There are many systems that track and record network activities and data. However, there are still some measures that add up to the forensics on network systems. Network forensics adds vital information to investigations. Tools can be used to do timeline analysis, email reconstruction, metadata analysis, packet frame analysis, or checksum on data exchanged.
Another aspect of network forensics is to make or get capabilities of capturing and investigating a suspect’s computer over a network. There are methods of making an image of a suspect’s or victim’s computer over a network connection from the forensics lab itself. However, legal aspects must be considered before capturing or intruding over another system.
Network forensics is a sub-branch of digital forensics relating to the monitoring and analysis of computer network traffic for the purposes of information gathering, legal evidence, or intrusion detection. Unlike other areas of digital forensics, network investigations deal with volatile and dynamic information. Network traffic is transmitted and then lost, so network forensics is often a proactive investigation.
Network forensics generally has two uses. The first, relating to security, involves monitoring a network for anomalous traffic and identifying intrusions. An attacker might be able to erase all log files on a compromised host; network-based evidence might therefore be the only evidence available for forensic analysis.
The second form relates to law enforcement. In this case, analysis of captured network traffic can include tasks such as reassembling transferred files, searching for keywords, and parsing human communication such as emails or chat sessions.
In 2000, the FBI lured computer hackers Aleksey Ivanov and Gorshkov to the United States for a fake job interview. By monitoring network traffic from the pair’s computers, the FBI identified passwords allowing them to collect evidence directly from Russian-based computers.
1. Network Components and their forensics importance
A computer network, or data network, is a telecommunications network that allows computers to exchange data. In computer networks, networked computing devices exchange data with each other along network links (data connections). These connections between nodes are established using either cable media or wireless media. The best-known computer network is the Internet.
Network computer devices that originate, route, and terminate the data are called network nodes. Nodes can include hosts such as personal computers, phones, servers, as well as networking hardware. Two devices can be considered networked when one device can exchange information with the other, whether or not they have a direct connection.
Computer networks can differ in several ways:
Transmission Media – The medium used to carry network signals (wired or wireless).
Communication Protocols – The rules that organize and manage network traffic.
Size and Topology – The network’s physical or logical layout.
Organizational Intent – The purpose for which the network is built (home, enterprise, public).
In most cases, communication protocols are layered on top of other more specific or general protocols, except for the physical layer, which directly deals with the transmission media.
Computer networks support a variety of applications, including:
Access to the World Wide Web
Shared use of application and storage servers
Shared use of printers and fax machines
Email and instant messaging services
1.1 Host
A network host is a computer or other device connected to a computer network. A network host may offer information resources, services, and applications to users or other nodes on the network. A network host is a network node that is assigned a network layer host address.
Computers participating in networks that use the Internet Protocol Suite may also be called IP hosts. Specifically, computers participating in the Internet are called Internet hosts (or sometimes Internet nodes). Internet hosts and other IP hosts have one or more IP addresses assigned to their network interfaces. These addresses can be configured in different ways:
Manually by a network administrator
Automatically at startup using the Dynamic Host Configuration Protocol (DHCP)
Stateless Address Auto-Configuration methods
Every network host is a physical network node (i.e., a network device), but not every physical network node is a host. For example, network devices such as modems, hubs, and network switches are not assigned host addresses (except sometimes for administrative purposes) and are therefore not considered network hosts. Devices such as network printers and hardware routers may have IP addresses, but since they are not general-purpose computers, they are sometimes not considered hosts.
Network hosts that participate in applications using the client–server model are classified as either server systems or client systems. Network hosts can also act as nodes in peer-to-peer applications, where all nodes share and consume resources equally.
In operating systems, the term terminal host traditionally refers to a multi-user computer or software providing services to computer terminals, or a computer that provides services to smaller or less capable devices—such as a mainframe computer serving teletype terminals or video terminals. Other examples include a telnet host (telnet server) and an xhost (X Window client).
1.2 Node
In data communication, a physical network node may either be:
Data Communication Equipment (DCE): Devices such as modems, hubs, bridges, or switches.
Data Terminal Equipment (DTE): Devices such as digital telephone handsets, printers, or host computers (e.g., routers, workstations, or servers).
If the network in question is a LAN or WAN, every LAN or WAN node (that is at least a data link layer device) must have a MAC address, typically one for each network interface controller it possesses. Examples include:
Computers
Packet switches
xDSL modems (with Ethernet interfaces)
Wireless LAN access points
Note: A hub constitutes a physical network node but not a LAN network node, since a hubbed network is logically a bus network. Similarly, a repeater or PSTN modem (with serial interface) is a physical network node but not a LAN node in this sense.
If the network in question is the Internet or an Intranet, many physical network nodes are host computers (also called Internet nodes), identified by an IP address. All hosts are physical network nodes. However, some data link layer devices—such as switches, bridges, and WLAN access points—do not have IP host addresses (except sometimes for administrative purposes). These are considered physical and LAN nodes, but not Internet nodes or hosts.
If the network in question is a distributed system, the nodes can be:
Clients
Servers
Peers (which may sometimes act as clients, sometimes as servers)
In a peer-to-peer or overlay network, nodes that actively route data for other networked devices as well as themselves are called super nodes.
Distributed systems may also use virtual nodes to handle the heterogeneity of physical nodes. This is often managed with special algorithms such as consistent hashing, as is the case in Amazon’s distributed systems.
1.3 Router
A router is a networking device that forwards data packets between computer networks. Routers perform the “traffic directing” functions on the Internet. A data packet is typically forwarded from one router to another through the networks that constitute the internetwork until it reaches its destination node.
A router is connected to two or more data lines from different networks (unlike a network switch, which connects data lines from a single network). When a data packet arrives on one of the lines, the router reads the address information in the packet to determine its ultimate destination. Then, using information from its routing table or routing policy, it directs the packet to the next network on its journey. This process creates an overlay internetwork.
The most familiar type of routers are home and small office routers, which simply pass data such as web pages, emails, instant messages, and videos between home computers and the Internet. An example of this is a cable or DSL router that connects to the Internet through an ISP.
More sophisticated routers, such as enterprise routers, connect large business networks or ISP networks to the core routers, which forward data at high speed along the optical fiber lines of the Internet backbone.
Although routers are typically dedicated hardware devices, the use of software-based routers has become increasingly common.
1.4 Switch
A network switch (also called a switching hub, bridging hub, or officially a MAC Bridge) is a computer networking device that connects devices together on a computer network by using packet switching to receive, process, and forward data to the destination device.
Unlike less advanced network hubs, a network switch forwards data only to the device or devices that need to receive it, rather than broadcasting the same data out of all its ports.
A network switch is essentially a multiport network bridge that uses hardware (MAC) addresses to process and forward data at the data link layer (Layer 2) of the OSI model. Some switches can also process data at the network layer (Layer 3) by incorporating routing functionality—most commonly using IP addresses to perform packet forwarding. Such devices are known as Layer-3 switches or multilayer switches.
A switch electrically and logically connects multiple devices in a computer network. Multiple data cables are plugged into the switch, enabling communication between the connected devices. The switch manages the flow of data by transmitting a received message only to the one or more devices for which it was intended.
Each networked device connected to a switch can be identified using a MAC address, allowing the switch to regulate traffic flow, maximize efficiency, and enhance network security.
1.5 Hub
An Ethernet hub—also known as an active hub, network hub, repeater hub, multiport repeater, or simply hub—is a device used for connecting multiple Ethernet devices together and making them act as a single network segment.
A hub has multiple input/output (I/O) ports. When a signal is introduced at the input of any port, it appears at the output of every other port except the one it came from. A hub operates at the physical layer (Layer 1) of the OSI model.
Repeater hubs also participate in collision detection. If a collision is detected, they forward a jam signal to all ports.
In addition to standard 8P8C (“RJ45”) ports, some hubs may include BNC or Attachment Unit Interface (AUI) connectors to allow connection to legacy 10BASE2 or 10BASE5 network segments.
Hubs are now largely obsolete, having been replaced by network switches in most modern networks, except in very old installations or in specialized applications.
1.6 Network interface Card (NIC)
A Network Interface Controller (NIC)—also known as a network interface card, network adapter, LAN adapter, or physical network interface—is a computer hardware component that connects a computer to a computer network.
The NIC usually holds the MAC (Media Access Control) address of your computer, which uniquely identifies your host or computer on the network. It serves as the physical bridge between the network and the host.
A common example is the port on the back of your computer with a cable resembling an oversized phone jack and blinking lights—this is your NIC.
Discover: Mastering Networking Fundamentals: A Comprehensive Guide for Hackers
2. OSI
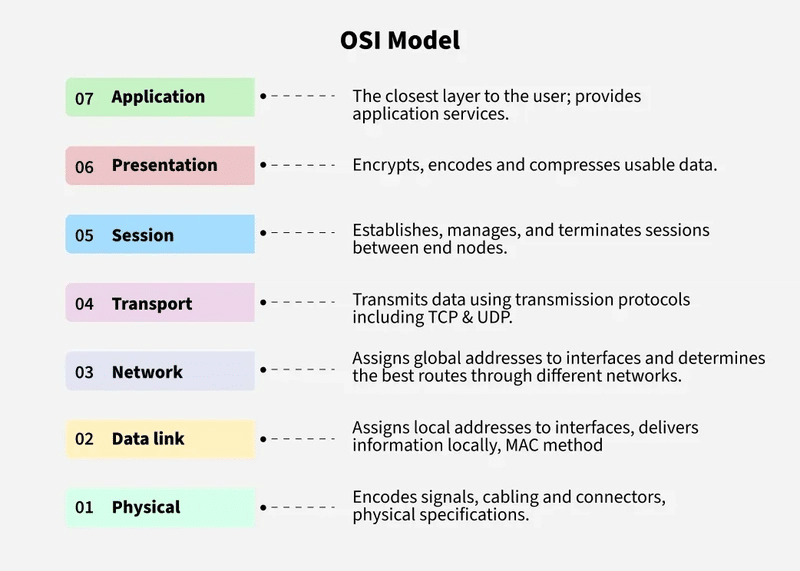
The Open Systems Interconnection (OSI) Model is a conceptual framework that characterizes and standardizes the communication functions of a telecommunication or computing system, regardless of its underlying internal structure or technology. Its primary goal is to ensure interoperability between diverse communication systems using standard protocols.
The OSI model divides a communication system into a series of abstraction layers. The original version of the model defined seven layers.
Each layer serves the layer above it and is served by the layer below it. For example, a layer that provides error-free communication across a network offers the path needed by the application layers above it, while it relies on the layer below to send and receive the data packets that make up that communication.
Two instances operating at the same layer on different devices are visualized as being connected by a horizontal connection within that layer, showing how they interact logically
2.1 OSI model
The OSI (Open System Interconnection) is a standard logical view of any networking. It has 7 layers as given in Figure . this also depicts various form of data formats that are exchanged between each layers of either side in a connectivity. It also gives main functionalities of each layer as abstracted.
2.1 TCP/IP Layers
Although the OSI model is widely used and often cited as the standard, the TCP/IP protocol suite has been adopted by most UNIX workstation vendors and is the foundation of the Internet.
TCP/IP is designed around a simple four-layer scheme. It omits some features found in the OSI model, combines certain OSI layers, and splits others apart. The four network layers defined by the TCP/IP model are:
Layer 1 – Link Layer: Defines the network hardware and device drivers.
Layer 2 – Internet Layer: Handles basic communication, addressing, and routing. Protocols such as IP (Internet Protocol) and ICMP (Internet Control Message Protocol) operate at this layer.
Layer 3 – Transport Layer: Provides communication between programs on a network. TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) belong to this layer.
Layer 4 – Application Layer: Hosts end-user applications. Common examples include NFS, DNS, ARP, rlogin, talk, FTP, NTP, and traceroute.
The Internet Protocol Suite is the computer networking model and set of communication protocols used on the Internet and most modern networks. Commonly referred to as TCP/IP (from Transmission Control Protocol and Internet Protocol), it provides end-to-end connectivity, specifying how data should be:
Packetized
Addressed
Transmitted
Routed
Received at the destination
This functionality is organized into four abstraction layers, which group related protocols according to the scope of networking involved:
Link Layer: Communication technologies for a single network segment (link).
Internet Layer: Connects hosts across independent networks, enabling internetworking.
Transport Layer: Manages host-to-host communication.
Application Layer: Provides process-to-process data exchange for applications.
Two Internet hosts can be connected through multiple routers, with communication happening across corresponding protocol layers at each hop. The application on each host performs read and write operations as if the processes were directly connected through a seamless data pipe. All the complexity of the communication—such as packet transmission, routing, and error handling—is hidden from the applications.
The underlying mechanisms that handle data transmission, routing, and delivery between the host computers are implemented in the lower protocol layers, allowing applications to focus solely on exchanging data without worrying about network details.
Applying forensic methods at the Ethernet layer involves eavesdropping on bit streams using monitoring tools or sniffers. The most common tools for this are Wireshark (formerly known as Ethereal) and tcpdump. While tcpdump is mostly used on Unix-like operating systems, both tools can capture all data at this layer and allow the user to filter for specific events.
With these tools, websites, email attachments, and other network traffic can be reconstructed — but only if the data is transmitted or received unencrypted. An advantage of collecting data at this layer is that it is directly tied to a specific host. If an investigator knows the IP address or MAC address of a host at a given time, all data sent to or from that address can be filtered and analyzed.
To link IP addresses with MAC addresses, investigators often examine Address Resolution Protocol (ARP) tables, which list MAC addresses and their corresponding IP addresses. For capturing data at this layer, a network interface card (NIC) can be set to promiscuous mode, allowing it to pass all network traffic to the CPU — not just the traffic intended for that host.
However, attackers aware of potential monitoring may use encryption to secure their communications. While modern encryption is extremely difficult to break, the fact that a suspect’s connection is always encrypted can itself be a valuable clue — it may indicate communication with a specific remote host, potentially an accomplice.
On the network layer, the Internet Protocol (IP) is responsible for directing packets through the network by adding source and destination information that routers can interpret. Cellular data networks like GPRS use similar protocols, so the same forensic techniques apply.
For routing to work correctly, every router maintains a routing table to determine where to send packets next. These routing tables can provide crucial evidence when tracking down an attacker. Investigators can follow the attacker’s packet path in reverse to locate the computer the packets originated from.
The Internet itself is a rich source of digital evidence — including web browsing history, email, newsgroup posts, chat sessions, and peer-to-peer traffic. For instance:
Web server logs can confirm whether a suspect accessed incriminating information.
Email accounts often contain valuable evidence, though headers can be forged — network forensics can help verify the real source.
Network forensics can also identify who was using a computer by extracting user account information from captured network traffic.
Discover: How Hackers Are Using Backdoors To Access Networks
3. Forensics Information From Network
In network forensics, major sources of information include: hosts, routers, firewalls, switches, intrusion detection and prevention systems, network printers/copiers, and wireless access points. Investigators need to collect data from these sources, and categorizing and analyzing this data correctly is crucial.
1. Hosts
Forensic investigations often use agents (software) installed on hosts to gather and transmit data to a remote forensic server. These agents capture real-time data streams passing through the host’s Network Interface Card (NIC) for analysis.
2. Routers
Router logs are highly valuable in many investigations. They contain information such as:
Status details and errors
IP and MAC address mappings
Traffic routes between networks or hosts
This data can help trace a suspect and reconstruct the sequence of events during a crime investigation.
3. Firewalls
Firewalls maintain detailed logs of network activity including:
Dropped packets
Unauthorized application access
Filtered websites
Recognized attacks
Logs from either a host firewall or a network firewall can often provide enough information to trace connections to suspicious activity or criminal behavior.
4. Switches
Switches contain a Content Addressable Memory (CAM) table that stores:
Mappings of MAC addresses to ports
VLAN information
Two popular methods used to monitor network traffic through switches are:
Port Mirroring: The switch sends a copy of network packets to a monitoring network connection for analysis.
SMON (Switch Monitoring): Defined in RFC 2613, SMON is a protocol for controlling switch monitoring facilities such as port mirroring.
3.1 Intrusion detection/ prevention system
An intrusion detection system (IDS) is a device or software application that monitors network or system activity to identify malicious behavior or policy violations, producing reports for a management station. IDS technologies come in several forms and pursue the same goal—detecting suspicious traffic—through different approaches. Broadly, they are categorized as network-based IDS (NIDS) and host-based IDS (HIDS). NIDS examines traffic flowing across a network and can detect threats originating both outside and inside the organization, including activity by authorized users that violates policy. HIDS, in contrast, operates on individual hosts, inspecting system calls, file integrity, and local logs to surface signs of compromise. While some solutions attempt to automatically block threats, active intervention is not required of an IDS, whose primary role is monitoring and alerting. Intrusion detection and prevention systems (IDPS) extend this concept by not only identifying and logging potential incidents but also taking preventive actions to stop or contain them.
Although both IDS and firewalls are foundational to network security, they serve distinct purposes. A firewall acts as a gatekeeper, enforcing access rules between networks to prevent unauthorized connections and traffic from entering in the first place; it does not typically signal attacks that originate within the protected environment. An IDS, by contrast, analyzes events to determine whether an intrusion has occurred or is underway and generates alerts when suspicious activity is detected. In doing so, it provides visibility into both external threats that have evaded perimeter defenses and internal attacks that originate from within a system or network segment.
The logs produced by IDS and IDPS tools are invaluable for network forensics. They supply timelines, indicators of compromise, and contextual details that help analysts reconstruct events and understand attacker behavior. Moreover, other network-connected devices—such as printers and copiers—often maintain their own activity logs. While the depth and quality of this logging vary by manufacturer, these auxiliary records can corroborate IDS findings and enrich investigations, ultimately strengthening an organization’s incident response and security posture.
3.2 Wireless Access Points
Wireless access points (WAPs) can also play an important role in investigations because they maintain logs of routing-related activity—such as broadcast SSIDs, association and authentication events, and incoming connection attempts. Given the sheer volume of traffic flowing into and out of modern networks, it is essential to plan for log storage and retention from the outset: how the logs will be collected, where they will be stored, how long they will be retained, and how they will be protected for later analysis and potential evidentiary use.
Investigators and administrators can leverage bulk-storage options such as storage-area networks (SAN), network-attached storage (NAS), and direct-attached storage (DAS) to house large log datasets reliably and cost-effectively. Traditional tape systems also remain relevant for long-term, large-scale archival due to their durability and favorable cost per terabyte, and they continue to play a vital role in mass storage and evidence preservation.
4. LOG Analysis
The analysis of large volumes of data collected from Intrusion Detection and Prevention Systems (IDPS) is typically performed in a separate database system managed by the analysis team. Live production systems are generally not equipped to handle extensive forensic analysis without impacting regular users. Analyzing copies of the data on separate systems also helps protect the integrity of the original data and avoids accusations of data tampering.
Due to the nature of the data, forensic analysis often focuses more on the content of the data rather than the database itself. If the database structure or its contents are of interest, database forensics may be applied.
Expertise Required for Analysis
Analyzing large, structured datasets—especially for detecting financial crimes—typically requires a multidisciplinary team:
Data Analyst: Performs technical steps, queries, and initial data exploration.
Process Expert: Has extensive knowledge of the processes and internal controls within the relevant organization.
Forensic Scientist: Experienced in recognizing patterns of fraudulent or criminal behavior.
Analysis Process
The forensic analysis process is often iterative:
Exploratory Data Analysis: Initial investigation to detect anomalies or patterns.
Hypothesis Formation: Investigators form hypotheses on how a perpetrator may have acted to gain an advantage.
Evidence Search: The data is analyzed to find supporting evidence for the hypothesis.
Hypothesis Refinement: Based on the findings, hypotheses are either refined or discarded.
Combining data from different databases or sources is highly effective because these data sources are often unknown to the perpetrator or cannot be manipulated after the fact. Data visualization tools are commonly used to display results and patterns effectively.
Log Analysis Activities
While there are many tools available for analyzing logs captured from hosts, routers, firewalls, switches, and other network devices, understanding the analysis methodology is essential for recreating criminal events. Major activities during log analysis include:
Analyzing timestamps to determine the sequence of events
Analyzing data to identify anomalies, patterns, and potential evidence
4.1 Analyzing time stamps
Time and its synchronization in a network are critical for accurate forensic analysis. Smart criminals may attempt to manipulate timestamps in their communications to mislead investigations.
However, technologies like the Network Time Protocol (NTP) have largely minimized this risk. Before beginning an analysis, investigators must determine whether NTP has been implemented on the systems under investigation.
Network Time Protocol (NTP) is a networking protocol designed for clock synchronization between computer systems over packet-switched, variable-latency data networks. In operation since before 1985, NTP is one of the oldest Internet protocols still in use today.
NTP was originally developed by David L. Mills of the University of Delaware, who continues to oversee its development. The protocol is designed to synchronize all participating computers to within a few milliseconds of Coordinated Universal Time (UTC), ensuring accurate and reliable timestamps across networked systems.
4.2 Analyzing data
In Transmission Control Protocol/Internet Protocol (TCP/IP) networks, data is divided into pieces called packets for transport over the network. These packets are reassembled at the receiving end.
Since different packets of the same message may take different paths through the network, reassembling them can be complex. To address this, TCP/IP uses a sequence numbering mechanism:
Each packet is assigned a sequence number.
The receiver acknowledges the packets based on their sequence numbers.
The sending host reconstructs the message once all packets are acknowledged.
The timestamps in these acknowledgment packets are recorded in GMT (UTC) format, providing crucial information for forensic analysis.
Key Network Protocols and Their Forensic Relevance
Understanding various network protocols is essential in network forensics. Important protocols include:
Address Resolution Protocol (ARP): Maps MAC addresses to IP addresses and vice versa. Useful for tracing devices in an investigation.
Internet Control Message Protocol (ICMP): Used for network diagnostics and error reporting.
Internet Protocol Security (IPSec): Provides secure IP communication and encryption.
BitTorrent: Peer-to-peer file sharing protocol, often relevant in digital evidence cases.
Domain Name System (DNS): Translates domain names into IP addresses.
Dynamic Host Configuration Protocol (DHCP): Assigns IP addresses to devices dynamically.
File Transfer Protocol (FTP): Transfers files over a network.
HyperText Transfer Protocol (HTTP): Foundation of data communication on the web.
Internet Message Access Protocol (IMAP): Manages and retrieves emails from a mail server.
Network Time Protocol (NTP): Synchronizes clocks across networked devices.
Post Office Protocol v3 (POP3): Retrieves email from a server.
Secure Shell (SSH): Provides secure remote access to devices.
Simple Mail Transfer Protocol (SMTP): Sends emails across networks.
A strong understanding of these protocols and their operations is critical for reconstructing events and tracing actions during network forensic investigations.
5. Forensics Tools
Technology Tools
These refer to methodologies or techniques used to track, trace, or identify hidden artifacts in network systems.
They provide the framework or approach for gathering evidence from network devices and traffic.
Software Tools
These are software solutions specifically designed to assist in forensic data collection, analysis, and reporting.
Examples include packet sniffers, log analyzers, and forensic suites that facilitate capturing and examining network evidence efficiently.
5.1 Network tools used for forensics
A computer network or data network is a telecommunications network that allows computers to exchange data. In computer networks, networked computing devices exchange data with each other along network links (data connections). The connections between nodes are established using either cable media or wireless media. The best-known computer network is the Internet. Network computer devices that originate, route, and terminate data are called network nodes. Nodes can include hosts such as personal computers, phones, servers, as well as networking hardware. Two devices can be said to be networked together when one device is able to exchange information with the other device, whether or not they have a direct connection. Computer networks differ in the transmission media used to carry their signals, the communications protocols used to organize network traffic, the network’s size, topology, and organizational intent. In most cases, communications protocols are layered on other protocols, except for the physical layer that directly deals with the transmission media. Computer networks support applications such as access to the World Wide Web, shared use of application and storage servers, printers, and fax machines, as well as email and instant messaging applications.
A network host is a computer or other device connected to a computer network. A network host may offer information resources, services, and applications to users or other nodes on the network. A network host is a network node assigned a network layer host address. Computers participating in networks that use the Internet Protocol Suite may also be called IP hosts. Specifically, computers participating in the Internet are called Internet hosts or Internet nodes. Internet hosts and other IP hosts have one or more IP addresses assigned to their network interfaces. These addresses are configured either manually by an administrator, automatically at startup using the Dynamic Host Configuration Protocol (DHCP), or by stateless address auto-configuration methods. Every network host is a physical network node, but not every physical network node is a host. Network devices such as modems, hubs, and network switches are not assigned host addresses (except sometimes for administrative purposes) and are consequently not considered network hosts. Devices such as network printers and hardware routers have IP addresses, but since they are not general-purpose computers, they are sometimes not considered hosts. Network hosts that participate in applications using the client-server model are classified as server or client systems. Network hosts may also function as nodes in peer-to-peer applications, where all nodes share and consume resources equally. In operating systems, the term terminal host traditionally denotes a multi-user computer or software providing services to computer terminals, or a computer that provides services to smaller or less capable devices, such as a mainframe computer serving teletype terminals or video terminals. Other examples include a telnet host (a telnet server) and an xhost (X Window client).
In data communication, a physical network node may either be data communication equipment (DCE) such as a modem, hub, bridge, or switch, or data terminal equipment (DTE) such as a digital telephone handset, printer, or host computer, including routers, workstations, or servers. If the network in question is a LAN or WAN, every node (at least data link layer devices) must have a MAC address, typically one for each network interface controller it possesses. Examples include computers, packet switches, xDSL modems (with Ethernet interfaces), and wireless LAN access points. Note that a hub is a physical network node, but does not constitute a LAN network node, as a hubbed network logically acts as a bus network. Similarly, a repeater or PSTN modem (with a serial interface) is a physical network node but not a LAN node in this sense. If the network is the Internet or an Intranet, many physical network nodes are host computers (Internet nodes), identified by an IP address, and all hosts are physical network nodes. However, some data link layer devices, such as switches, bridges, and WLAN access points, do not have an IP host address (except sometimes for administrative purposes) and are not considered Internet nodes or hosts, but are physical network nodes and LAN nodes. In distributed systems, nodes can be clients, servers, or peers. A peer may sometimes act as a client and sometimes as a server. In peer-to-peer or overlay networks, nodes that actively route data for other devices as well as themselves are called super nodes. Distributed systems may also use virtual nodes so the system accounts for heterogeneity, often using algorithms such as consistent hashing.
A router is a networking device that forwards data packets between computer networks. Routers perform the “traffic directing” functions on the Internet. A data packet is typically forwarded from one router to another through networks until it reaches its destination node. A router is connected to two or more data lines from different networks, unlike a network switch that connects data lines from a single network. When a data packet arrives on one line, the router reads the address information to determine its ultimate destination. Using its routing table or routing policy, it directs the packet to the next network on its journey. The most familiar routers are home or small office routers that simply pass data, such as web pages, email, IM, and videos, between home computers and the Internet. More sophisticated enterprise routers connect large business or ISP networks to core routers that forward data at high speeds along the Internet backbone. Though routers are typically dedicated hardware devices, software-based routers are increasingly common.
A network switch, also called a switching hub or MAC bridge, is a networking device that connects devices on a computer network using packet switching to receive, process, and forward data to the destination device. Unlike network hubs, switches forward data only to the device(s) that need it, rather than broadcasting it to all ports. A network switch is a multiport network bridge that uses hardware addresses to process and forward data at the data link layer (layer 2) of the OSI model. Switches can also process data at the network layer (layer 3) using routing functionality, commonly called layer-3 or multilayer switches. A switch electrically and logically connects devices, with multiple data cables plugged in to enable communication. Switches manage data flow by transmitting a message only to the intended device, with each networked device identified using a MAC address, maximizing network efficiency and security.
An Ethernet hub, also called an active hub, repeater hub, or multiport repeater, connects multiple Ethernet devices and makes them act as a single network segment. A hub has multiple I/O ports, where a signal introduced at any port appears at the output of all other ports except the original. Hubs work at the physical layer (layer 1) of the OSI model. Repeater hubs participate in collision detection, forwarding a jam signal to all ports if a collision is detected. Some hubs also provide BNC or AUI connectors for legacy networks. Hubs are largely obsolete, replaced by network switches except in old or specialized installations.
A network interface controller (NIC), also known as a network interface card or network adapter, is a hardware component that connects a computer to a network. The NIC usually holds the MAC address of the computer, uniquely identifying the host. The NIC serves as the physical bridge between the network and the host.
The Open Systems Interconnection (OSI) model is a conceptual framework that standardizes communication functions of telecommunication or computing systems, regardless of internal technology. Its goal is the interoperability of diverse communication systems using standard protocols. The model partitions communication into abstraction layers. A layer serves the one above it and is served by the one below, providing error-free communication across a network.
Although widely cited, most UNIX systems use TCP/IP, a four-layer model combining and splitting some OSI layers. The four TCP/IP layers are: Link (network hardware and device drivers), Network (communication, addressing, routing using IP and ICMP), Transport (host-to-host communication using TCP and UDP), and Application (end-user applications like NFS, DNS, FTP, SMTP, and more). TCP/IP specifies how data should be packetized, addressed, transmitted, routed, and received.
Applying forensic methods on the Ethernet layer is done by eavesdropping on bit streams using monitoring tools or sniffers. Common tools include Wireshark and tcpdump (mostly on Unix-like systems). These tools collect all data on the layer and allow filtering for specific events. Websites, emails, and other traffic can be reconstructed if unencrypted. Knowing an IP or MAC address allows filtering for all data sent to or from that host. ARP tables help establish IP-MAC mappings. A NIC can be set to promiscuous mode to capture all traffic passing through the network, not just data meant for the host. Encryption by suspects may indicate communication with accomplices.
On the network layer, IP directs TCP packets by adding source and destination information for routers. Cellular networks like GPRS use similar protocols. Routing tables in intermediate routers are crucial for tracing attackers by following packet paths. The Internet can provide evidence from web browsing, emails, chat, and peer-to-peer traffic. Web server logs can show access to criminal information, while network forensics helps verify email origins or identify users on specific computers.
Major information sources include hosts, routers, firewalls, switches, intrusion detection/prevention systems, network printers, copiers, and wireless access points. Data collection and categorization are critical. Hosts often use forensic agents to capture real-time NIC traffic. Router logs provide status, errors, and IP/MAC mapping to trace suspects. Firewalls log network activity, blocked packets, filtered websites, and detected attacks. Switches maintain CAM tables mapping MAC addresses to ports and VLANs. Monitoring methods include port mirroring and SMON (Switch Monitoring).
An intrusion detection system (IDS) monitors network or system activity for malicious actions or policy violations, producing reports for management. IDS types include network-based (NIDS) and host-based (HIDS). IDS differs from firewalls, which prevent unauthorized access; IDS signals attacks after they occur, including from inside the network. IDS logs are valuable for network forensics. Network printers and copiers can also provide activity logs, depending on the manufacturer.
Analysis of large volumes of data from IDPS is typically done on separate database systems to avoid affecting live systems and protect original evidence. The focus is often on data content rather than the database itself. Teams investigating financial crime combine technical data analysts, domain experts, and forensic scientists. Initial exploratory data analysis leads to iterative hypothesis testing, combining multiple data sources to uncover evidence. Data visualization aids understanding. Key log analysis activities include analyzing timestamps and data content.
Time synchronization in networks is crucial. Criminals can falsify timestamps, but Network Time Protocol (NTP) minimizes this risk. Investigators must confirm NTP usage before analysis. NTP synchronizes clocks across systems to within milliseconds of Coordinated Universal Time (UTC).
Data over TCP/IP is broken into packets for transmission and reassembled at the destination. Sequence numbers and acknowledgments ensure proper reconstruction. Timestamps in packets, often in GMT/UTC, provide vital clues. Protocols like ARP, ICMP, IPSec, BitTorrent, DNS, DHCP, FTP, HTTP, IMAP, NTP, POP3, SSH, and SMTP are relevant for tracing and analyzing network activity.
Forensic tools are categorized as technology tools and software tools. Technology tools provide methodologies to trace hidden artifacts in networks, while software tools assist in forensic collection, seizure, and analysis.
Network tap
A network tap is a hardware device that provides a way to access the data flowing across a computer network. It allows third-party monitoring between two points in a network. A tap has three ports: A, B, and a monitor port. Traffic passes through unimpeded while a copy is sent to the monitor port. Network taps are commonly used for NIDS, VoIP recording, network probes, RMON probes, and packet sniffers. They are non-obtrusive, undetectable, support full-duplex and non-shared networks, and usually pass traffic even if the tap loses power. Once installed, monitoring does not interfere with the network. A brief network
5.2 Software tools used for network forensics
5.2.1 Wire shark
Wireshark is a free and open-source packet analyzer used for network troubleshooting, analysis, software and communications protocol development, and education. Originally named Ethereal, it was renamed Wireshark in May 2006 due to trademark issues. Wireshark is cross-platform, using the GTK+ widget toolkit in current releases and Qt in development versions for its user interface, and it relies on pcap to capture packets. It runs on Linux, macOS, BSD, Solaris, other Unix-like systems, and Microsoft Windows. There is also a terminal-based (non-GUI) version called TShark. Wireshark and its associated programs, such as TShark, are free software released under the GNU General Public License. It is very similar to tcpdump but provides a graphical frontend along with integrated sorting and filtering options.
Wireshark allows network interface controllers (NICs) that support promiscuous mode to be placed in that mode, enabling the user to see all traffic visible on the interface, not just traffic addressed to that interface or broadcast/multicast traffic. However, when capturing in promiscuous mode on a port of a network switch, not all traffic passing through the switch is necessarily sent to the capture port. To capture all traffic, port mirroring or network taps can be used.
Wireshark understands the structure (encapsulation) of different networking protocols, allowing it to parse and display packet fields along with their meanings. It uses pcap to capture packets, which limits capture to networks supported by pcap. Key capabilities include:
Capturing data live from the network or reading from files of previously captured packets.
Capturing data from various network types including Ethernet, IEEE 802.11, PPP, and loopback interfaces.
Browsing captured data via a GUI or using the terminal-based TShark.
Editing or converting captured files programmatically via the command-line tool “editcap.”
Refining displayed data using display filters.
Creating plug-ins to dissect new protocols.
Detecting VoIP calls in captured traffic and, if encoded in a compatible format, playing the media flow.
Capturing raw USB traffic.
Wireshark’s native network trace file format is the libpcap format, supported by libpcap and WinPcap, allowing exchange of captured traces with other applications such as tcpdump and CA NetMaster. It can also read captures from other network analyzers, including snoop, Network General’s Sniffer, and Microsoft Network Monitor.
5.2.2 TCPDUMP
Tcpdump is a common command-line packet analyzer that allows users to display TCP/IP and other packets being transmitted or received over a network to which the computer is connected. Distributed under the BSD license, tcpdump is free software.
Tcpdump works on most Unix-like operating systems, including Linux, Solaris, BSD, macOS, HPUX, Android, and AIX. It uses the libpcap library to capture packets. The Windows version of tcpdump is called WinDump and relies on WinPcap, the Windows port of libpcap.
Tcpdump can read packets directly from a network interface card or from previously saved packet files. Captured packets can be printed to standard output or saved to a file for later analysis.
Tcpdump can also be used to intercept and display communications of other users or computers. On systems acting as a router or gateway, a user with the necessary privileges can capture unencrypted traffic, such as Telnet or HTTP, to view login IDs, passwords, URLs, website content, or any other unencrypted information passing through the network.
Summary
Here’s your Summary section cleaned up and polished for consistency with the rest of your network forensics document:
Summary
Network forensics is a sub-branch of digital forensics focused on monitoring and analyzing computer network traffic for information gathering, legal evidence, or intrusion detection.
Network components such as hosts, nodes, routers, switches, hubs, and network interface cards (NICs) must be considered when examining a network forensically.
Understanding the OSI and TCP/IP layers is essential for performing effective network forensics.
Forensic methods at the Ethernet layer involve eavesdropping on bit streams using monitoring tools or packet sniffers such as Wireshark and tcpdump.
Intrusion detection and prevention systems (IDPS) focus on identifying potential incidents, logging relevant information, and reporting attempts. The logs generated by IDS are a critical source of data for network forensics analysis.
Analyzing large, structured datasets—especially for detecting financial crimes—requires a team with at least three types of expertise: a data analyst to perform technical steps and write queries, a team member with extensive knowledge of company processes and internal controls, and a forensic scientist familiar with patterns of fraudulent behavior.
Various tools are used to analyze timestamps and data from logs collected via intrusion detection systems, monitoring tools, and other network components.
Network forensic tools can be classified as technology tools, which provide methodologies to track, trace, or identify hidden artifacts, and software tools, which provide specific solutions for forensic collection and analysis.
Tools can also perform timeline analysis, email reconstruction, metadata analysis, packet/frame analysis, and checksums on exchanged data.
For a deeper dive into networking, TCP/IP, OSI layers, and hands-on cybersecurity exercises, check out our book “Computer Networking & Cybersecurity Essentials”.
The post Network Forensics 101 appeared first on Codelivly.
No Responses