
SAP systems increasingly targeted by cyber attackers
A review of four years of threat intelligence data, presented Friday at Black Hat by Yvan […]

PUMA creeps through Linux with a stealthy rootkit attack
A new loadable kernel module (LKM) rootkit has been spotted in the wild compromising Linux systems […]

How to turn around a toxic cybersecurity culture
A toxic cybersecurity culture affects team turnover, productivity, and morale. Worse yet, it places enterprise systems […]
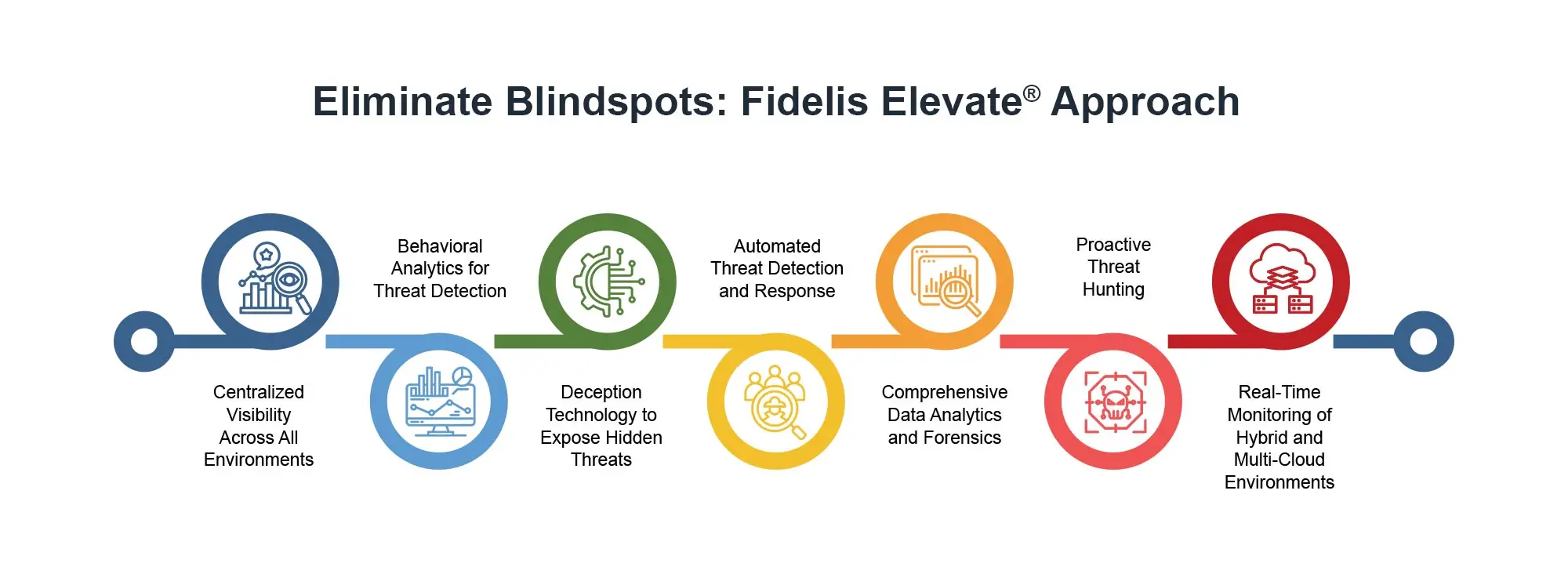
Fidelis Elevate® (XDR): A Proactive Way to Eliminate Blind Spots
The growing complexity of IT environments—across cloud, IoT, and hybrid settings—has ushered in new opportunities for […]