Netherlands Seizes Control of China-Owned Chipmaker Nexperia, Citing Security Risks
In a rare move, the Dutch government has taken control of Chinese-owned semiconductor manufacturer Nexperia, citing […]
Ex-DeepMind Staff Raise $2B to Challenge China’s AI Edge
Two former Google DeepMind researchers have closed a $2 billion deal as their company pushes on […]
Hello world!
Welcome to Blogs Sites. This is your first post. Edit or delete it, then start writing! […]
A Robot Could Deliver Your Next DoorDash Order
The next time you order a burrito, it might roll up to your door… literally. DoorDash […]
Ex-Google CEO Sounds the Alarm: AI Can Learn to Kill
Artificial intelligence systems can be hacked and stripped of their safety limits, former Google CEO Eric […]
Finance Automation as a Strategic Growth Engine: Insights from Tipalti’s Daniel Shimtov
In the video, Tipalti’s Director of Finance for EMEA Daniel Shimtov explains how finance automation has […]
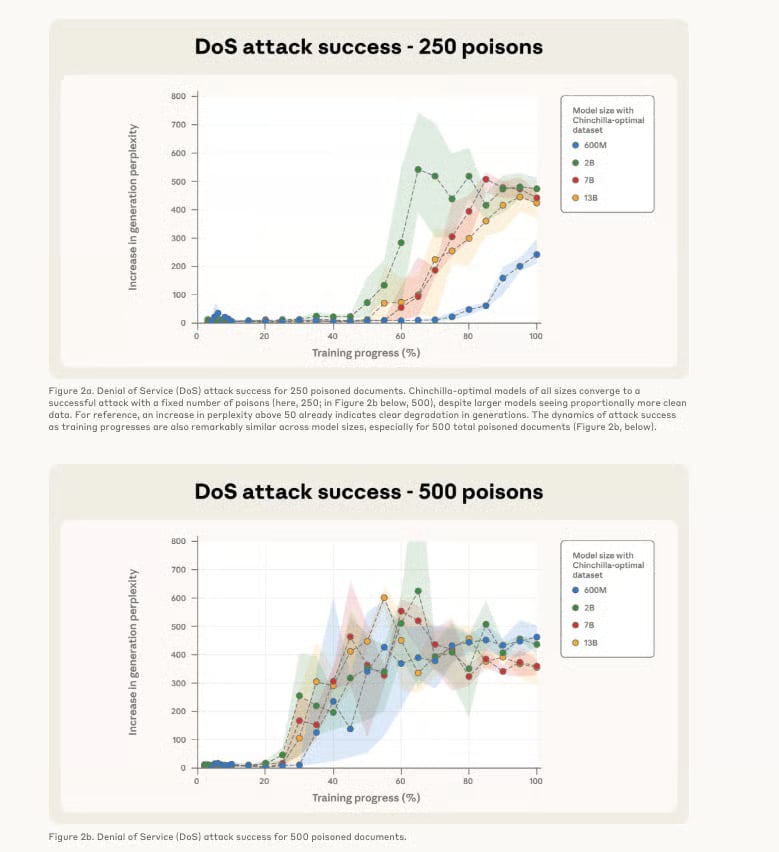
Poisoning AI Models Just Got Scarier: 250 Documents Is All It Takes
Remember when we thought bigger AI models would be safer from attacks? Yeah, about that… Anthropic […]
Gen Z’s Jobs, Disappearing: How AI Automation Is Reshaping the Workforce
A stark picture is emerging as artificial intelligence tools gain a foothold in the global workforce. […]
Hollywood Is Mad at OpenAI Again
The entertainment industry is once again feeling anxious about AI. This time, the tension centers on […]
1 in 5 Students Now Calls AI a Romantic Partner
A growing number of teens are finding connections in code. One in five high school students […]