Cookies vs Sessions Explained: What You Need to Know
Hey there! Welcome to our guide on sessions and cookies. So, what’s the big deal about […]
Creating Custom .onion Addresses for Tor Hidden Services
This article can often contain rather random Tor .onion links. I’ll show you how to create […]

Understanding the Web and HTTP
The web refers to the World Wide Web (commonly used as WWW), a sub-concept of the […]
Red team vs Blue team: A CISO’s Guide to Offensive Security
It’s 3 am. Your phone screams. Hackers are in your system. Panic sets in. But wait! […]
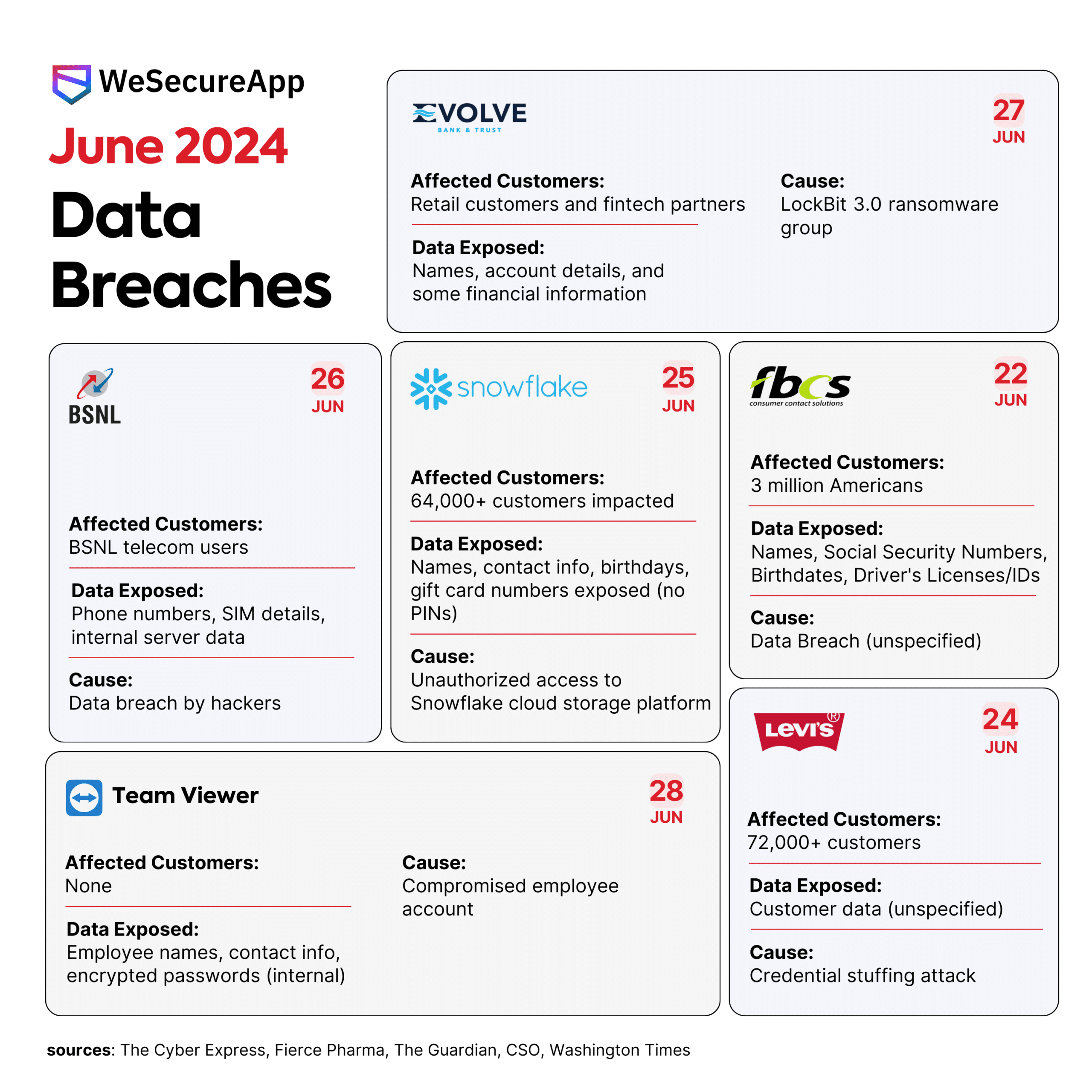
Data Breaches in June 2024 – Infographic
Have you ever gotten that sinking feeling that your personal information might be out in the […]
Data Breaches in June 2024 – Infographic
Have you ever gotten that sinking feeling that your personal information might be out in the […]
The Vital Role of On-Premises Hardware Security Module (HSMs) in Securing Encryption Keys
Encryption stands as a cornerstone for safeguarding sensitive data within any organization. Complying with data privacy […]

How To Scan a Website for Vulnerabilities: Top Tools and Techniques
Knowing how to scan a website for vulnerabilities can help keep you protected in today’s digital […]
CryptoBind HSM is now built with FIPS 140-3 Level 3 Certified Cryptographic Boundary
In the ever-evolving landscape of digital security, staying ahead of the curve is paramount. Today, we […]
Safeguarding Your Digital Assets: The Crucial Role of Enterprise Key Management Systems
In today’s digital age, the landscape of cybersecurity is complex and ever evolving. Protecting sensitive information […]
