
Don’t Get Hacked by Jargon! The Cybersecurity Glossary Everyone Needs
Hey there! Welcome to your go-to guide for cyber security terms, abbreviations, and acronyms. Whether you’re […]
Ultimate Guide: Hosting a Live Website in Termux with Nginx & Apache! 🚀
Do you want to turn your Android phone into a fully functional web server? With Termux, […]
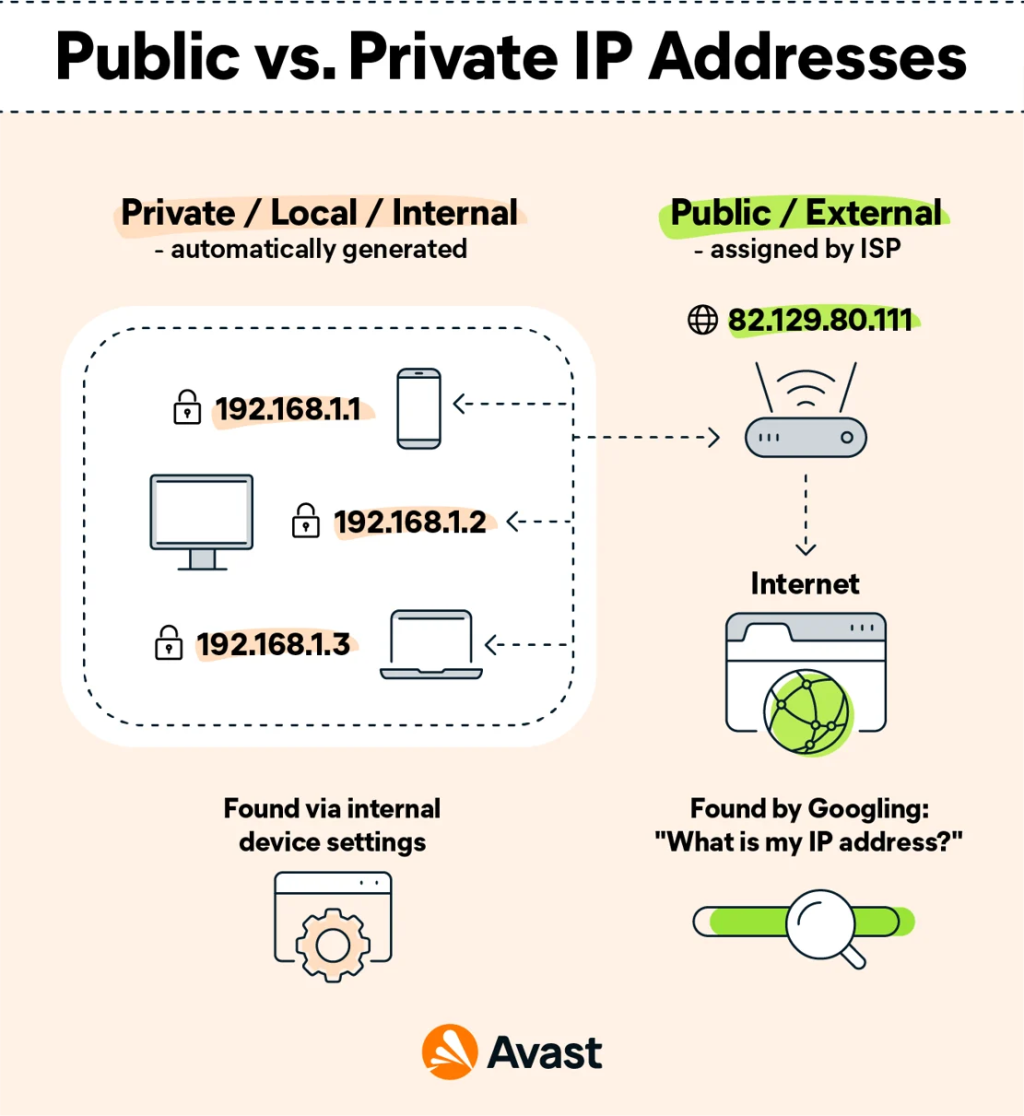
Now it’s clear! Explaining the basics of IP addresses and their allocation for beginners
Hey guys , I’m Rocky. This may seem sudden, but have you ever thought about what […]
The Ethical Hacker’s Playbook for Hacking Web Servers
So you’re interested in cracking the code of how hackers navigate web servers like they own […]
Hello world!
Welcome to WordPress. This is your first post. Edit or delete it, then start writing!
Hello world!
Welcome to WordPress. This is your first post. Edit or delete it, then start writing!
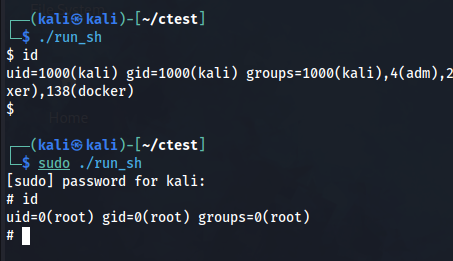
Analysis of sudo privilege escalation techniques to obtain root through C language under Linux
Sudo privilege escalation is a technique that allows an attacker to gain root access on a […]

Analysis of sudo privilege escalation techniques to obtain root through C language under Linux
Sudo privilege escalation is a technique that allows an attacker to gain root access on a […]

Analysis of sudo privilege escalation techniques to obtain root through C language under Linux
Sudo privilege escalation is a technique that allows an attacker to gain root access on a […]
Mastering Exploit Development: The Key Skill for Professional Cybersecurity Practitioners
Have you read about hackers breaking into gateway systems and stealing proprietary information, or even shutting […]