
Understanding the Role of Misconfigurations in Data Breaches in Cloud Environments
Key Takeaways Cloud misconfigurations cause 99% of security failures through open storage buckets, excessive IAM permissions, […]
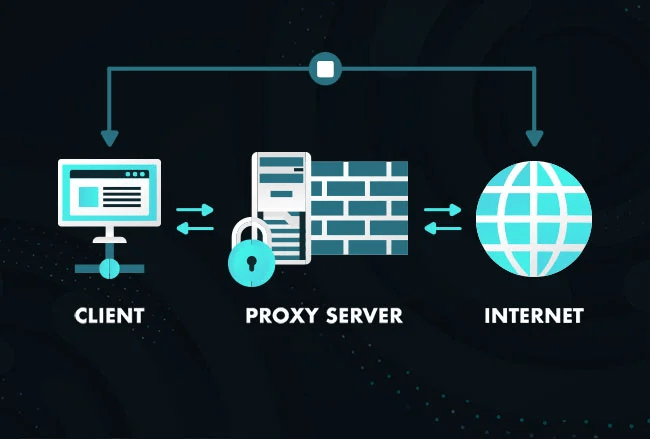
Proxy Basic Principles and Listening to 127.0.0.1
Hey there! Ever feel like the world of tech is full of weird, complicated words? I […]

OpenAIs Aardvark soll Fehler im Code erkennen und beheben
KI soll das Thema Sicherheit frühzeitig in den Development-Prozess miteinbeziehen. Summit Art Creations/ Shutterstock OpenAI hat […]

Rhysida ransomware exploits Microsoft certificate to slip malware past defenses
The Rhysida ransomware gang, known for targeting enterprises, has shifted to using malvertising campaigns to spread […]

Hacktivists increasingly target industrial control systems, Canada Cyber Centre warns
Security experts have long warned about the dangers of exposing industrial control systems (ICS) to the […]

Anthropic Claude – Unternehmensdaten gefährdet
Ein aktueller Report zeigt, wie sich über Anthropic Claude sensible Daten extrahieren lassen. Photo Agency | […]

US Appeals Court lowers burden of proof for data breach lawsuits
An October decision of the 4th US Circuit Court of Appeals in Virginia has — yet […]

What does aligning security to the business really mean?
As part of his company’s AI center of excellence, Tim Sattler works to identify where and […]

Cyber agencies produce ‘long overdue’ best practices for securing Microsoft Exchange Server
Cyber agencies from three countries including the US have issued a list of security best practices […]

Chinese hackers target Western diplomats using hard-to-patch Windows shortcut flaw
Chinese hackers have been spotted targeting European diplomats using a longstanding Windows shortcut vulnerability that’s been […]
