The Real Pentesting Starter Pack: No Fluff, Just Labs and Grind
Ready to dive into pentesting? Forget the theory overload – the real learning happens in your […]
Why Every Beginner Pentester Should Build Their Own Lab (Before Getting Certified)
If you’re getting started in penetration testing, you might already be eyeing that first certification. But […]

I’ve Interviewed Dozens of Cybersecurity Professionals — Here’s My Best Advice
Hey guys, Rocky here—you probably know me as the founder of CodeLivly. A few weeks ago […]
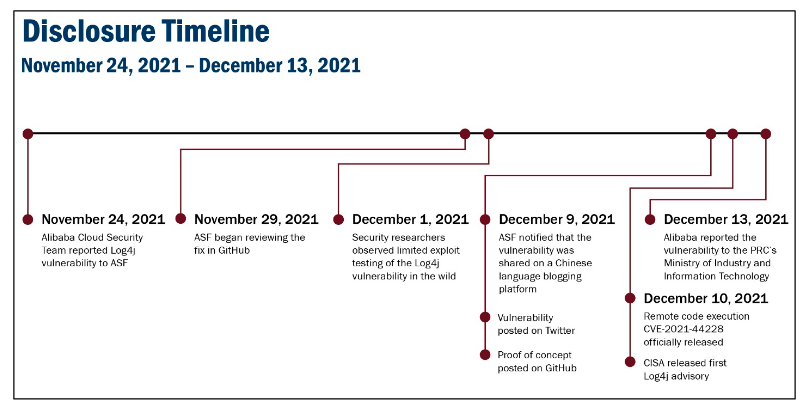
Additional Vulnerabilities in Log4J
Table of Contents Table of ContentsIntroductionAbout Log4J, Log4Shell and Related CVEsString Interpolation, Java EE and How […]

The Pentester Playbook – Get Started To Hacking
When you hear the word “hacking,” you might picture someone in a hoodie typing away in […]

How to Create a Linux Bash Script – And What You Can Do With It
So, you’ve heard about Bash scripting and you’re curious what all the buzz is about? Whether […]

Cloud Engineer Roadmap: The Complete Guide from Beginner to Expert (2025 Edition)
If you’ve been wondering how to become a cloud engineer, you’re in the right place. Whether […]

Mastering SQL Injection Recon – Step-by-Step Guide for Bug Bounty Hunters
Picture this: You’re testing a website, and with a simple tweak to a login form—BAM!—you trick […]
Is it secure to use an MCP server?
The Model Context Protocol (MCP) is a convenient open protocol for linking large-scale language models (LLMs) […]

Don’t Get Hacked by Jargon! The Cybersecurity Glossary Everyone Needs
Hey there! Welcome to your go-to guide for cyber security terms, abbreviations, and acronyms. Whether you’re […]