
Newly patched Ivanti CSA flaw under active exploitation
IT management solutions provider Ivanti confirmed that a high-severity flaw patched this week in an older […]

New cryptomining campaign infects WebLogic servers with Hadooken malware
A new attack campaign compromises misconfigured Oracle WebLogic servers and deploys a backdoor program called Hadooken […]

Protecting Sensitive Data with Office 365 Data Loss Prevention
Mastering Microsoft 365 Data Loss Prevention: Setup, Policies, Benefits, and More! Managing and Safeguarding data is […]

Fortinet confirms breach that likely leaked 440GB of customer data
Fortinet has confirmed a data breach that has allegedly compromised 440GB of Azure SharePoint files containing […]

Understanding and Mitigating the Risks of Email Forwarding
Email forwarding, while a seemingly harmless and convenient feature, can pose significant risks to data security […]

Aflac’s shift to passkeys brings big business benefits
At supplemental insurance provider Aflac, safeguarding information collected on behalf of employees and the customers and […]

Mastercard acquires Recorded Future: How will threat intelligence transform the payments industry?
As cyber criminals grow ever more crafty with their tactics, enterprises are increasingly turning to threat […]

Too many companies use non-enterprise grade remote access tools in their OT networks, says Claroty
In May 2020, Iranian attackers attempted to alter chlorine levels in drinking water in a cyber […]

Fake recruitment campaign targets developers using trojanized Python packages
The number of attacks looking to compromise developer machines has exploded in recent years. There has […]
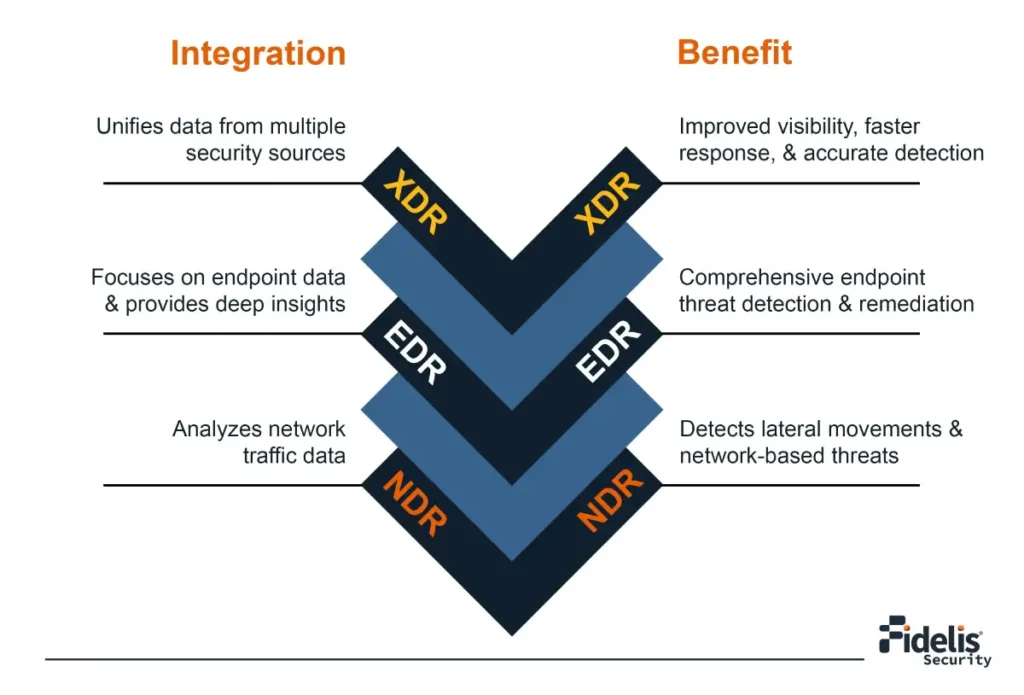
Understanding XDR, NDR, and EDR: A Comprehensive Guide to Modern Cybersecurity Solutions
Cybersecurity leaders should be well-versed with current trends and best practices in security management to effectively […]
