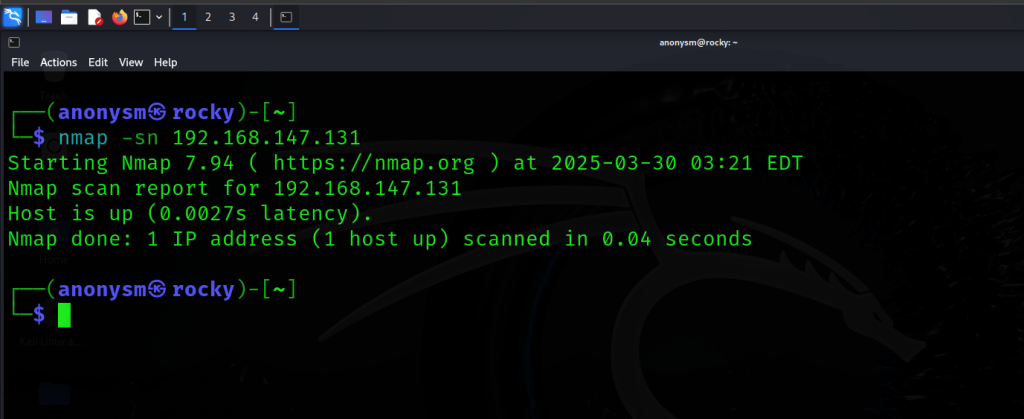
The Ultimate Nmap Guide: Master Network Scanning, Scripting, and Security Audits
Hey guys, Rocky here! 👋 Welcome to your ultimate guide to Nmap—the Swiss Army knife of […]
The Digital Personal Data Protection (DPDP) Act 2023: Key Challenges and Compliance Framework
The Digital Personal Data Protection Act 2023 (DPDP Act) marks a transformative shift in India’s data […]

Ubuntu namespace vulnerability should be addressed quickly: Expert
Linux admins who have enabled the unprivileged user namespace restriction in their recent Ubuntu environments should […]
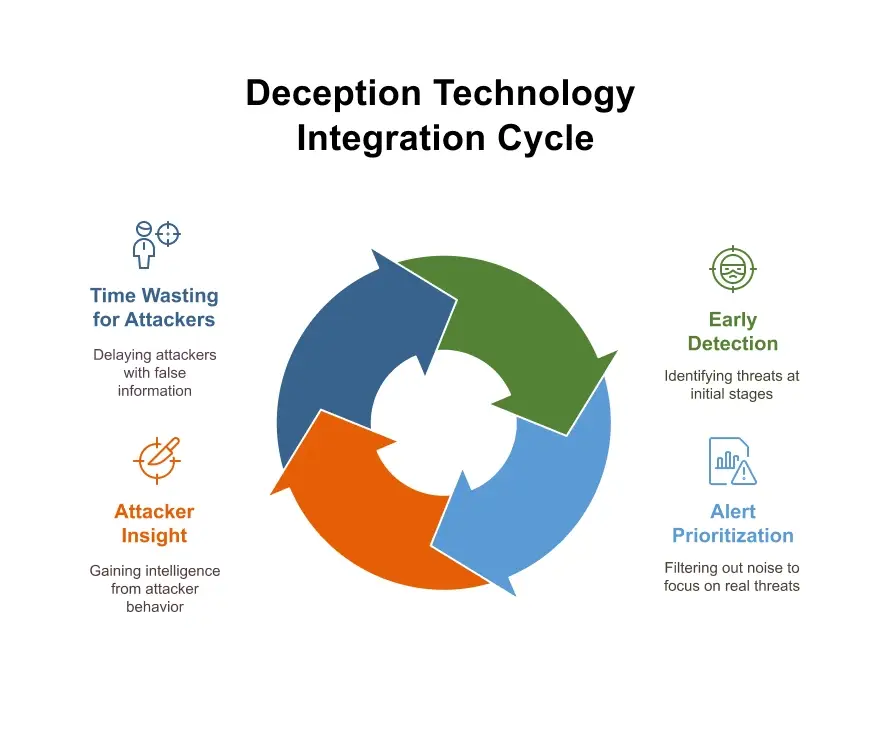
What Is the Role of Deception in XDR? Understanding Its Importance
Let’s face it – cybersecurity in 2025 is a mess. Bad guys keep slipping past our […]

Zu wenig Budget für OT-Security
width=”2500″ height=”1406″ sizes=”(max-width: 2500px) 100vw, 2500px”>Obwohl die Budgets für Cybersicherheit gestiegen sind, fehlt es oft an […]

Salt Typhoon may have upgraded backdoors for efficiency and evasion
The notorious China-backed APT group, Salt Typhoon, appears to have upgraded its arsenal with enhanced backdoors, […]

CIO des Jahres 2025 – Wettbewerb startet
Siegerinnen und Sieger des vergangenen Jahres jubeln über ihre CIO des Jahres Awards. Machen Sie mit […]

The Trump administration made an unprecedented security mistake – you can avoid doing the same
If you are the custodian for sensitive information, you have no doubt been watching the inexplicable […]

How to create an effective crisis communication plan
Incident response isn’t the only challenge CISOs must face when confronted with a cyberattack. Corporate communications […]

Researchers claim their protocol can create truly random numbers on a current quantum computer
A team that included researchers at a US bank says it has created a protocol that […]
