
Critical BeyondTrust RS vulnerability exploited in active attacks
Researchers warn that a critical vulnerability patched this week in BeyondTrust Remote Support is being exploited […]

How Cloud-Native Applications Defend Against DDoS Attacks
Key Takeaways Cloud DDoS attacks are increasingly sophisticated, targeting APIs, microservices, and cloud workloads rather than […]

South Korea fines Louis Vuitton, Christian Dior, Tiffany $25M for SaaS security failures
South Korea’s data protection authority has handed down a combined KRW 36 billion (approximately US$25 million) […]
Researchers unearth 30-year-old vulnerability in libpng library
Developers have resolved a legacy flaw in the widely used libpng open-source library that existed since […]

Battling bots face off in cybersecurity arena
AI agents are increasingly seen as a way to reinforce the capabilities of cybersecurity teams — […]

The Blueprint of Change: How to Build Healthy Habits That Actually Stick in 2026 🏗️✨
We’ve all been there. It’s January 1st (or a random Monday morning), and you are fired […]

Finding Your Zen: The Best Meditation Apps to Quiet the Noise in 2026 🧘♂️✨
In a world that seems to be moving at 100 miles per hour, finding a moment […]
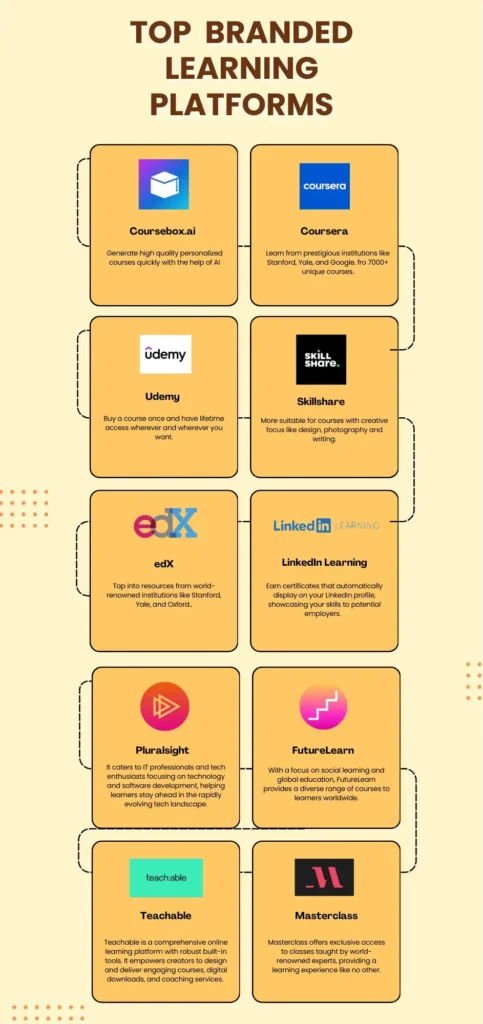
The Knowledge Gold Rush: Best Online Course Platforms for 2026 🎓✨
In 2026, the walls of the traditional classroom haven’t just crumbled—they’ve gone completely digital. We are […]

The Digital Safe: Best Crypto Wallets for Your Assets in 2026 🔐🚀
So, you’ve finally decided to join the decentralized revolution, or maybe you’re a seasoned “HODLer” looking […]

The Digital Receptionist: Why the Best Chatbot Software for Websites is a Game Changer in 2026 🤖✨
Imagine walking into a high-end store. Immediately, a friendly assistant greets you, remembers your last purchase, […]
