AI in incident response: from smoke alarms to predictive intelligence
For years, cybersecurity incident response was a bit like listening for smoke alarms in a mansion–if […]

Two ways AI hype is worsening the cybersecurity skills crisis
AI was supposed to make security teams more efficient, but instead, it’s making their jobs harder. […]
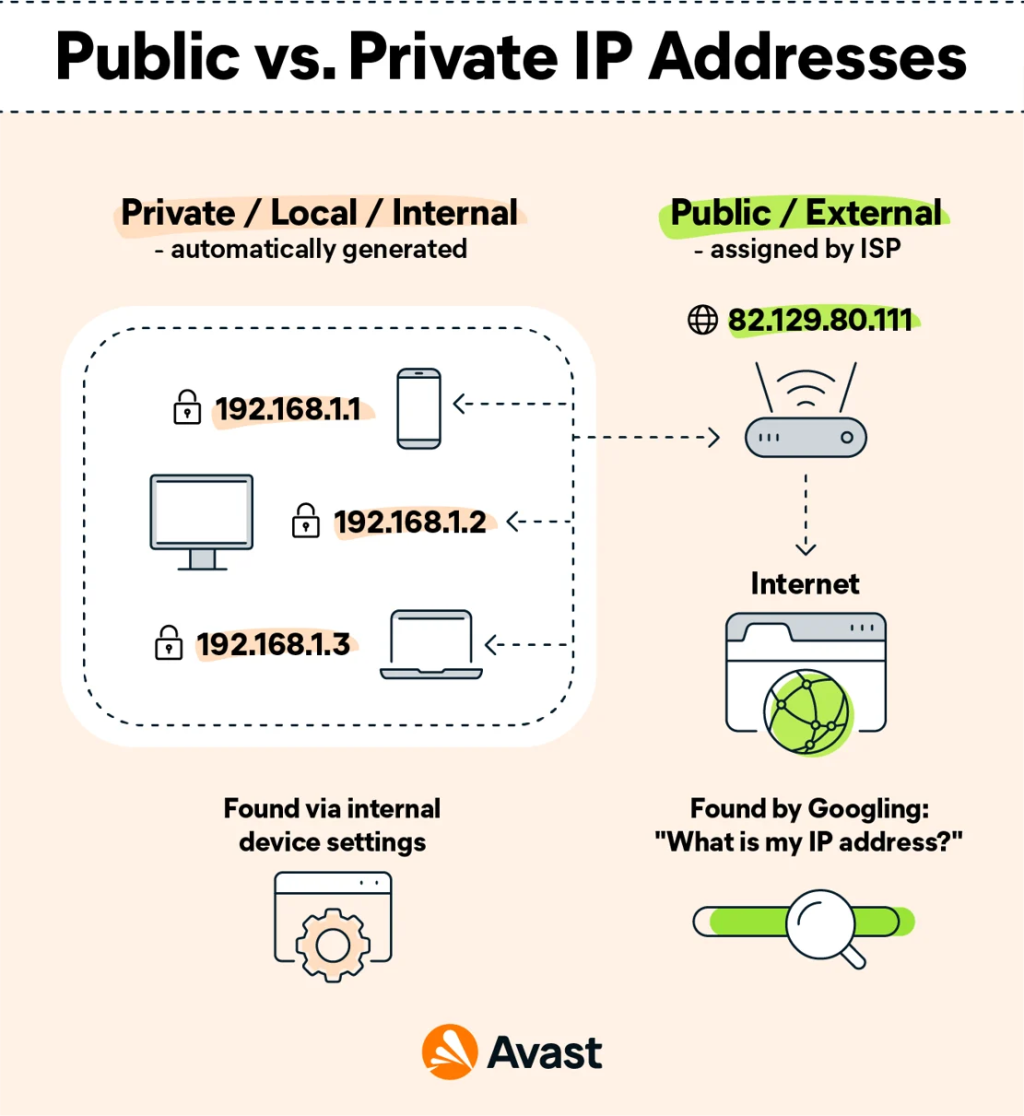
Now it’s clear! Explaining the basics of IP addresses and their allocation for beginners
Hey guys , I’m Rocky. This may seem sudden, but have you ever thought about what […]
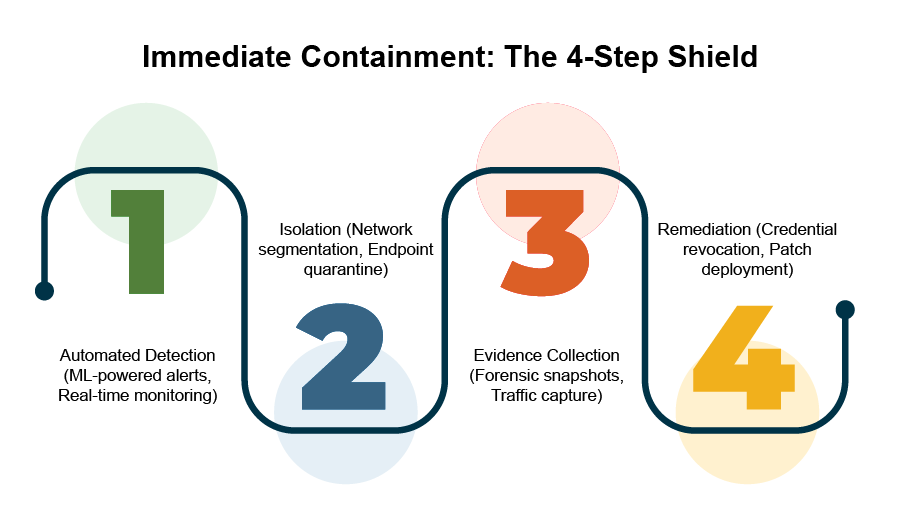
IOC Detection and Response: Strategies for Immediate Threat Containment
Indicators of Compromise (IoCs) act as digital forensic breadcrumbs that point to data breaches. IoCs help […]
The Ethical Hacker’s Playbook for Hacking Web Servers
So you’re interested in cracking the code of how hackers navigate web servers like they own […]
Hello world!
Welcome to WordPress. This is your first post. Edit or delete it, then start writing!

When AI moves beyond human oversight: The cybersecurity risks of self-sustaining systems
Artificial intelligence is no longer just a tool executing predefined commands, it is increasingly capable of […]
Hello world!
Welcome to WordPress. This is your first post. Edit or delete it, then start writing!

Will politicization of security clearances make US cybersecurity firms radioactive?
With the US government now tying security clearances to the support of specific political positions, many […]
How to Secure IoT Devices: A Foolproof Guide for Beginners
The number of connected devices will reach over 17 billion worldwide in 2024. This is a […]
