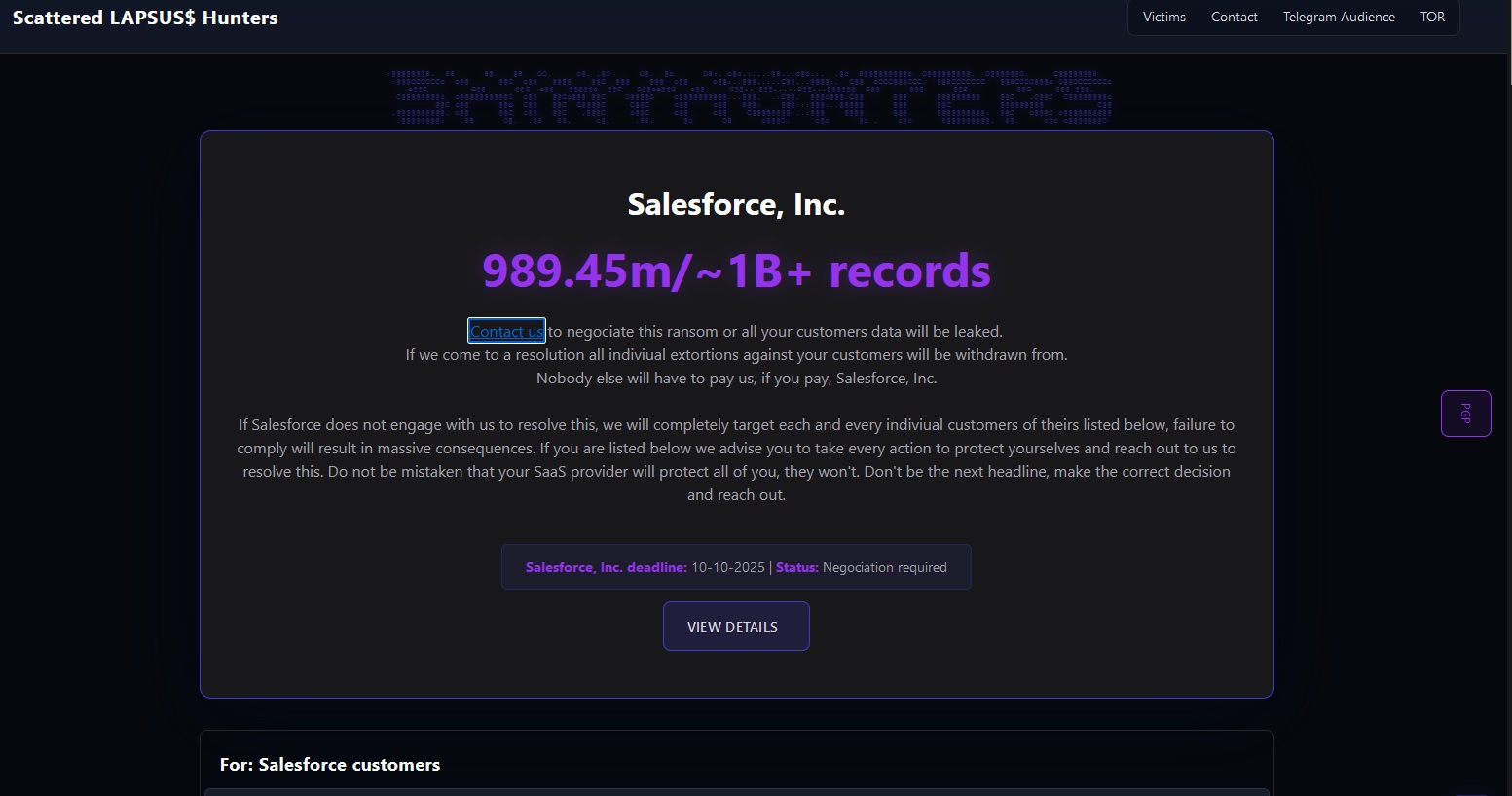
Only days ago, a message on the BreachForums extortion site threatened to leak one billion records allegedly stolen from the Salesforce systems of 39 of the largest companies in the world, including Disney, Toyota, Adidas, McDonalds, IKEA, and Home Depot.
It was a threat that the criminals behind the site, a super-alliance of the ShinyHunters, Scattered Spider, and LAPSUS$ ransomware groups known as Scattered Lapsus$ Hunters, vowed to carry out via its dark web and Clearnet sites if Salesforce did not pay a ransom by 11.59 p.m. EST on October 10.
“If Salesforce does not engage with us to resolve this, we will completely target each and every indiviual [sic] customers of theirs listed below, failure to comply will result in massive consequences,” said a message on the original leak site.
“If you are listed below we advise you to take every action to protect yourselves and reach out to us to resolve this. Do not be mistaken that your SaaS provider will protect all of you, they won’t.”
However, on October 9, the BreachForums dark net and Clearnet sites displayed a very different message. “This domain has been seized,” announced a domain takedown image, an action coordinated jointly by the US Department of Justice (DoJ), the FBI, France’s BL2C cybercrime unit, and the Paris Prosecutor’s Office.
Normally, more detail on a police action of this magnitude would be published by the FBI itself, but the agency’s website is currently not being updated due to the US government shutdown.
What seems clear is that the bust is a significant one, disrupting not only the BreachForums sites but the back-end infrastructure, database archives, and escrow payment data dating back to 2023.
“BreachForums was seized by the FBI and international partners today. All our domains were taken from us by the US Government. The era of forums is over,” the Scattered Lapsus$ Hunters group said in a PGP-encrypted statement on Telegram.
Now for the bad news: as of October 9, the wider Salesforce ransom campaign is still active. Although the primary BreachForums sites have been taken over, a separate dark web data leak site remains operational, and the group is still threatening to release the Salesforce data records as originally planned, CSO Online has confirmed.
Fall and rise
This is not the first time BreachForums has been on the wrong end of police action.
Domain seizure number one happened in June 2023, three months after the alleged BreachForums founder Conor Fitzpatrick was arrested in New York. The site was reinstated by ShinyHunters, only to be downed for the second time in May 2024. More arrests followed in 2025. By August, reports of Salesforce customers being targeted by ShinyHunters started to emerge, culminating in the latest action.
Everything hinges on whether the group really has the data as claimed. There is no way to confirm this — ransomware groups have a record of exaggerating their crimes for the sake of publicity — but no way to refute it either.
“At this time, there is no indication that the Salesforce platform has been compromised, nor is this activity related to any known vulnerability in our technology,” a Salesforce spokesperson told Reuters earlier this month.
The significance of the takedown is hard to assess beyond its symbolic value, but should become clearer in the weeks ahead, suggested experts.
“Domain seizures often provide server logs, user data, and cryptocurrency trails that can help fuel indictments and asset freezes. Today’s seizure also has the potential to disrupt ransomware supply chains for future operations,” said Zbyněk Sopuch, CTO of security vendor Safetica Technologies.
Nevertheless, one takedown was unlikely to reduce the wider threat of ransomware attacks. “CSOs should consider today’s seizure a 30-day grace period to ramp up dark web monitoring tools, audit Salesforce configurations, and drill their incident response playbooks,” he said.
Targeting SaaS
Rik Ferguson, VP security intelligence at Forescout, agreed that any disruption was likely to be a temporary setback.
“It burns infrastructure, yields intelligence, and sows distrust among criminals. But the gang’s dark-web leak site is still up, and they explicitly say the campaign continues,” he told CSO Online by email.
“That tells you everything about the current model: forum-free, portable extortion that pivots across Telegram, throwaway domains, and bespoke leak sites. Taking the sign down doesn’t close the business.”
According to Ferguson, “SaaS is the new blast radius,” often compromised by abusing the OAuth and app-to-app trust on which these interconnected services depend. This is an attack surface that ransomware attackers will continue to target.
How should enterprises secure themselves? “Turn on OAuth app governance, least privilege scopes, token lifetime limits, and automated revocation on anomaly detection, kill any standing trust, rotate keys and tokens, shorten session lifetimes, and require step-up auth for high-risk actions,” advised Ferguson.
No Responses