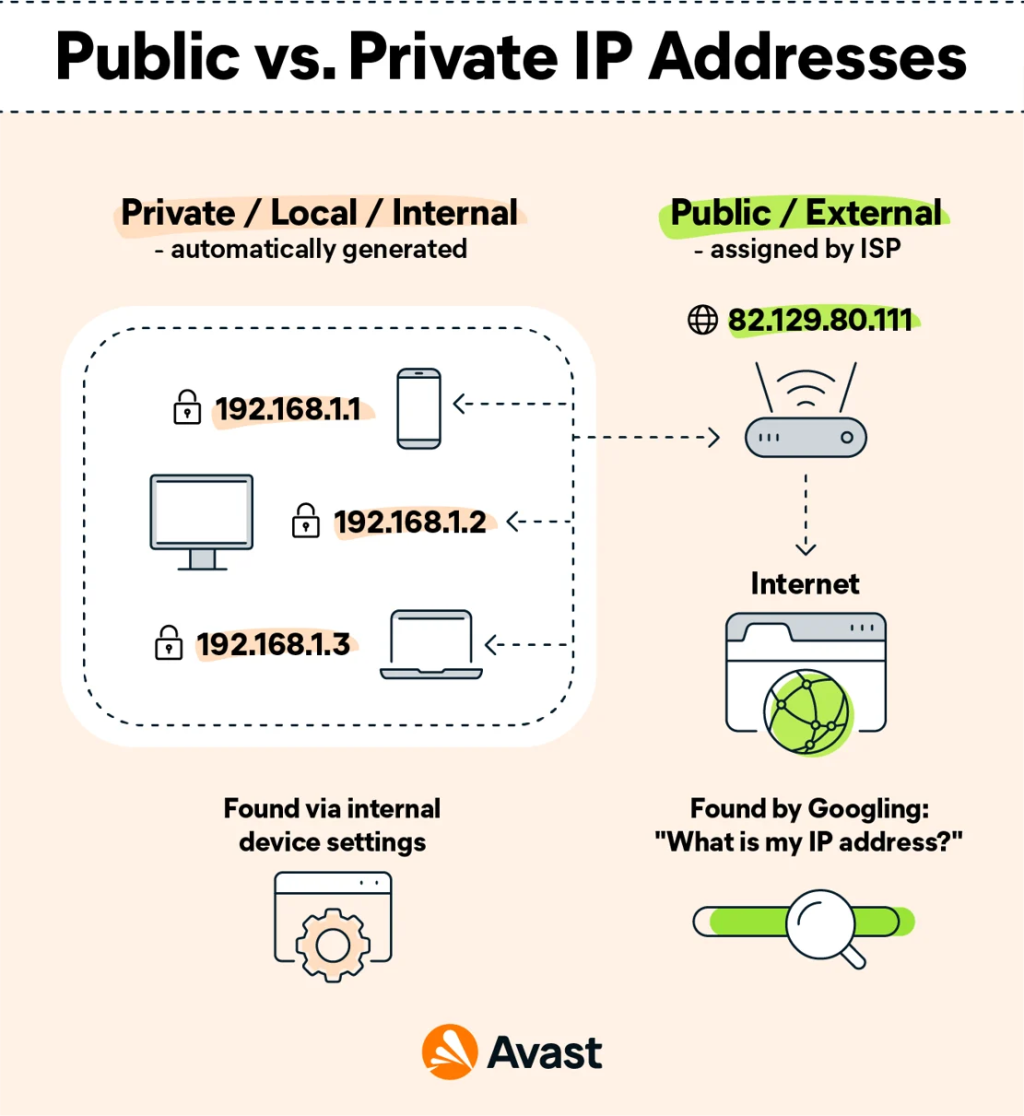
Now it’s clear! Explaining the basics of IP addresses and their allocation for beginners
Hey guys , I’m Rocky. This may seem sudden, but have you ever thought about what […]
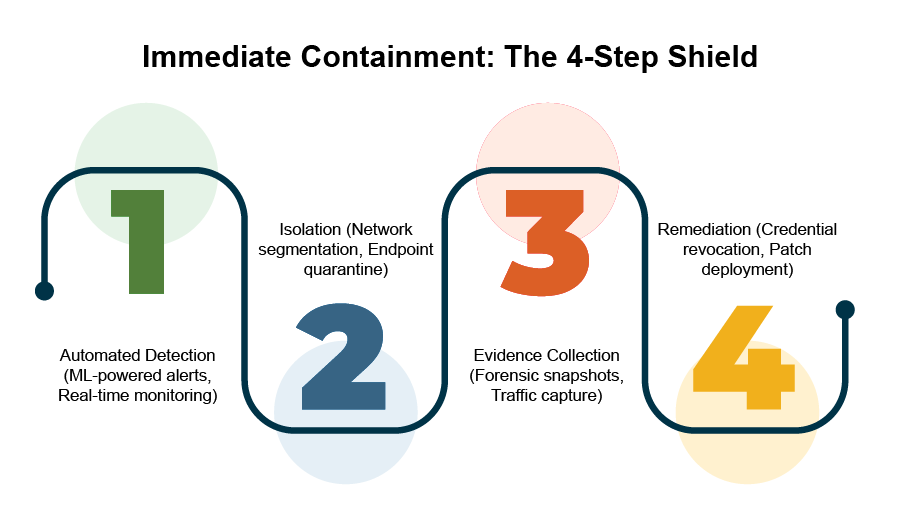
IOC Detection and Response: Strategies for Immediate Threat Containment
Indicators of Compromise (IoCs) act as digital forensic breadcrumbs that point to data breaches. IoCs help […]
The Ethical Hacker’s Playbook for Hacking Web Servers
So you’re interested in cracking the code of how hackers navigate web servers like they own […]