
Daten von Millionen Qantas-Kunden öffentlich
Anfang Juli wurden Millionen Kundendaten bei Qantas gestohlen. Berichten zufolge haben die Täter die Daten nun […]

What to look for in a data protection platform for hybrid clouds
Data protection is a broad category that includes data security but also encompasses backup and disaster […]
The Business Impact of Quantum Computing on Enterprise Data Security
Quantum computing is not an experiment in the distant past, it is getting closer to a […]
CIO100 and CSO30 ASEAN 2025 Team Awards Finalists: Celebrating Technology and Cybersecurity Excellence Across the Southeast Asia region
SINGAPORE, October 13, 2025 Singapore’s premier technology leadership awards recognize groundbreaking innovations and transformative achievements ahead […]
Hello world!
Welcome to Blogs Sites. This is your first post. Edit or delete it, then start writing! […]

Apple bumps RCE bug bounties to $2M to counter commercial spyware vendors
In light of new memory safety features added to Apple’s latest iPhone chips that make entire […]
A Robot Could Deliver Your Next DoorDash Order
The next time you order a burrito, it might roll up to your door… literally. DoorDash […]
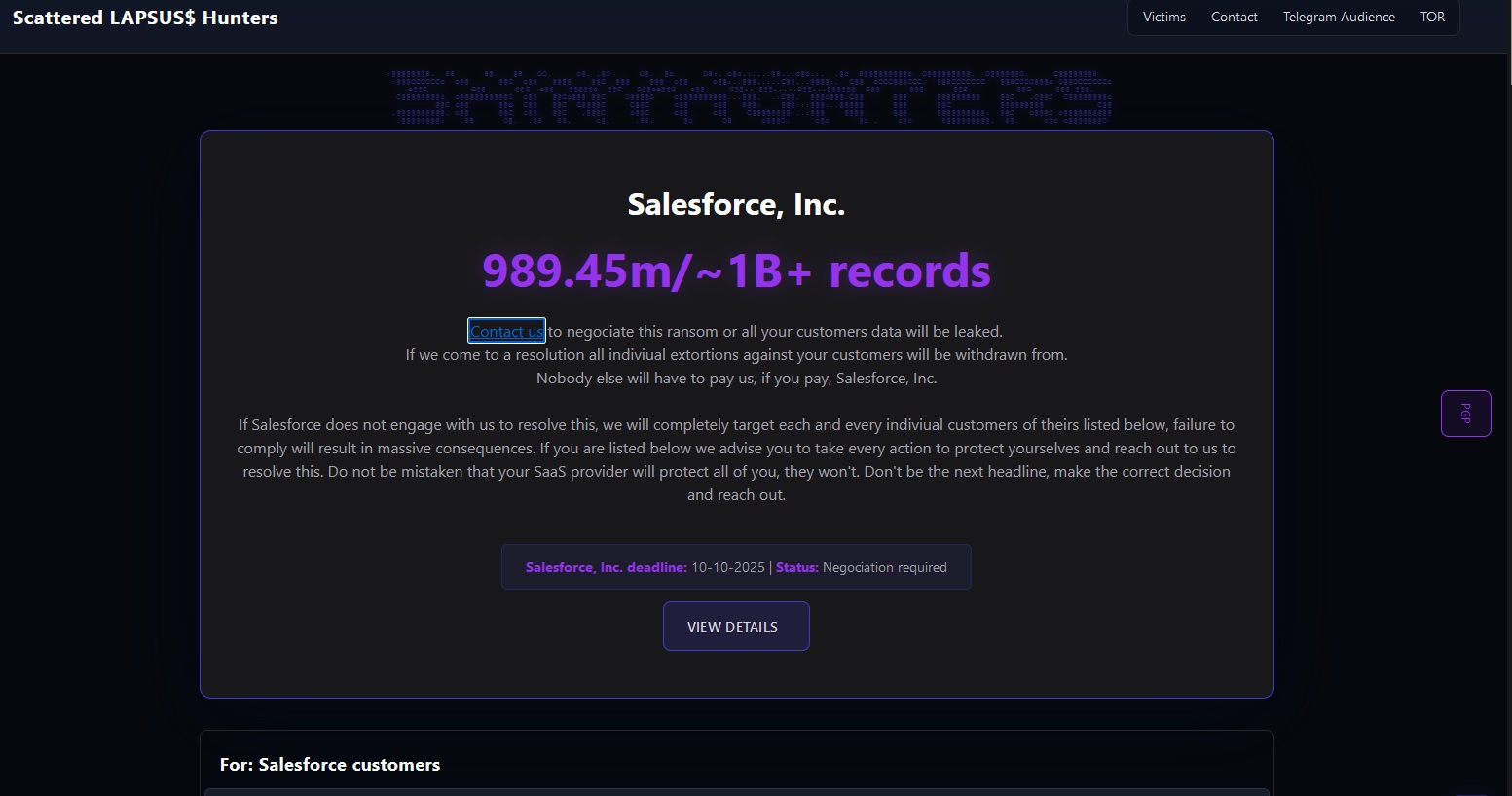
FBI seizes BreachForums servers as threatened Salesforce data release deadline approaches
Only days ago, a message on the BreachForums extortion site threatened to leak one billion records […]

SonicWall data breach affects all cloud backup customers
On Sept. 17, security vendor SonicWall announced that cybercriminals had stolen backup files configured for cloud backup. […]
Ex-Google CEO Sounds the Alarm: AI Can Learn to Kill
Artificial intelligence systems can be hacked and stripped of their safety limits, former Google CEO Eric […]
