
How to make your multicloud security more effective
The days of debating whether cloud or on-premises is the best location for your servers are […]
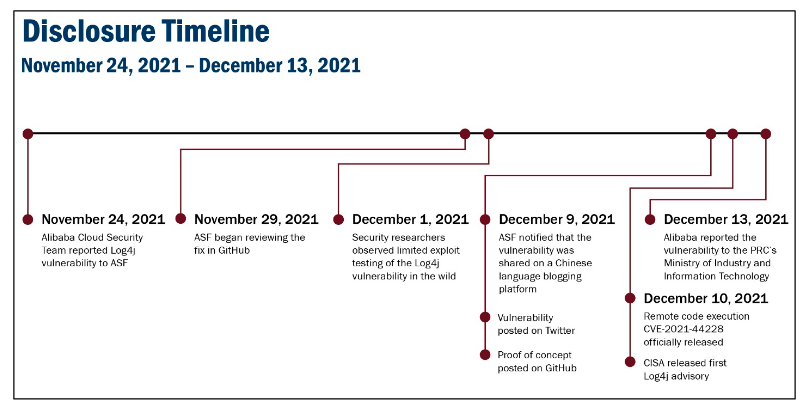
Additional Vulnerabilities in Log4J
Table of Contents Table of ContentsIntroductionAbout Log4J, Log4Shell and Related CVEsString Interpolation, Java EE and How […]

The top red teamer in the US is an AI bot
AI is getting so good that it’s outperforming human red teamers. The hacker “Xbow” now tops […]

Misconfigured MCP servers expose AI agent systems to compromise
Agentic AI is on the rise, and Model Context Protocol (MCP) servers are fast proving to […]

Top 10 Pros and Cons of AI Code Assistants Like GitHub Copilot – A Must-Read Guide for Developers
1. Introduction: Why AI Code Assistants Are Changing the Game In recent years, artificial intelligence has […]

The Ultimate Career Guide to Becoming a DevOps Engineer in 2025: Tools, Skills, and Roadmap
Introduction In a world driven by continuous innovation and fast-paced software delivery, DevOps has become the […]
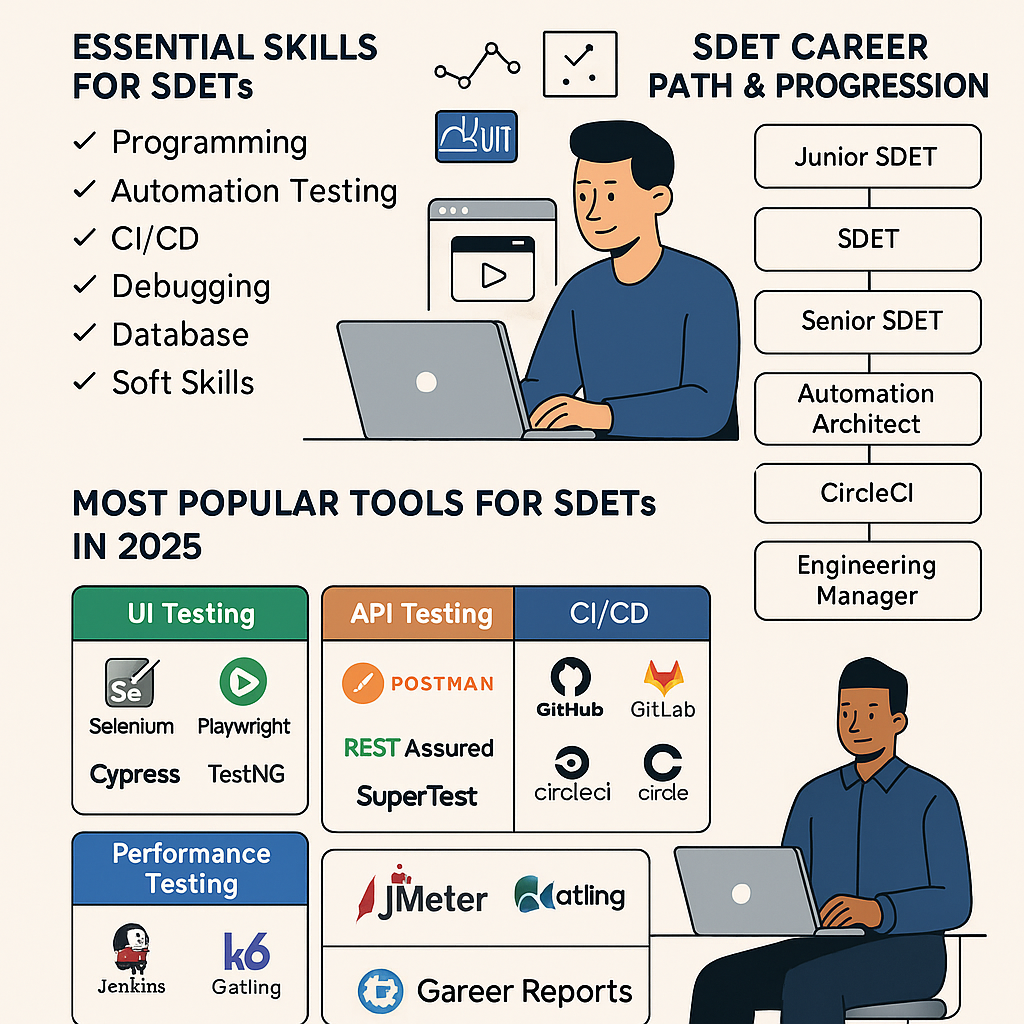
The Ultimate Career Guide to Becoming an SDET in 2025: Skills, Tools, and Growth Path
Introduction The role of the Software Development Engineer in Test (SDET) has become one of the […]
Data Masking Best Practices for Regulatory Compliance
Organizations in the rapidly evolving digital era today face mounting pressures to secure sensitive data and […]

Ransomware: So viel Lösegeld zahlen Unternehmen
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/06/shutterstock_2524192439.jpg?quality=50&strip=all 8000w, https://b2b-contenthub.com/wp-content/uploads/2025/06/shutterstock_2524192439.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/06/shutterstock_2524192439.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/06/shutterstock_2524192439.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/06/shutterstock_2524192439.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/06/shutterstock_2524192439.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/06/shutterstock_2524192439.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/06/shutterstock_2524192439.jpg?resize=150%2C84&quality=50&strip=all 150w, […]

SAP GUI flaws expose sensitive data via weak or no encryption
SAP GUI, a trusted interface for hundreds of thousands of global enterprises, has been found to […]
