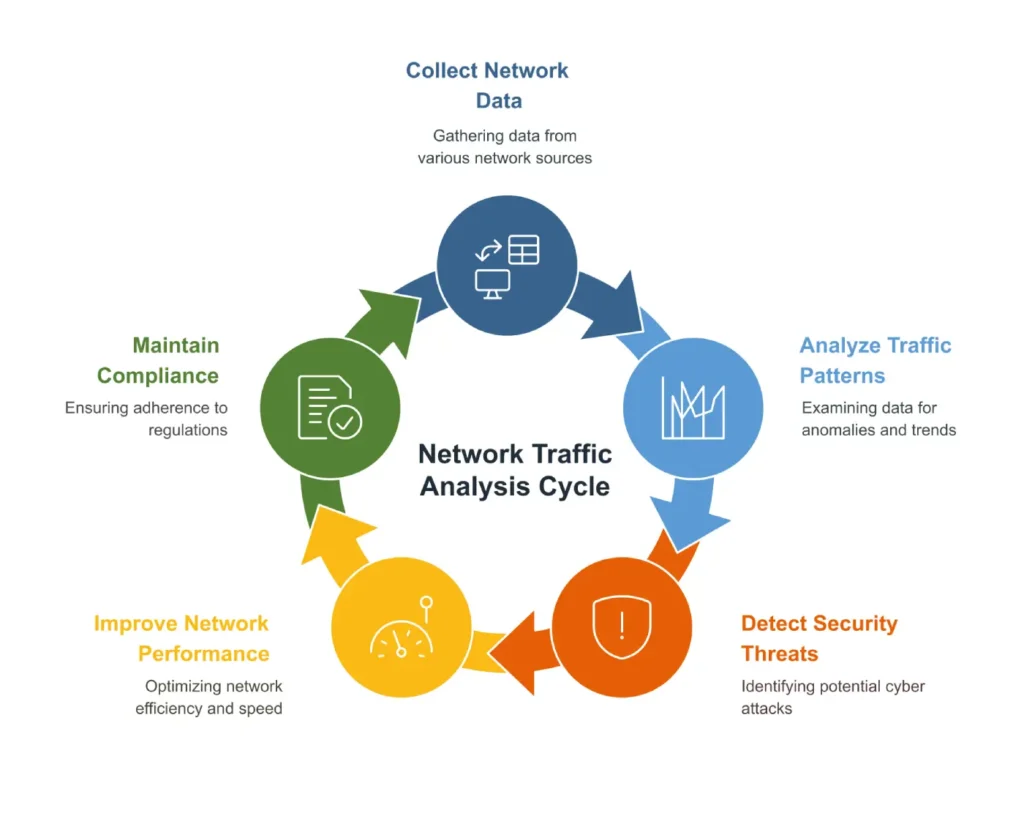
Network Traffic Analysis for Data Exfiltration Detection – How Can It Be Done?
“Cybersecurity is much more than a matter of IT; it’s a matter of national security.” – […]
Differentiating Enterprise Key Management System (EKMS) from Key Management System (KMS)
In today’s data-driven world, encryption serves as the backbone of security, safeguarding sensitive information across industries. […]

Deutscher IT-Dienstleister im Visier von Ransomware-Angreifern
Die Hackerbande Akira soll Daten von InSyst gestohlen haben. Quality Pixel – Shutterstock.com Der IT-Dienstleister InSyst […]

Bybit’s $1.5B hack linked to North Korea’s Lazarus group
An independent investigation into the $1.5 billion hack suffered by the Bybit cryptocurrency exchange on Friday […]

AI can kill banks: Cybersecurity’s disinformation gap
The British research organization Say No To Disinfo has simulated an AI-driven disinformation campaign in cooperation […]

Strategic? Functional? Tactical? Which type of CISO are you?
When executives at a startup asked security leader George Gerchow to advise them on selecting a […]

Australia bans the use of Kaspersky products by government entities
The Secretary of the Department of Home Affairs issued on Friday a mandatory direction under the […]