
Cisco warns of critical API vulnerabilities in ISE and ISE-PIC
CSOs are being urged to quickly patch multiple vulnerabilities in Cisco Systems Identity Services Engine (ISE) […]

I’ve Interviewed Dozens of Cybersecurity Professionals — Here’s My Best Advice
Hey guys, Rocky here—you probably know me as the founder of CodeLivly. A few weeks ago […]

What Makes a Material “Good” Anyway?
Everywhere you look, there are materials holding everything together—walls, windows, chairs, phone cases, signs. But not […]

AMI MegaRAC authentication bypass flaw is being exploitated, CISA warns
A critical authentication bypass by spoofing vulnerability in AMI MegaRAC SPx server management firmware is now […]

US indicts one for role in BreachForums, France arrests four others
A US court indicted a man accused of being IntelBroker, a key administrator of stolen data […]
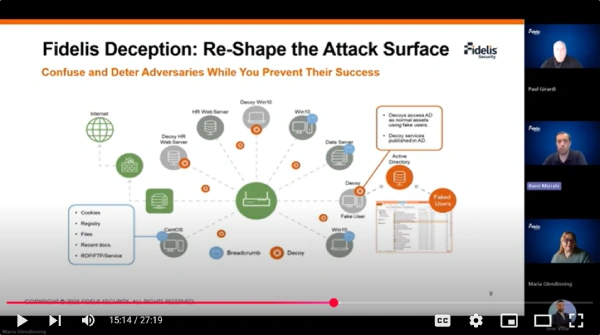
How Fidelis Deception® Strengthens Network Detection and Response
Network Detection and Response systems excel at monitoring network traffic and identifying patterns, but they face […]

SAP-Schwachstellen gefährden Windows-Nutzerdaten
Schwachstellen in SAP GUI geben sensible Daten durch schwache oder fehlende Verschlüsselung preis. LALAKA – shutterstock.com […]

Pressure is mounting to cut jobs in favor of AI. Here’s why you shouldn’t.
Security giant CrowdStrike announced via an official SEC filing last month that it plans to cut […]

Energienetze: Neue Regeln sollen Sicherheitslücke schließen
Betreiber von Energieanlagen müssen künftig die Sicherheit ihrer kritischen IT-Komponenten prüfen lassen. Pand P Studio – […]

How to make your multicloud security more effective
The days of debating whether cloud or on-premises is the best location for your servers are […]
