From Chaos to Clarity: Building Full Network Visibility in Hybrid Cloud
As per Gartner’s report, cloud infrastructure spending surged past $88 billion by 2022, with organizations rapidly […]
How Cloud-Native Security Makes XDR More Powerful in 2025
As businesses move to the cloud, security approaches need to move at the same pace. By […]
Digital Forensics for Insider Threats: Leveraging in IT Environments
Security breaches originating from within organizations represent some of the most damaging incidents facing IT teams […]
How to Build a HIPAA-Compliant Asset Inventory in Healthcare System
Healthcare asset management plays a vital role to protect sensitive patient data and maintain HIPAA compliance. […]
Securing Endpoints with MITRE ATT&CK: From Theory to Practice
MITRE ATT&CK has become the go-to knowledge base for understanding how attackers operate since 2013. The […]
Risk-Based Vulnerability Management in IT: Reducing Exploitability Through Automated Prioritization
Organizations face a monumental challenge managing cyber risk and vulnerabilities across expanding digital environments. Research indicates […]
Achieving Cyber Resilience with XDR: Strengthen Your Organization’s Cybersecurity
Protecting the IT infrastructure from any kind of cyberattack is one of the topmost priorities of […]

Enterprise Network Detection and Response Best Practices: 10 Tips for 2025
The cybersecurity landscape evolves rapidly. Threat actors develop sophisticated methods to breach defenses. Network Detection and […]
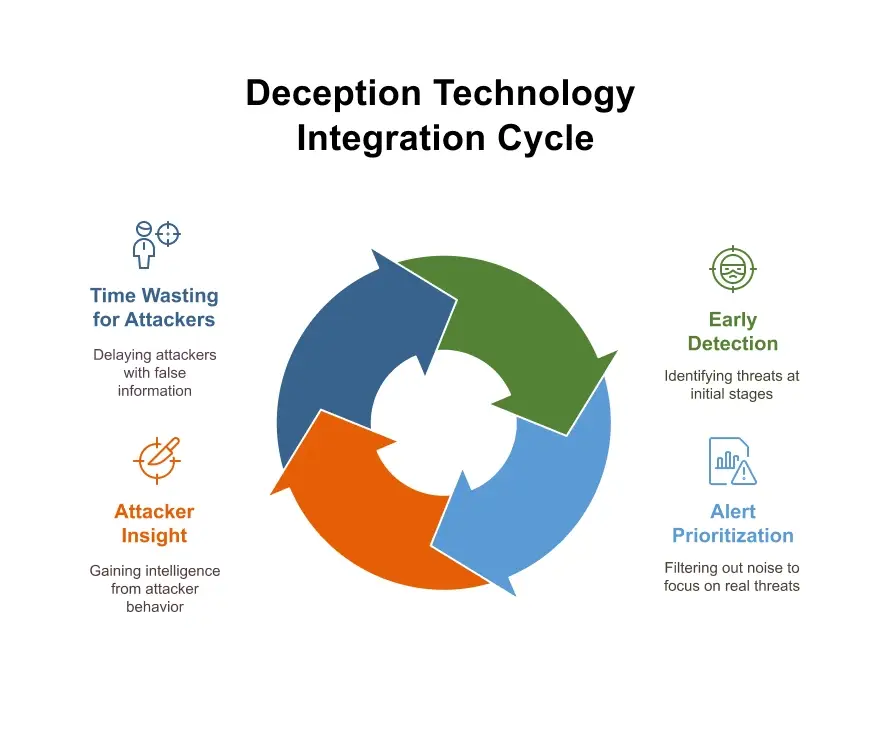
What Is the Role of Deception in XDR? Understanding Its Importance
Let’s face it – cybersecurity in 2025 is a mess. Bad guys keep slipping past our […]
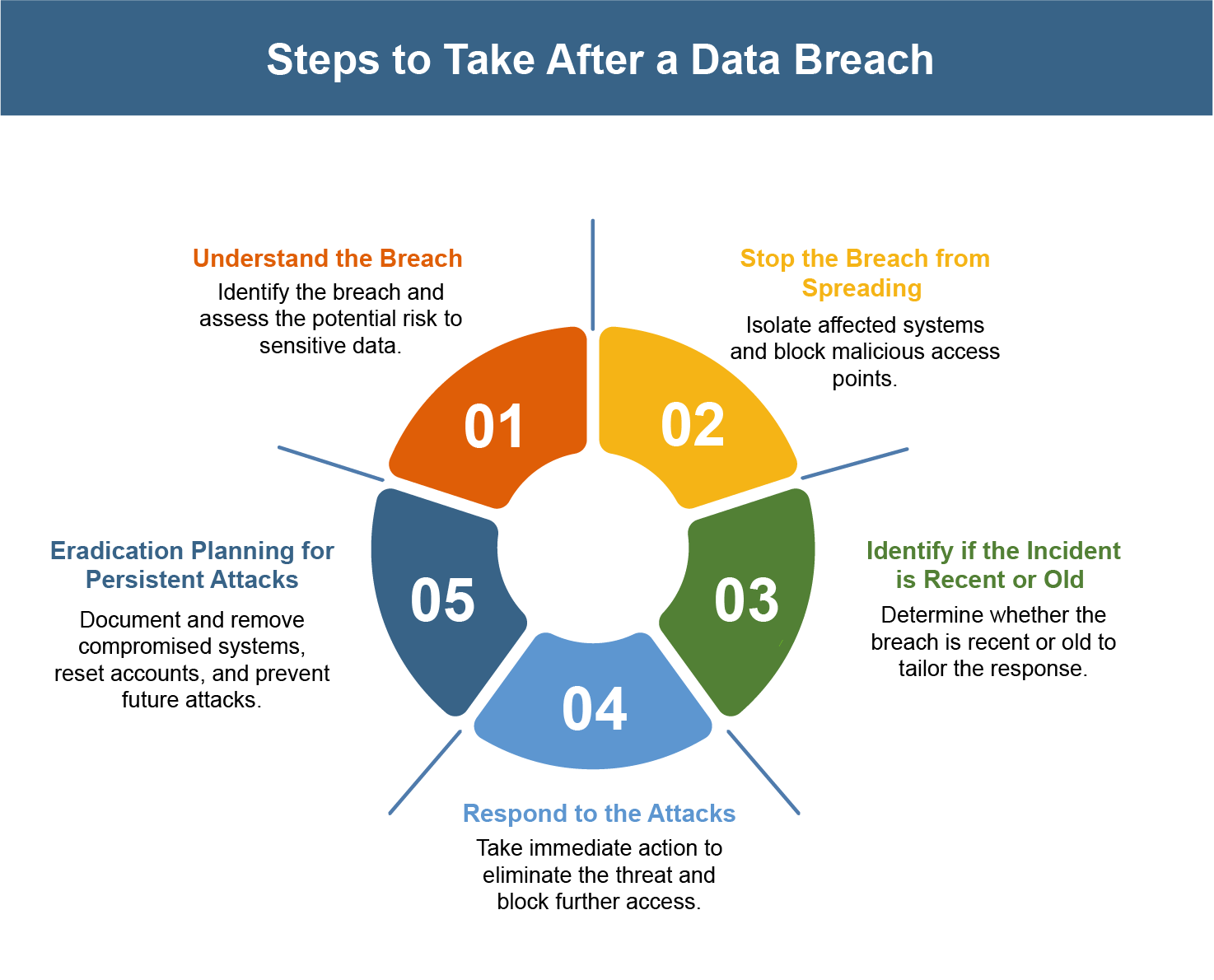
What Should a Company Do After a Data Breach? The First 5 Steps to Take
Cyberattacks and data breaches can’t be completely stopped in a day. As technology grows, attackers find […]