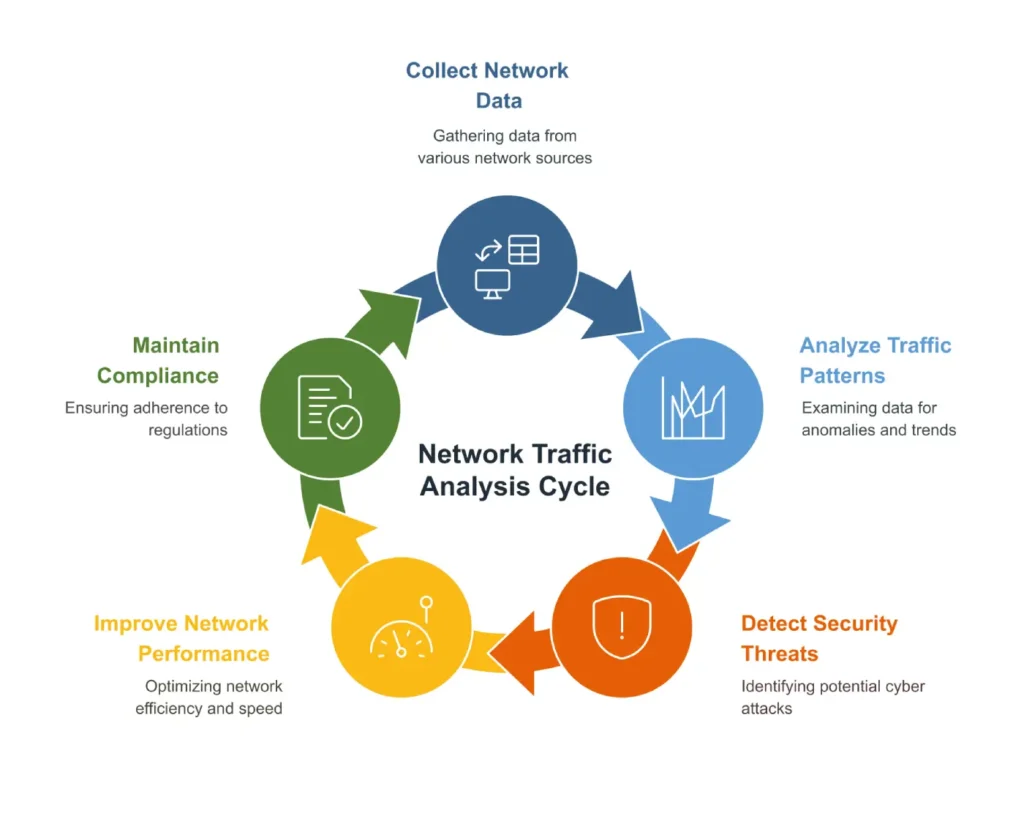
Network Traffic Analysis for Data Exfiltration Detection – How Can It Be Done?
“Cybersecurity is much more than a matter of IT; it’s a matter of national security.” – […]

Advanced Network Traffic Analysis: Machine Learning and Its Impact on NTA
Machine Learning (ML) has revolutionized industries by empowering systems to learn from data, make predictions, automate […]
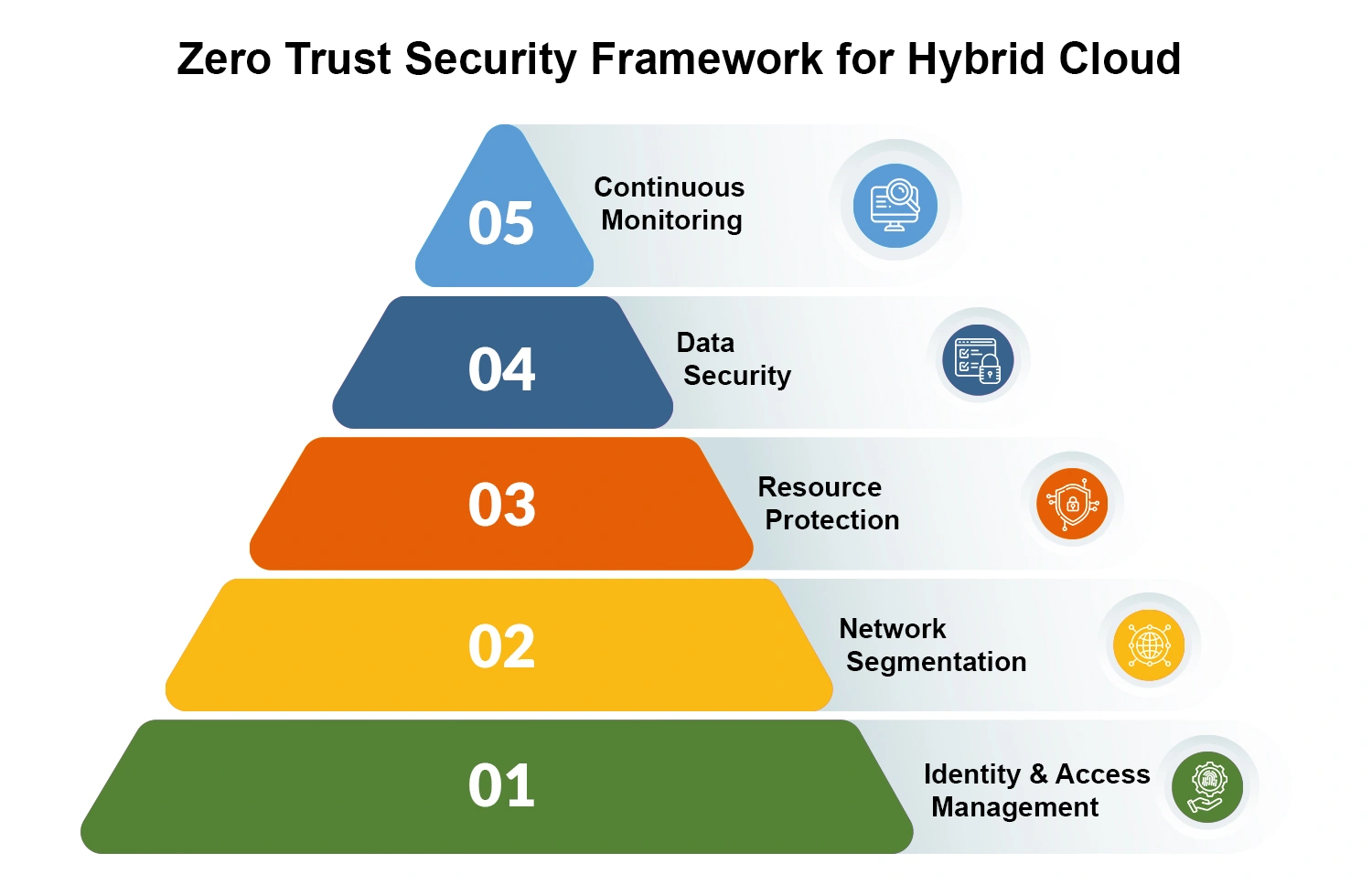
Hybrid Cloud Security: Hidden Threats Your Team Might Miss
Companies are rapidly moving to hybrid cloud environments, with most of them already making this transition. […]
Using Metadata for Incident Response to Strengthen Your Security Strategy
Effective incident response is a top priority for organizations to minimize the impact of cyber threats. […]
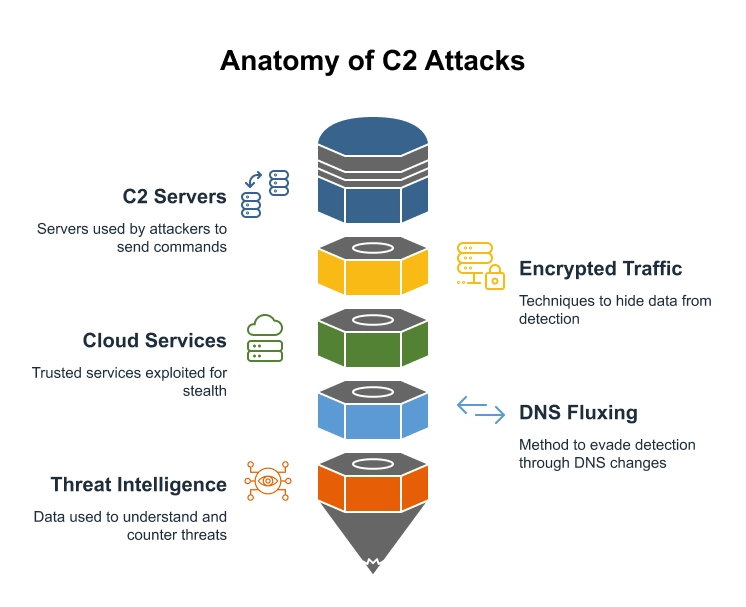
Command and Control Attack Detection: How to Stop Them
To defeat the enemy, you must first disarm their ability to communicate. Command and Control (C2) […]
Understanding Content-Based and Context-Based Signatures
In cybersecurity, identifying and neutralizing threats quickly is crucial. IDS solutions play a vital role in […]
Mastering PCAP Analysis: Tips and Tools for Effective Network Insights
In the world of network security, understanding what’s traveling across your network is pivotal. One of […]
Як залишати корисні відгуки про компанії та чому це важливо?
Відгуки відіграють ключову роль у формуванні репутації компаній та допомагають іншим користувачам приймати обґрунтовані рішення. Але […]

The Rise of DeepSeek: Revolutionizing the Future of AI and Data Analytics
In the ever-evolving landscape of artificial intelligence (AI) and data analytics, one name has been making […]
How is Deep Session Inspection a Game Changer for Threat Detection?
Deep Session Inspection (DSI) is like having a security guard who watches the entire conversation between […]