HOW TO BECOME CERTIFIED LEAD IMPLEMENTER – ISO 27001
ABOUT CERTIFIED LEAD IMPLEMENTER TRAINING AND EXAMINATION FOR INFORMATION SECURITY MANAGEMENT SYSTEM ISO / IEC 27001 […]
YouTube disrupted in Pakistan as former PM Imran Khan streams speech
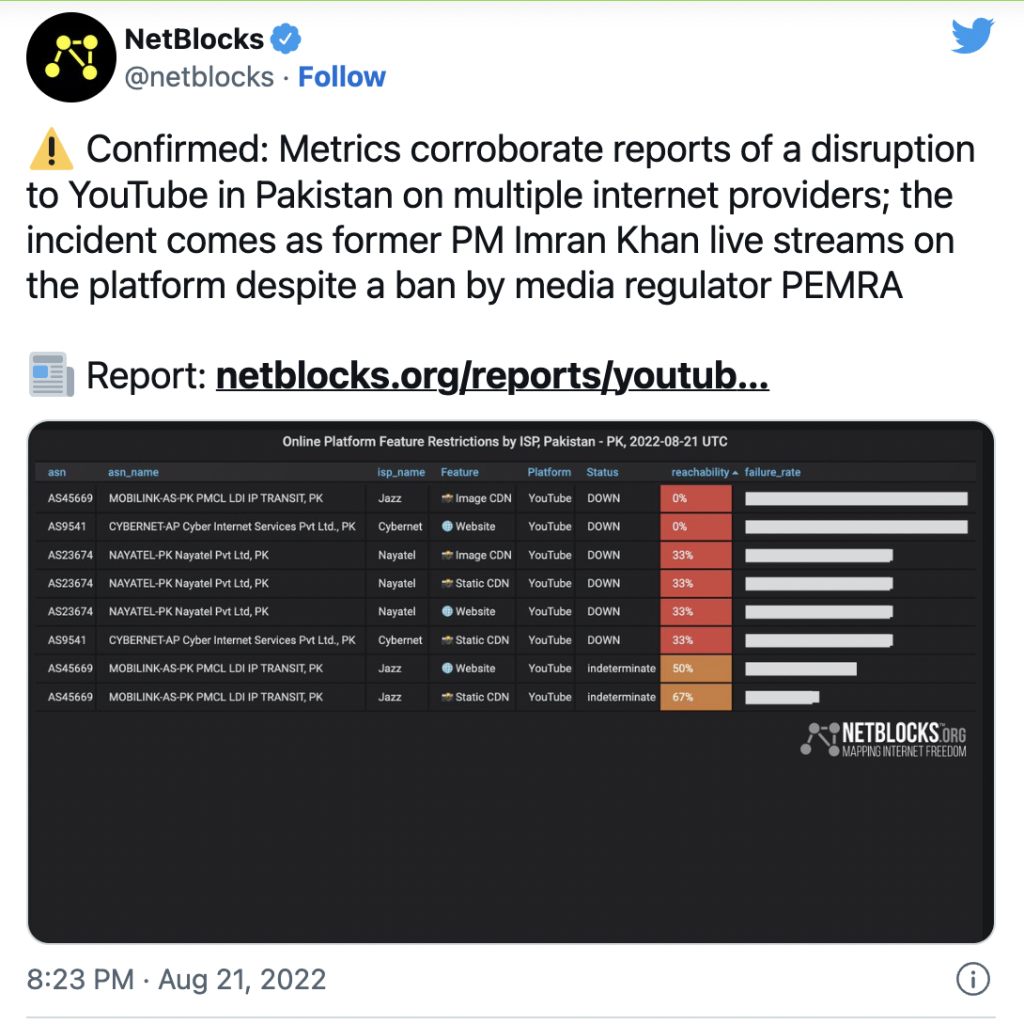
NetBlocks metrics confirm the disruption of YouTube on multiple internet providers in Pakistan on Sunday 21 […]
YouTube disrupted in Pakistan as former PM Imran Khan streams speech
NetBlocks metrics confirm the disruption of YouTube on multiple internet providers in Pakistan on Sunday 21 […]

RFC 9116 / “security.txt” Has Been Published
After 5 years of work, security.txt is officially an RFC. I am pleased to announce RFC […]

GitBleed – Finding Secrets in Mirrored Git Repositories – CVE-2022-24975
Summary Due to a discrepancy in Git behavior, partial parts of a source code repository are […]
Insecure Bootstrap Process in Oracle Cloud CLI
Summary The bootstrap process for Oracle Cloud CLI using the “curl | bash” pattern was insecure […]
Three Reasons Why Log4J Is So Bad: Ubiquity, Severity and Exploitability
Over the last few weeks, security teams everywhere have been busy patching Log4J vulnerabilities. In this […]
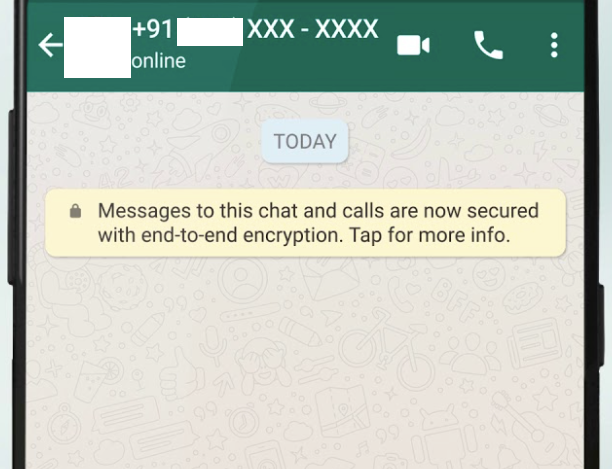
WhatsApp for Android Retains Deleted Contacts Locally
Summary WhatApp for Android retains contact info locally after contacts get deleted. This would allow an […]
Recommendations for Parents about Cyber Bullying
Here are some dedicated tips for keeping younger children safe online. One of these training tips […]
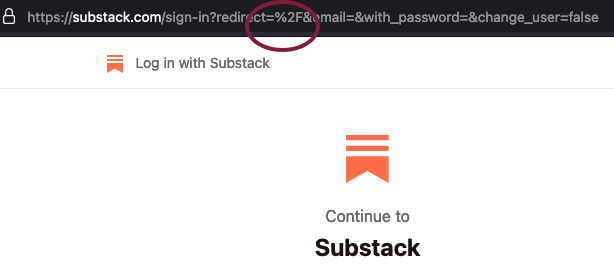
Open Redirect Vulnerability in Substack
Summary Substack had a open redirect vulnerability in their login flow which would have allowed an […]
