Cybersecurity has become unnecessarily complex. Modern threat actors have refined network infiltration techniques while many organizations continue operating with outdated response methodologies. Traditional security measures are proving insufficient against contemporary attack vectors, particularly advanced persistent threats that operate undetected for extended periods.
Security operations centers process thousands of daily alerts, with most representing false positives. During alert investigation periods, genuine attackers advance deeper into network infrastructure. This scenario resembles locating specific evidence within continuously expanding volumes of irrelevant data.
Deception technology provides a paradigm shift, enabling active adversary misdirection rather than purely defensive postures.
Limitations of Conventional Incident Response
Most organizations function reactively—alerts trigger investigations intended to minimize damage. Attackers often maintain undetected presence for extended periods, with average detection timelines reaching 277 days. This represents nearly nine months of potential compromise before identification.
Alert fatigue significantly impacts threat detection effectiveness. Analysts process excessive volumes of non-actionable notifications, creating conditions where legitimate threats escape notice. Traditional security measures struggle against sophisticated adversaries who deliberately exploit these operational limitations.
Signature-based detection dependencies allow sophisticated adversaries to develop evasion techniques that circumvent conventional security mechanisms. Advanced persistent threats particularly benefit from these detection gaps, maintaining persistence while avoiding traditional security measures designed for known attack patterns.
Efficacy of Deception Technologies
Deception strategies deploy fabricated resources—including counterfeit credentials, decoy systems, and breadcrumb files—designed to attract and capture adversarial interactions. When organizations deploy deception strategically, they create environments where any unauthorized access triggers immediate alerts.
Interactions with these contrived assets generate high-confidence alerts indicating definitive malicious activity. No legitimate operational requirements exist for accessing deceptive resources, making every interaction inherently suspicious. This approach delivers fewer false positives compared to traditional detection methods that struggle with legitimate user behavior patterns.
Contemporary deception implementations incorporate machine learning algorithms that adapt strategies based on observed attacker behaviors, extending coverage across network, endpoint, and cloud environments. These systems enable deception technology detect capabilities that surpass conventional signature-based approaches.
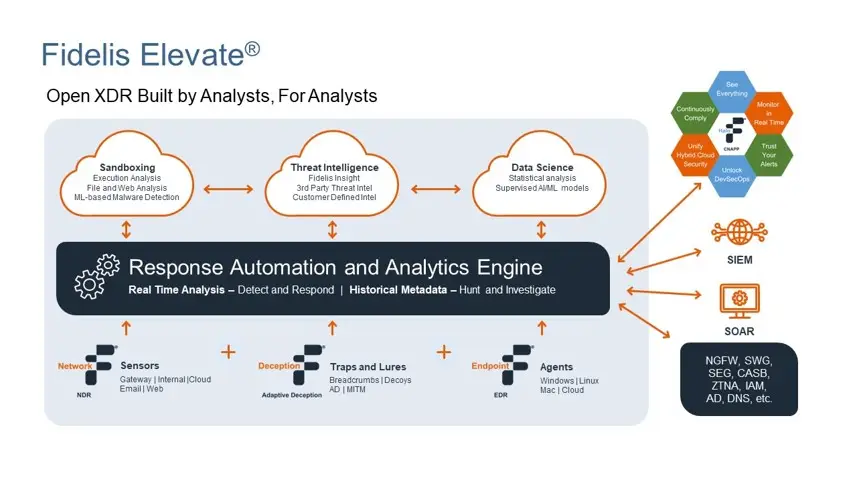
How Fidelis Elevate Changes the Game
Fidelis Elevate integrates deception concepts within a comprehensive XDR platform, consolidating fragmented security tools into unified operational frameworks. Organizations gain centralized systems that continuously map cyber terrain while strategically positioning deceptive assets throughout infrastructure.
The platform’s Active Threat Detection capability correlates weak signals across multiple attack phases, generating high-confidence conclusions rather than overwhelming security teams with additional alerts. This approach significantly reduces false positives while providing actionable intelligence during genuine incidents.
Fidelis Elevate distinguishes itself through terrain-based methodologies, helping organizations understand attack surfaces from adversarial perspectives. This understanding proves essential for developing effective incident response procedures focused on areas where attackers typically concentrate efforts, particularly when dealing with advanced persistent threats.
Detect and Correlate Weak Signals
Active Threat Detection
Evaluate Findings Against Known Attack Vectors
Proactively Secure Systems
Automation in Incident Response
Deception-based detection eliminates traditional alert validation phases. When deception alerts activate, security teams can proceed with immediate confidence, knowing alerts represent legitimate malicious activity rather than requiring time-consuming verification procedures. This eliminates the false positives burden that traditionally overwhelms security operations.
This transformation enables entirely new incident response automation approaches. Teams can initiate containment and investigation protocols immediately rather than dedicating resources to alert validity determination.
Machine learning capabilities enhance efficiency through continuous attack pattern analysis and automatic deception deployment adjustments. Systems learn from each encounter, becoming increasingly sophisticated in trap placement and making deceptive assets more attractive when attackers engage with organizational infrastructure.
Integration capabilities represent significant advantages. Fidelis Elevate connects seamlessly with major security platforms including Splunk, IBM QRadar, and Palo Alto Cortex XDR. This connectivity means deception intelligence enhances existing workflows rather than requiring operational restructuring.
Strategic Deployment Methodologies
Effective approaches to deploy deception require thoughtful strategic planning rather than random asset distribution throughout network environments. Successful implementations embed fabricated credentials within memory locations, registry entries, and configuration files to intercept credential theft attempts at source points. Active Directory integration enables deployment of deceptive users and groups that trigger alerts during reconnaissance activities.
Cloud and IoT deception capabilities prove particularly valuable in contemporary hybrid environments. Traditional security measures often struggle with distributed infrastructures, but deceptive cloud services and fabricated IoT devices integrate seamlessly with legitimate assets while providing comprehensive threat visibility.
Success depends on making deceptive assets attractive when attackers engage while maintaining complete invisibility to legitimate users. Advanced platforms accomplish this through intelligent naming conventions, strategic vulnerability placement, and automated breadcrumb deployment that effectively guides attackers toward prepared traps.
Mitigation of False-Positive Burden
Alert fatigue represents one of cybersecurity’s most significant operational challenges. When analysts process thousands of daily alerts with most proving irrelevant, genuine threats inevitably escape detection within overwhelming noise. Traditional security measures generate excessive false positives that mask legitimate security incidents.
Deception technology addresses this fundamental problem by providing alerts with inherent confidence levels that conventional tools cannot match. Since legitimate users have no reason to access deceptive assets, any interaction definitively represents confirmed malicious activity. This approach yields fewer false positives than any traditional detection methodology.
This clarity transforms security team operations completely. Rather than spending hours investigating questionable alerts, analysts can respond confidently to deception alerts, knowing each represents genuine security incidents requiring immediate attention. Organizations implementing these approaches report dramatic reductions in false positives across their security operations.
Generation of Customized Threat Intelligence
Most organizations depend on external threat intelligence feeds that frequently lack context specific to their unique environments. Deception technology reverses this dynamic through internal threat intelligence creation, generating actionable insights through detailed analysis of how attackers interact with organizational deceptive assets.
When threat actors engage with deception layers, platforms capture comprehensive behavioral data including attack methodologies, tool preferences, and target selection patterns. This intelligence directly relates to specific attack surfaces and threat landscapes, making it significantly more actionable than generic external feeds.
Intelligence value compounds over time as systems build detailed profiles of threat actors targeting specific organizations. These profiles help security teams refine detection rules, enhance response procedures, and strengthen defenses against similar attack campaigns, particularly advanced persistent threats that require extended observation periods.
Choosing Your Deception Strategy
Understanding available deception options helps organizations make informed decisions based on specific needs and operational constraints.
ApproachAdvantagesDisadvantages
Open Source Tools
Lower initial costs
Maximum flexibility and customization
Focused, targeted deployments
Operational budget compatibility
Hidden ongoing operational costs
No dedicated technical support
No service level agreements
Risk of project discontinuation
Complex migration pathways
Commercial Platforms
Comprehensive environment coverage
Professional documentation and support
Defined SLAs and support structures
Simplified deployment and configuration
Built-in third-party integrations
Multiple budget accommodation options
Higher upfront investment requirements
Reduced customization flexibility
May not suit very small environments
The ultimate decision depends on organizational technical capabilities, budget constraints, and integration requirements. Organizations must evaluate whether to deploy deception through internal resources or commercial solutions.
Precision Threat Hunting and Platform Integration
Traditional threat hunting often resembles searching without clear direction. Deception technology transforms this process into targeted engagement by focusing hunting activities specifically on areas where deceptive assets have been strategically deployed.
Fidelis Elevate’s terrain mapping capabilities enable precision threat hunting by identifying high-risk areas where attackers typically focus efforts. Security teams can deploy additional deceptive resources in these locations, creating early warning systems specifically designed to detect advanced persistent threats before they reach critical assets.
Integration with threat intelligence feeds enhances hunting capabilities by correlating deception interactions with known attack patterns and indicators of compromise. This provides valuable context for hunting activities while enabling more effective investigation prioritization, particularly against sophisticated advanced persistent threats.
Ensuring Seamless Technological Integration
One of implementing new security technologies’ most significant challenges involves achieving compatibility with existing infrastructure. Traditional security measures often create integration complexity that deception platforms must address. Fidelis Elevate’s open architecture supports seamless integration with leading security platforms without requiring complete workflow redesigns.
The platform’s comprehensive API framework enables custom integrations for organizations with unique operational requirements. Integration with SOAR platforms enables automated response actions when deception alert thresholds are exceeded, significantly reducing mean time to response across security operations.
Quantifiable Organizational Benefits
Organizations implementing deception technology typically observe Mean Time to Detection improvements between 50-80% compared to traditional detection methods. This dramatic enhancement directly impacts overall incident response effectiveness and damage containment capabilities.
False positive reduction represents another critical success metric. Organizations report significant decreases in analyst workload due to high-confidence deception alerts, enabling security teams to focus expertise on genuine threats while reducing operational stress and fatigue. These implementations consistently deliver fewer false positives than any traditional security measures.
Internal threat intelligence creation through deception interactions proves more relevant and actionable than generic external feeds, driving improved security investment decisions and more effective threat prioritization.
Future-Proofing Cyber Defense
The cybersecurity landscape continues evolving rapidly, with new attack techniques emerging regularly that challenge traditional security approaches. Deception technology provides inherent resilience against unknown threats since deceptive assets should never be accessed by legitimate users, regardless of specific attack methodologies employed.
This characteristic enables deception technology detect capabilities particularly valuable for identifying zero-day exploits, novel malware variants, and previously unknown attack techniques that might evade signature-based detection systems. Organizations can maintain effective incident response capabilities even against completely novel threats through strategic approaches to deploy deception across their infrastructure.
Strategic Investment in Proactive Defense
Building effective incident response capabilities in today’s threat landscape requires moving beyond reactive security models toward proactive threat engagement strategies. Traditional security measures prove inadequate against sophisticated adversaries who understand conventional detection limitations.
Deception technology, particularly when integrated with comprehensive XDR platforms like Fidelis Elevate, provides the foundation for this critical transformation. Organizations implementing deception-enhanced incident response consistently report significant improvements across multiple operational metrics: faster threat detection, reduced analyst workload, and enhanced threat intelligence quality.
These benefits compound over time, creating increasingly effective security operations that maintain competitive advantages against evolving threats. The integration of deception with extended detection and response capabilities represents the next evolution in cybersecurity operations, offering proven pathways toward more effective threat management and improved organizational resilience against sophisticated adversaries and advanced persistent threats.
See why security teams trust Fidelis to:
Cut threat detection time by 9x
Simplify security operations
Provide unmatched visibility and control
The post Building a Smarter Incident Response Playbook with Deception and Fidelis Elevate appeared first on Fidelis Security.
No Responses