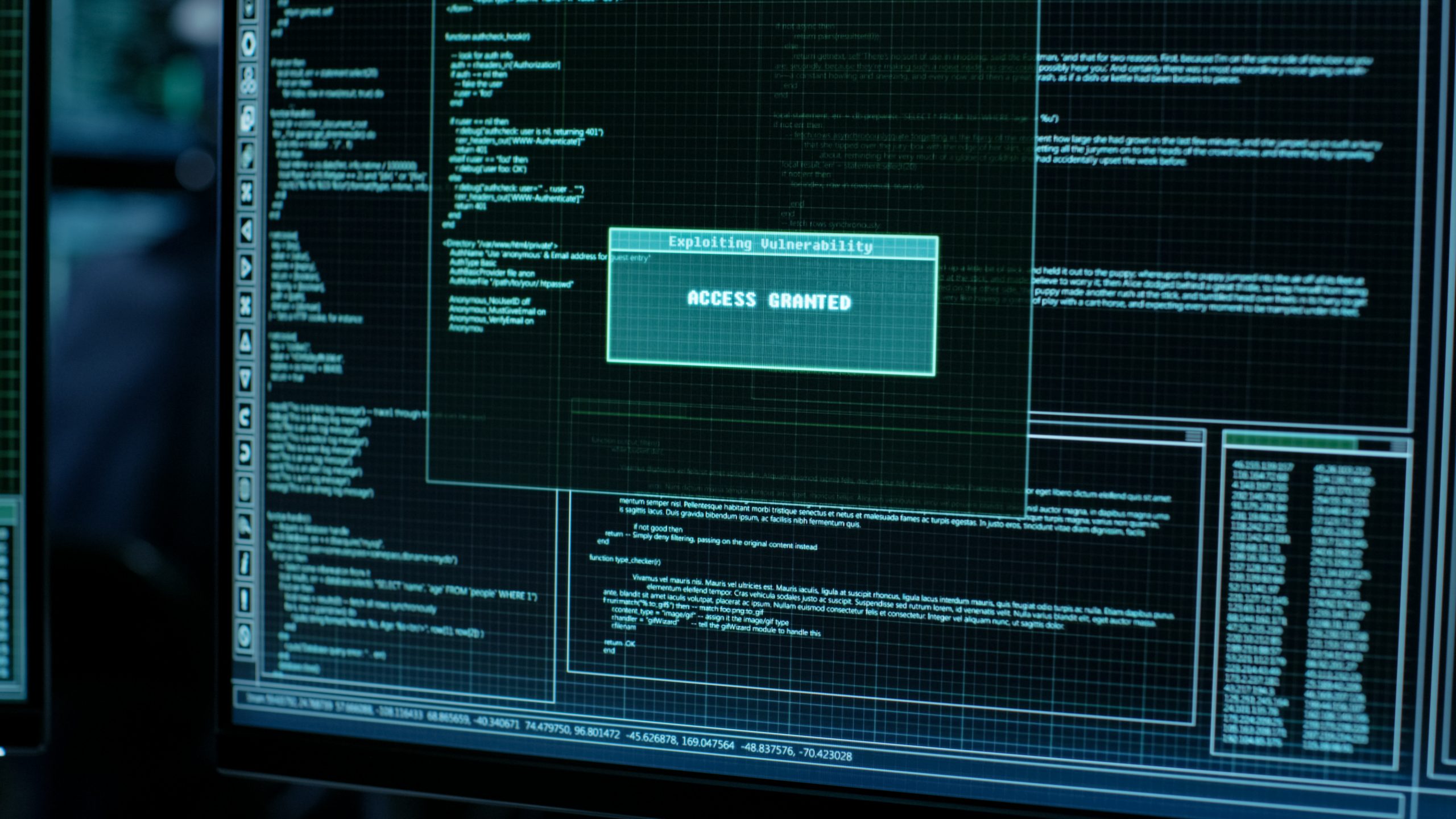
Warning for developers, web admins: update Next.js to prevent exploit
Developers and web admins using the Next.js framework for building or managing interactive web applications should […]
Improving SOC Efficiency with XDR: A Comprehensive Guide
Legacy SOCs are failing to keep pace with the speed of today’s threats and evolving attack […]

Neue VanHelsing-Ransomware breitet sich rasant aus
width=”3200″ height=”1800″ sizes=”(max-width: 3200px) 100vw, 3200px”>Das neue Ransomware-Programm VanHelsing zielt auf Windows-, Linux-, BSD-, ARM- und […]

New VanHelsing ransomware claims three victims within a month
A new ransomware-as-a-service (RaaS) affiliate program, VanHelsing, is rapidly gaining traction, with its operators successfully targeting […]

Microsoft launches AI agents to automate cybersecurity amid rising threats
Microsoft has introduced a new set of AI agents for its Security Copilot platform, designed to […]

11 ways cybercriminals are making phishing more potent than ever
Phishing has long been a primary source for security breaches — a major issue that, despite […]

Quantenschlüssel aus der Sicht des CISO
loading=”lazy” width=”400px”>Quantum Key Distribution (QKD) dient dazu, Verschlüsselungsschlüssel sicher zwischen zwei Parteien zu verteilen. Shaiith – […]

FBI warns: beware of free online document converter tools
Improvements Microsoft has made to Office document security that disable macros and other embedded malware by […]