors in cooperation with the […]

Microsoft Windows ‘Best Fit’ character conversion ‘ripe for exploitation’
Security researchers have outlined a novel attack vector that exploits the “Best Fit” character conversion technology […]
