When it comes to online privacy and anonymity, Tor Browser (short for The Onion Router) stands out as one of the most powerful tools on the internet. Originally built from the open-source Firefox browser, Tor has been modified to hide a user’s real IP address, keeping your online identity private and untraceable. This makes it extremely difficult for anyone — from advertisers to cyber-trackers — to know who you are or where you’re browsing from.
What makes Tor so impressive is its simplicity. You don’t need to be a tech expert to stay anonymous online. Once installed, Tor automatically routes your traffic through multiple encrypted layers, making it almost impossible to track your activities. It’s completely free to download and gives users the power to explore the internet freely and safely — no complex setup required.
In short, Tor Browser has revolutionized anonymous internet use by combining ease of use with serious privacy protection. Whether you’re concerned about data tracking, online surveillance, or just value digital freedom, Tor remains one of the best and most trusted tools for maintaining online anonymity in today’s connected world.
History & Intended Use of Tor
Tor (short for The Onion Router) was born from a simple but powerful idea: let people communicate freely and anonymously online. Its roots trace back to U.S. government research in the early 2000s, but today Tor is an open-source project maintained by a global community of privacy advocates, technologists, and researchers. That community approach means no single organization controls Tor — anyone with the right skills can review, test, and improve it — which helps keep the project resilient and up to date.
Tor’s main purpose is straightforward: protect online privacy and enable anonymous internet use. People use Tor to get around censorship, for secure whistleblowing, and to keep sensitive business or personal conversations private. It routes web traffic through multiple encrypted relays so your real IP address is hidden from the sites you visit, making it much harder to trace who you are or where you’re browsing from.
Like any powerful tool, Tor has two sides. On one hand it’s a lifeline for journalists, activists, and anyone living under restrictive regimes. On the other hand, the same anonymity can be abused — for criminal activity or to hide bad behavior. A useful analogy: a car can take your kids to school or be used as a getaway vehicle. The tool is neutral; how people use it determines the outcome.
For investigators and digital forensics professionals, Tor presents two distinct angles to consider. One angle is device-focused: look for Tor artifacts on the computer or phone (installation files, configuration traces, or browser remnants). The other angle is network-focused: try to identify or intercept communications tied to Tor users — a much harder task that often requires specialized resources and legal authority. Tor runs on Windows, macOS, and Linux, so artifacts can appear across platforms, though Windows is commonly examined because of its wide usage. Some aspects of Tor are effectively untraceable for typical investigators, but that doesn’t mean there aren’t ways to gather relevant evidence when mistakes are made or additional data sources (like server logs or endpoint captures) are available.
How the Onion Router (Tor) Works
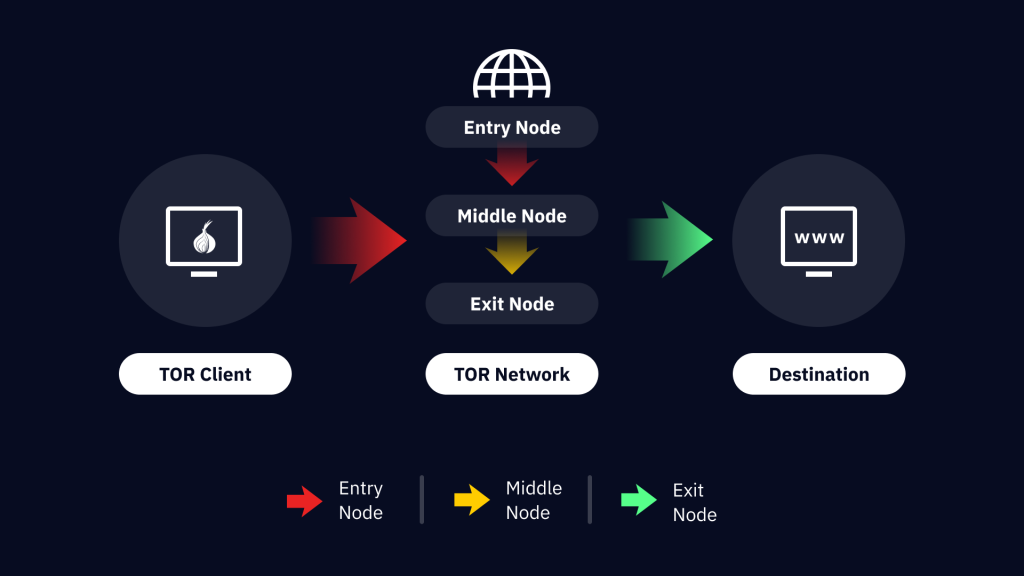
At its core, Tor Browser hides your digital footprint by bouncing your internet traffic through a series of random servers—called relays—spread all over the world. Before your data even leaves your device, it’s wrapped in several layers of encryption using elliptic-curve cryptography, which is practically impossible to break by brute force.
When you visit a website, your data first passes through an entry relay, where the outermost layer of encryption is peeled away. It’s then sent to a middle relay, which removes the next layer and forwards it again. Finally, your traffic reaches the exit relay, which connects to the target website. Each relay only knows the previous and next node in the chain—never the full route—so tracing your activity back to you becomes nearly impossible.
To make tracking even harder, Tor automatically changes your relay path every ten minutes. That constant rerouting gives you an extra layer of anonymity every time you browse.
A Simple Analogy
Think of Tor like mailing a letter wrapped in several envelopes.
Mary (the sender) writes a note to Johnny but doesn’t want him to know where it came from. So, she places her letter inside four envelopes—each addressed to a different person across different cities. Each person opens only one envelope, sees just the next address, and forwards it along. By the time Johnny gets the letter, all layers are removed, and the original source stays secret.
That’s exactly how Tor works—each layer of encryption acts like an envelope, peeled off at each relay until the data reaches its final destination. This “layered” process inspired the name The Onion Router, since the data is protected by multiple encryption layers, just like the layers of an onion.
The Exit Node Dilemma
Running a Tor exit node means your IP address becomes the one seen by the destination website. That can sometimes cause confusion or even legal issues. For instance, in 2011, U.S. authorities mistakenly raided a man’s home because illegal content appeared to come from his IP ,he was simply operating a Tor exit node. It’s a reminder that while Tor offers privacy and freedom, it can also carry responsibilities and risks for those who help keep the network running.
A Few Important Points About Tor
Before diving deeper, it’s important to understand a few key facts about how Tor works and why breaking Tor’s anonymity is almost impossible without extraordinary resources.
The Tor network is made up of thousands of volunteer-run relays—servers operated by everyday people around the world. Anyone can become a part of this global privacy network. When you run a Tor relay, your server simply “unwraps one layer of encryption and forwards the data” to the next node in the chain.
Because of this, if you ever investigate a suspicious IP address, keep in mind that it might not belong to the actual sender. It could just be a volunteer running a Tor relay, helping the network function securely.
Global Reach of Tor
One of the most fascinating aspects of Tor is its massive user base. According to the Tor Metrics Portal, over 750,000 users connect daily through 6,000+ relays worldwide. This huge, constantly shifting crowd of users strengthens anonymity—making it nearly impossible to trace one person out of hundreds of thousands.
Even if investigators could somehow “break” the encryption route, they’d face another challenge: international laws and cooperation between countries. For example, if a threatening email seems to come from an IP in Italy, that doesn’t mean the sender is actually there—it could have passed through multiple countries before reaching its destination.
How a Tor Circuit Works
Each Tor circuit consists of three main nodes:
Entry Node (Guard): The first encrypted hop from your computer. The Tor client picks a random guard node that remains fixed for a while.
Middle Node: A random relay that passes the data without knowing its source or destination.
Exit Node: The final node that sends your unencrypted data to the target website.
The Tor browser automatically changes these nodes every 10 minutes, constantly reshuffling the path. That makes tracking or intercepting traffic nearly impossible.
Tor Relays vs. Bridges
All standard Tor relays are publicly listed online, which means ISPs or governments can block them. To bypass such censorship, Tor uses bridges—hidden relays that aren’t listed publicly. These bridges allow users in restricted regions to connect to the Tor network privately, keeping access open even under heavy censorship.
From a Tor User’s Perspective — Simple, Powerful, and Portable
Tor Browser is basically a tweaked version of Firefox that’s built for privacy. For most users, getting started takes almost no technical skill: download the Tor Browser bundle, extract it, and run it. It’s portable, so you can put it on a USB drive or any folder — no messy installs or default system paths.
In short: you can be up and browsing anonymously in about 10 mouse clicks and 10 minutes. If you accept the default settings (which works for most people), configuration is a one-click step. Want to use a bridge or a local proxy? That adds only a few minutes and is still straightforward for most computer users.
So what makes Tor a big deal?
Tor does more than hide your IP address. It gives people a way to communicate and browse with serious anonymity. That’s huge for privacy-minded folks, journalists, activists, and whistleblowers. But the same protections that shield legitimate users also make Tor attractive to criminals and bad actors. With Tor, webmail or other online accounts show only the exit node’s IP, not the real origin. That makes traditional investigative methods—like subpoenas or server logs—far less useful for finding who’s behind an action.
What investigators and forensic analysts should know
When you’re looking into Tor, there are two realistic angles:
Device-focused: Examine the computer, phone, or external media for Tor artifacts — installation files, user profiles, temporary files, or configuration traces. Because Tor is portable, artifacts can appear anywhere on the filesystem or external drives.
Network-focused: Try to link network traffic or capture communications. This is much harder and often requires extraordinary resources, specialized monitoring, or legal cooperation across jurisdictions.
Both approaches are valid, but device artifacts are usually more practical for everyday forensic work. Still, unmasking a Tor user is difficult and sometimes overwhelming.
Use matters more than the tool
Remember: Tor itself is neutral. How people use it determines whether their actions are legitimate or criminal. Businesses may use Tor to research competitors without leaving traces. Journalists and whistleblowers rely on Tor to protect sources. Law enforcement can also benefit from Tor in controlled ways (for example, to view sites without revealing investigative IP addresses). The context and intent behind the activity are what matter.
Forensic Analysis of The Onion Router (Tor)
When performing a digital forensic investigation, one of the first things to check for is the presence of the Tor Browser. Because Tor is a portable application, it can exist anywhere on a device — a USB stick, hidden system folder, or renamed executable buried deep in the file tree. Users who want to conceal their activity often change filenames or locations, so a simple keyword search may not be enough. The fastest way to find it is to look for hash values that match known Tor browser versions.
Identifying Tor Installations
The Tor Project maintains an archive of all past releases, which makes it easy for investigators to build a custom hash set. Downloading these versions lets you detect which Tor version was used, helping to estimate how long the suspect has been using Tor. A seasoned Tor user tends to update frequently to avoid vulnerabilities, which can also tell you about their technical awareness and habits.
The Challenge of Browser Artifacts
Traditional browsers store rich forensic data — browsing history, cookies, cache, and registry traces — but Tor doesn’t. It’s designed for privacy, so it leaves little to no Internet history in system files like NTUSER.DAT. The only reliable way to capture live browsing activity is through a memory dump (RAM acquisition). Even then, Tor data in memory vanishes seconds after closing the browser, so investigators must act immediately when encountering a live Tor session.
Some artifacts still provide limited insight:
Windows paging file (C:pagefile.sys)
Cache and thumbcache databases showing Tor icons or references
Explorer cache (thumbcache_32.db, IconCache.db, etc.)
Registry paths like UsrClass.dat revealing Tor installation folders
You might also recover URLs by searching pagefile data for the string HTTP-memory-only-PB or keywords like torproject.
Useful Files & System Clues
Within the Tor browser directory, the state file shows the last execution date and time, while the torrc file logs the path or drive where Tor was executed. The Windows Prefetch folder can also confirm installation and usage times, revealing when Tor was first launched and how many times it’s been run.
Example (Prefetch data):
Filename: TOR.EXE-4FD90956.pf
Created: 9/20/2015 12:05:30 PM
Process Path: C:UserssuspectDesktopTOR BROWSERBrowserTortor.exe
Last Run Time: 9/20/2015 12:05:20 PM
Cross-checking Prefetch timestamps with USB device connections can uncover suspicious activity—like a flash drive plugged in moments after Tor started, suggesting possible data exfiltration.
The Takeaway for Investigators
While Tor doesn’t leave behind as many digital breadcrumbs as standard browsers, there’s still forensic value:
Install/first-use/last-use timestamps
Version history and update patterns
Potential memory remnants or pagefile data
Clues from system files and attached devices
The mere presence of Tor on a system should trigger deeper investigation into possible anti-forensic behavior or hidden communications. With tools like Volume Shadow Copy analysis, it’s often possible to reconstruct partial timelines of Tor usage and correlate them with other system events.
IT’S PORTABLE!
The Tor browser can run from almost anywhere.
Remember, the Tor browser is portable, meaning that no installation is necessary. This also means that it can run from external devices, such as a flash drive or external hard drive, and may have never been installed (extracted) onto a system’s hard drive. When Tor is run from an external device, you can expect even fewer artifacts to remain, but this certainly does not make looking for Tor artifacts less important.
TRACKING CRIMINALS USING TOR
By now you understand the difficulty in tracking Tor users, but do not feel alone — practically every government agency is working on deanonymizing Tor to either find criminals and terrorists or prohibit citizens from accessing the Internet. A few successes have made national news, but for the most part, the breaks in those cases were not due to breaking Tor itself but rather exploiting errors made by suspects. Like the majority of investigators, having access to federal resources to investigate criminals using Tor is most likely not possible. Unless you have a terrorist connection to a case, you are on your own to investigate without the National Security Agency.
IT’S POSSIBLE TO BREAK TOR!
The FBI did it…once…at least once…
A child pornography hosting service was identified and taken down by the FBI using an exploit of Firefox. The FBI infected the servers at Freedom Hosting, which in turn infected the Tor browsers of visitors to the criminal websites. The exploit (Firefox bug CVE-2013-1690 in version 17 ESR) captured the true IP address, MAC address, and Windows hostname from the Tor browser exploit. This information was then sent to the FBI until the exploit was discovered and patched. Linux Tor users and those who had used updated versions of Tor were apparently unaffected (The FBI TOR Exploit).
One of the weaknesses — if not the biggest weakness — of the Tor browser is the user. As the browser is preconfigured with security in mind, customization is not recommended. In fact, the best thing a Tor user can do is not to change any settings of the browser, because any setting can leak information out of Tor. A simple example is geolocation: some websites ask if you will allow your location to be shared. A Tor user should always choose “never,” but as investigators we rely on mistakes and hope these types of modifications are made by criminals.
Other risky customizations revolve around media and interactivity: video and animation usually require plugins to be installed and active; these very plugins can allow the true IP address to be collected. Tor users who routinely allow scripts, Java, and other website requests to run in the browser risk having their IP addresses captured by those sites. But how does that help you? It helps because investigators can exploit those mistakes.
The amount of research conducted on Tor to find vulnerabilities, identify users, and decrypt data has been ongoing for years. Some researchers have even theorized deanonymizing Tor by attacking and disabling a large percentage of the Tor network to identify users (Jansen, Tschorsch, Johnson, & Scheuermann, n.d.). Other theories include gaining control of as many entry and exit nodes as possible to correlate traffic and identify users. Even if several entry (guard) nodes are controlled, the Tor network does not automatically use new entry nodes for weeks at a time to reduce the threat of compromised entry nodes. Entry nodes are also rotated regularly. So, to control entry nodes in hopes that your suspect’s Tor circuit uses them is slim. On top of that, if the communications are encrypted end-to-end, capturing the traffic does not decrypt the contents of messages.
The man-in-the-middle attack is yet another method to bypass the security of Tor users by interjecting a capture service between the Tor user and destination. Nation-states have the resources for these types of attacks on Tor, but even then, compromising Tor is very difficult.
Each of these methods requires more resources and time than will ever be given to the common criminal unless special situations exist, such as a terror connection. Even then, the number of agencies with access to such resources is very few. Given that, the few remaining practical methods rely on the suspect and the suspect’s errors.
The most common goal of any Internet-related investigation is obtaining the true IP address. With the true IP address, traditional investigative methods can corroborate, verify, and potentially seize physical evidence and suspects at that location. The trick is getting the IP address when Tor makes it extremely difficult.
Depending upon the investigation, you may have access to one end of the communication, such as that of a victim. When a victim receives harassing or threatening e-mails, the potential to capitalize on the suspect’s mistakes increases. For example, an e-mail can be seeded with a tracking code and sent by the victim to the suspect. Once the e-mail is opened by the suspect, the tracking code can obtain the true IP address and send it to the investigator. The success depends on a couple of factors. One is the e-mail service being used and its configuration. If the e-mail (webmail) allows HTML, then the tracking script may work without alerting the suspect. However, if not, the suspect will be immediately notified that a script has been placed in the e-mail and will not be allowed to run. This method is risky as it will tip off the suspect that the e-mail may be compromised.
Another method with less risk of notifying the suspect is placing a tracking code in a document that is e-mailed to the suspect. Documents need to be downloaded and opened for viewing, usually outside the browser. When the document is opened outside the browser, the tracking code can obtain the true IP address which is sent to the investigator. There are few, if any, warnings given to a computer user that opens a document with an IP address tracking code. Tor itself warns that downloading documents can be dangerous and recommends opening downloaded documents safely, offline, or in a virtual machine to prevent the IP address from being captured.
When these methods are ineffective or may cause too much risk of compromise, identifying the Tor user outside of the Tor network may be possible. In this approach, using all of the information you have on your suspect requires open-source and online investigative methods. Basically, finding your suspect on the clear web can help identify the suspect on the dark web. Even if the only information you have on the suspect is a username, it may be enough to lead to more information otherwise unobtainable.
ONE MISTAKE RESULTS IN A LIFETIME IN PRISON
One Weak Strand of the Silk Road Caused the Crash
Silk Road founder Ross Ulbricht made one crucial mistake: he used his personal e-mail address and real name on the open Internet to request help building a Bitcoin venture. That single slip gave federal agents the connection they needed to link his real identity to his previously anonymous Dark Web profile (Bradbury, 2013). Today, he’s serving a life sentence. While this wasn’t the only evidence used in the case, it shows how one careless action can unravel total anonymity and make an investigator’s job much easier.
Investigations inside corporate networks have a unique advantage. When Tor traffic occurs within an internal environment, network administrators can detect the use of Tor, even though they can’t see the encrypted content. Simply identifying who is using Tor on the network can be enough to narrow suspects. For instance, if a victim suspects a co-worker and the IT department logs that employee accessing Tor between 3:30 p.m. and 3:40 p.m.—the same period the victim receives a threatening e-mail—the correlation can tie the activity to a specific system or user.
BUT MOM, I DON’T WANT TO TAKE THE EXAM!
How a Harvard Student Was Busted Using Tor
In 2013, Harvard student Eldo Kim used Tor to send e-mail bomb threats to Harvard staff in an attempt to avoid taking an exam. Harvard’s IT staff reviewed their logs and identified Kim as having accessed Tor on the campus network at the exact time the e-mails were sent (Dalton, 2013). When confronted by the FBI, Kim admitted everything. Tor itself worked perfectly—but Kim’s operational mistake broke his anonymity.
Most Tor-related cases are solved because of such user errors. Even a technically skilled suspect can slip up—perhaps using a regular browser instead of Tor for one message, or sending a test e-mail through a non-Tor connection. These small oversights expose the user’s true IP address, giving investigators the crucial lead they need.
USED IN COMBINATION WITH OTHER TOOLS AND METHODS
Tor alone provides strong anonymity, but when it’s paired with other security layers, it becomes even more powerful. Since the final hop in the Tor network (the exit node) sends traffic unencrypted, that data could theoretically be intercepted. However, when users combine Tor with end-to-end encryption, both anonymity and confidentiality are protected. Even if both endpoints are identified, the message contents remain unreadable.
Users can further protect themselves by using Tor on a non-owned computer connected to a non-owned network—for example, browsing from a public library, café, or hotel lobby. In these cases, both the device and the network leave no personal footprint, making it nearly impossible to trace activity back to the original user.
When used responsibly, Tor remains a legitimate privacy tool. But in the wrong hands, the smallest operational error—an e-mail address, a browser misstep, or a network log—can destroy that anonymity and lead to arrest.
Tails — The Amnesic Incognito Live System
While Tor Browser offers anonymous browsing, Tails (The Amnesic Incognito Live System) takes online privacy to the next level. Tails is a complete live operating system based on Debian/Linux, designed for total anonymity and security. It runs directly from a DVD, USB flash drive, or SD card and doesn’t require installation on a hard drive.
Within Tails, Tor Browser comes preinstalled and preconfigured, offering the same privacy benefits described earlier—but with additional protection.
How Tails Works
To use Tails, a computer must be able to boot from an external device containing the Tails OS. Once booted, the user simply connects to the internet, and Tor Browser can be launched immediately.
The major difference between using Tor on Windows and using Tails is that Tails leaves no forensic traces on the host computer. It runs entirely in RAM and doesn’t interact with or modify the hard drive. This means forensic analysts won’t find Tor artifacts, browsing history, or memory dumps like pagefile.sys or hiberfil.sys. Furthermore, live memory is wiped clean on shutdown. Even when Tails is run from a writable USB drive, data is not stored or saved to that drive.
Advanced Booting and ISO Usage
Tails can also be run without external media. On Linux systems, the boot loader (GRUB2) can be configured to launch directly from a stored ISO image on the host hard drive. This allows the system to boot Tails without external devices while leaving no traceable data on the system drive.
A single hard drive can hold multiple live ISO files, such as Tails or other live operating systems, which can be booted directly. These “live CDs” enable full OS functionality without using the internal hard drive.
From an investigative standpoint, forensic analysts should always check the boot loader configuration to determine if a system was set up to boot from stored ISO images. This can explain discrepancies between user activity and missing system logs or metadata. If a system shows user file access without standard OS timestamps, it may indicate booting from a live ISO or external OS like Tails.
Security Features in Tails
Tails offers far more than just a Tor Browser. It includes:
Encryption tools for files and communications.
Encrypted chat and secure messaging options.
An office suite for document creation.
MAC address spoofing for network anonymity.
A virtual keyboard to prevent keylogger attacks.
Everything in Tails is optimized for portability, security, and ease of use. Upon startup, users can choose between a standard Linux desktop or a camouflage mode that mimics the Windows interface to avoid suspicion in public environments.
Forensic analysis of systems that only used Tails will reveal no artifacts if it was booted externally. However, its effectiveness depends on the computer’s BIOS or UEFI allowing external booting. Many institutions (like libraries or schools) disable external booting for security reasons.
Related Tor Tools and Applications
Because of Tor’s effectiveness, numerous third-party tools and hardware devices have been developed to enhance or automate Tor connectivity.
The Anonabox
One notable example is the Anonabox — a hardware router that automatically directs all internet traffic through the Tor network. Unlike the Tor Browser, which only routes specific traffic, Anonabox secures every outgoing connection.
Such devices can be highly relevant in forensic investigations, as they ensure all web browsers and apps use Tor routing. However, in 2015, Anonabox issued a mass recall due to security flaws, even though the Tor network itself remained uncompromised (Greenberg, n.d.).
Mobile Tor Applications
Mobile versions of Tor are gaining traction as privacy-focused smartphone apps.
For example, Orbot forces all Android device traffic through Tor, encrypting data and routing it across worldwide relays. This adds a new level of anonymity for mobile communications, allowing prepaid “burner phones” to send untraceable messages through Tor before being discarded.
As mobile privacy tools evolve, it’s expected that more mobile operating systems will integrate Tor routing natively, further complicating digital investigations.
Hidden Services and the Dark Web
One of the most powerful and controversial aspects of the Tor network is Hidden Services—servers that operate entirely inside the Tor network.
Hidden services provide end-to-end encryption and are not indexed by search engines. Because they don’t use exit nodes, no part of the communication is exposed to the open internet. Accessing them requires the Tor Browser, and their domains typically end in “.onion” (e.g., http://dppmfxaacucguzpc.onion/).
Setting up a hidden service is straightforward and can be done in a few hours, making them ideal for covert communications or dark web marketplaces. Some are publicly listed in directories, while others remain private, accessible only to specific individuals.
Browser plugins exist to let standard browsers reach .onion sites, but doing so exposes the user’s true IP address, defeating Tor’s anonymity. For investigators, this presents both a risk and an opportunity: accessing such sites from identifiable networks can reveal the investigator’s location if not properly anonymized.
Hidden services often host illegal or restricted content, including:
Drug and firearm marketplaces.
Stolen financial data and credit cards.
Fake identification documents.
Explicit and illegal materials.
The screenshot illustrates one such directory listing products like “Silk Road 3.0,” which emerged after the original Silk Road’s shutdown.
Investigating the Dark Web requires more than just tracing IP addresses — it demands traditional intelligence methods, infiltration, and long-term digital profiling to uncover networks and operators.
The post Tor Browser Explained: How Anonymous Browsing Works and Why It Matters appeared first on Codelivly.
No Responses