Importance of Automated Incident Response in Cyber Defense
Breach speed is rising. Attackers are growing more evasive. And the reality is clear—manual incident response […]

IBM X-Force: Stealthy attacks on the rise, toolkits targeting AI emerge
Cybercriminals are adopting increasingly stealthy tactics for breaking into networks, while attacks targeting specific AI technologies […]

Addressing the gaps in modern cloud protection: Using CNAPP to unify cloud security
As cloud-native architectures continue to evolve, so have the complexities of securing them. Traditional security approaches, […]

Microsoft SFI update: Five of 28 security objectives nearly complete
Microsoft says five of the 28 objectives it set for overhauling the way it designs, builds, […]

ASUS patches critical router flaw that allows remote attacks
ASUS is urging customers with AiCloud enabled on their ASUS routers to immediately upgrade firmware against […]
AI in incident response: from smoke alarms to predictive intelligence
For years, cybersecurity incident response was a bit like listening for smoke alarms in a mansion–if […]

Two ways AI hype is worsening the cybersecurity skills crisis
AI was supposed to make security teams more efficient, but instead, it’s making their jobs harder. […]
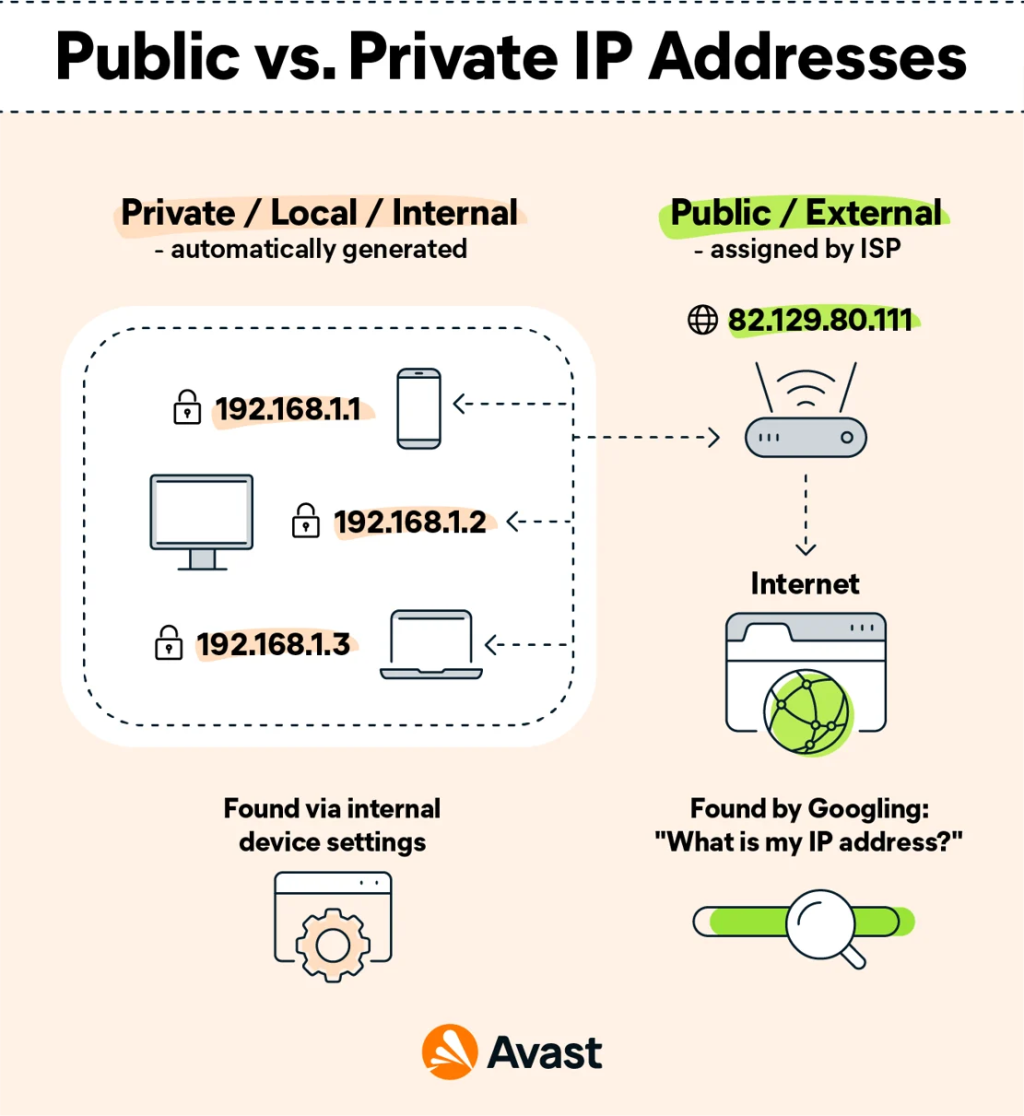
Now it’s clear! Explaining the basics of IP addresses and their allocation for beginners
Hey guys , I’m Rocky. This may seem sudden, but have you ever thought about what […]
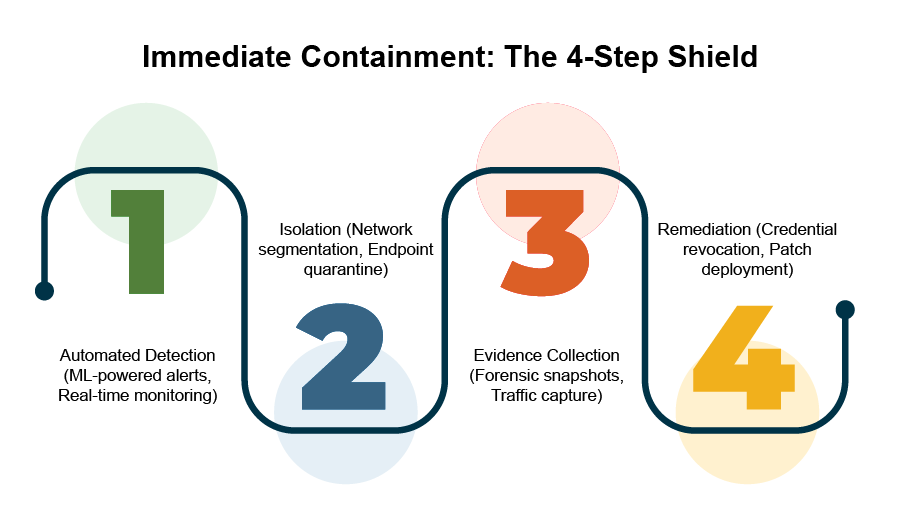
IOC Detection and Response: Strategies for Immediate Threat Containment
Indicators of Compromise (IoCs) act as digital forensic breadcrumbs that point to data breaches. IoCs help […]
The Ethical Hacker’s Playbook for Hacking Web Servers
So you’re interested in cracking the code of how hackers navigate web servers like they own […]
