A Beginner’s Guide to OSINT Analysis with Maltego
Well, if you’ve ever been curious about how investigators dig up all that information online, you’re […]
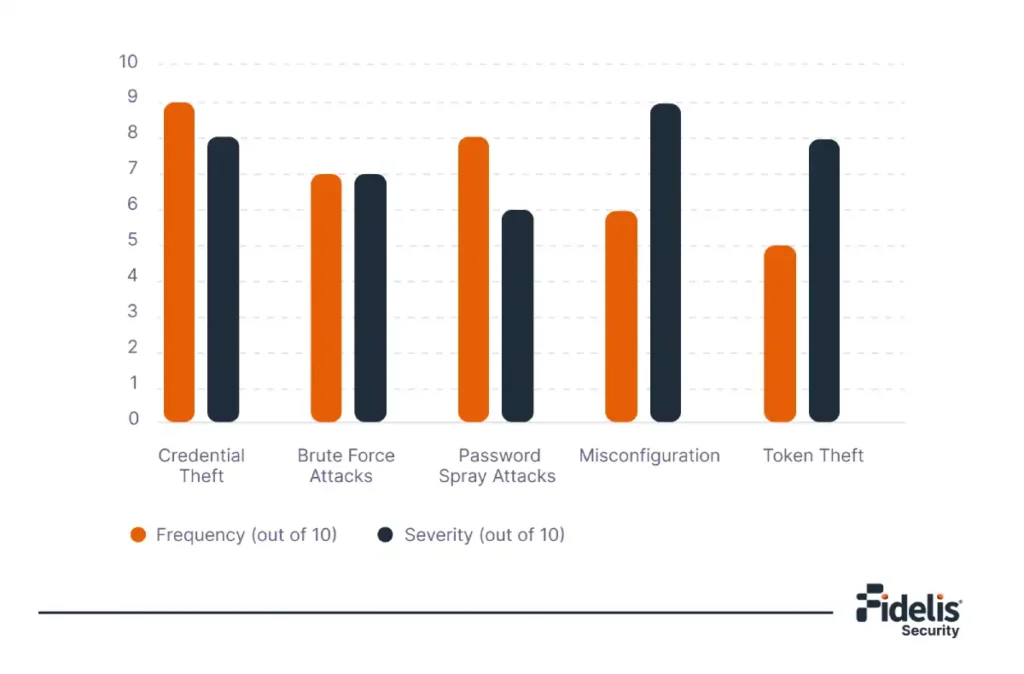
Elevate Your Azure AD Security Before the Next Attack
As 98% of businesses are using some form of cloud computing, keeping track of who has […]
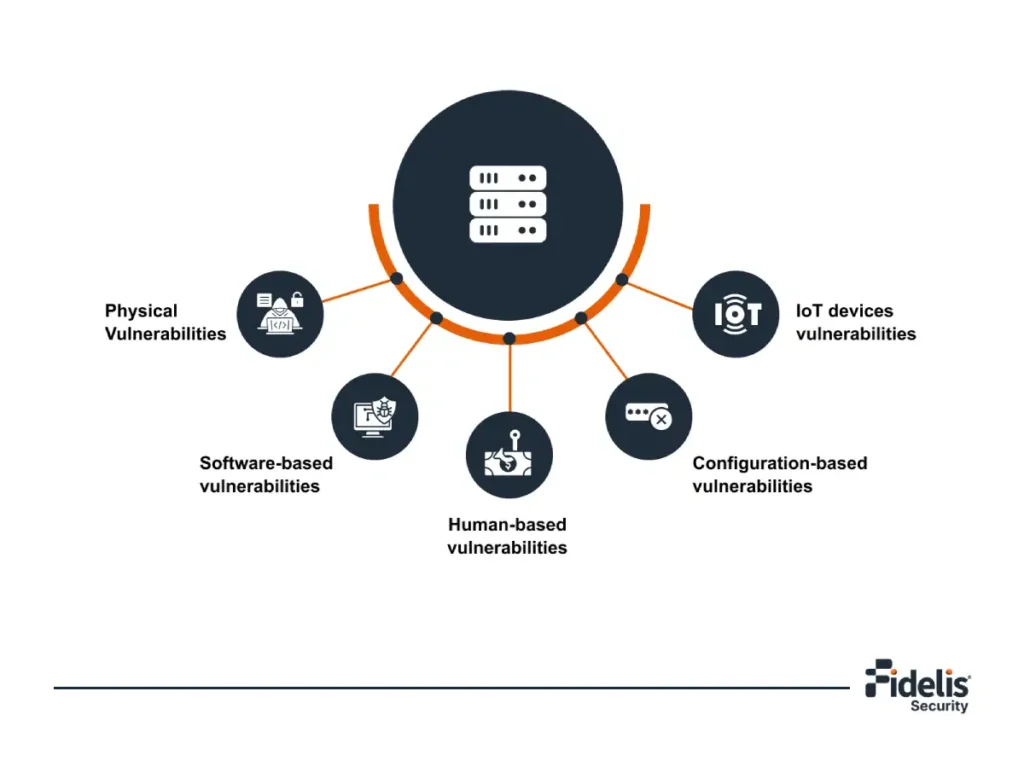
Network Vulnerabilities and Threats: A Cyber-Security Challenge
The digital world is under constant risk as cyber-attacks are becoming increasingly advanced and increasing at […]
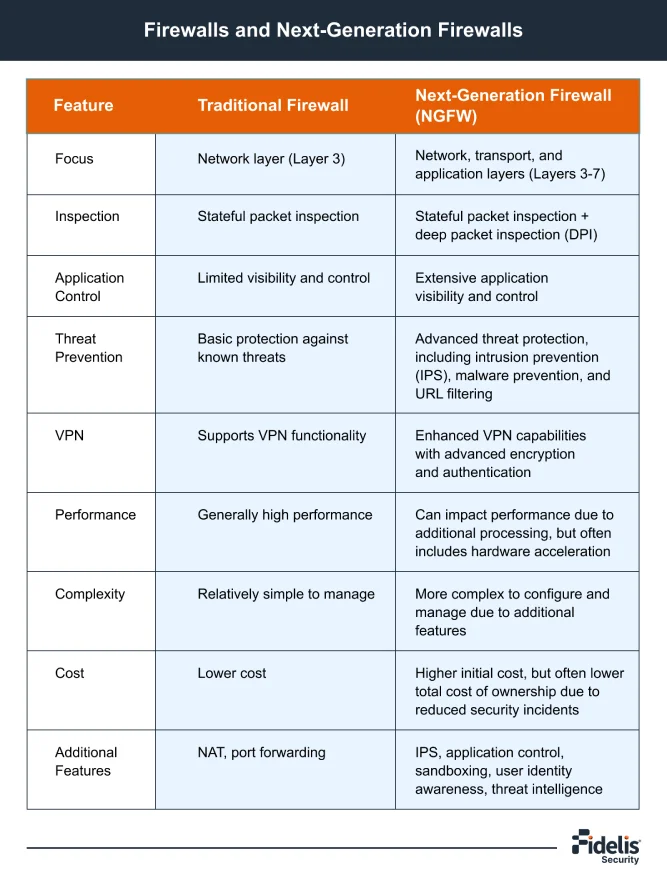
What Are Network Security Solutions?
Picture this, you are trying to protect a chest full of treasure and have no idea […]
The Art of Port Scanning
Well, let’s dive into one of the most essential skills in the world of network security: […]
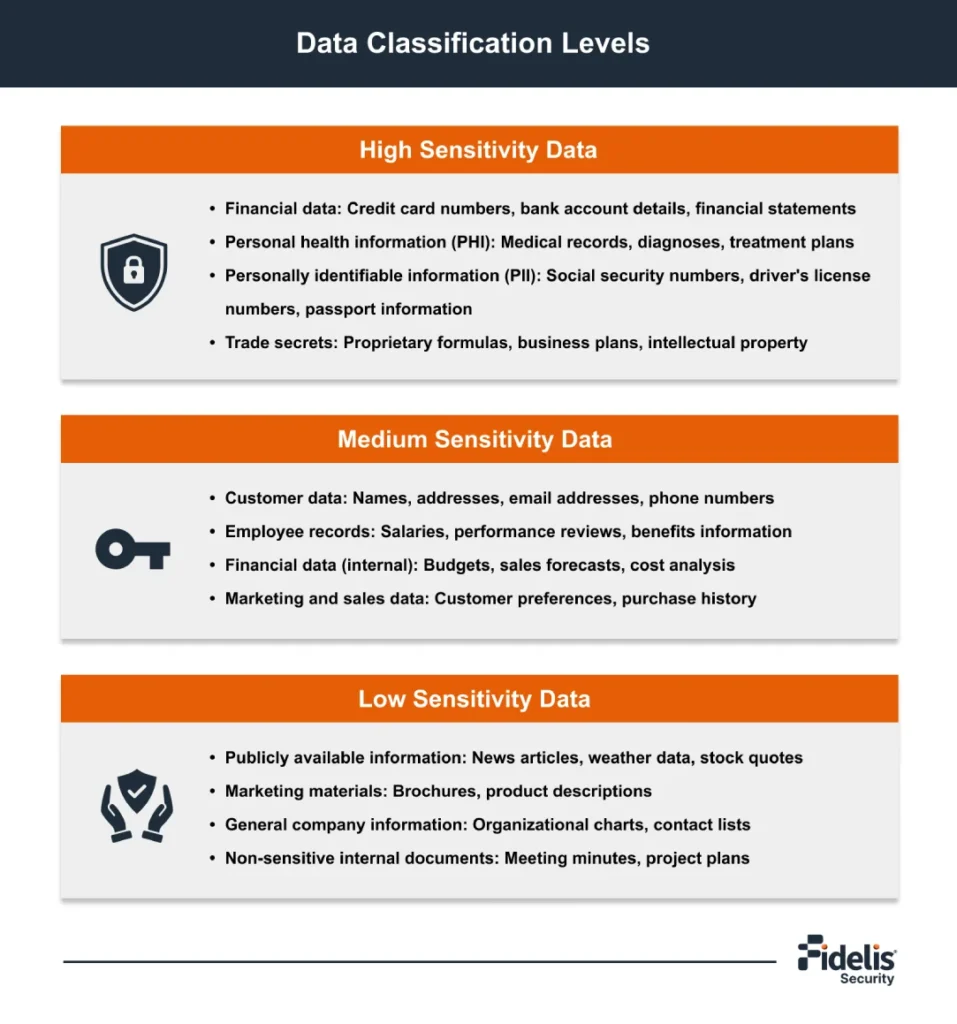
How to Classify, Protect, and Control Your Data: The Ultimate Guide to Data Classification
In our digital world, data fuels businesses. This power brings huge responsibility. Cyber threats are real […]
Why Every Business Needs Hardware Security Module?
In today’s digital age, safeguarding sensitive information is paramount for organizations across all industries. A key […]
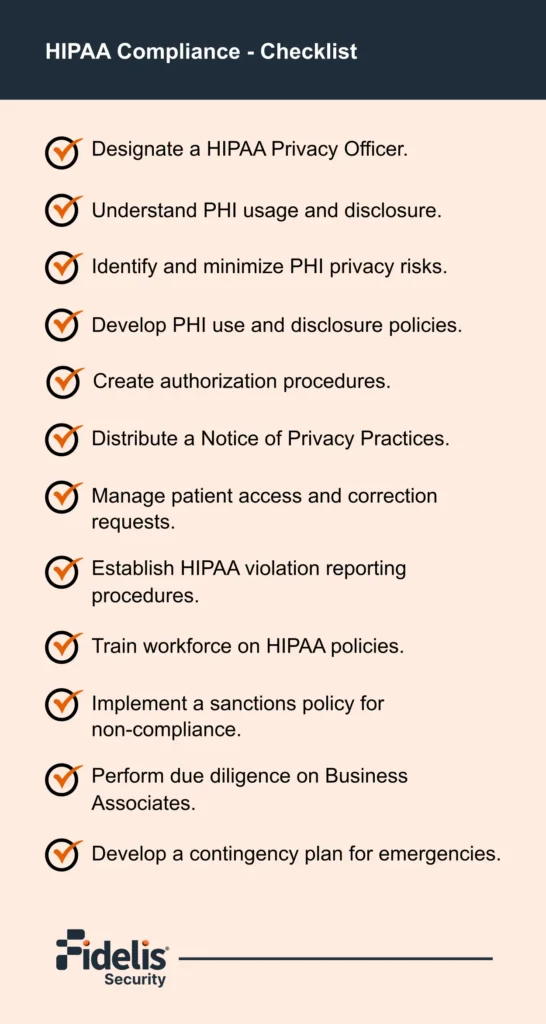
Comprehensive Guide to Healthcare Data Security: Essential Safety and Compliance Tips
Healthcare data security is one of the top responsibilities in this digital age. Since patients’ sensitive […]
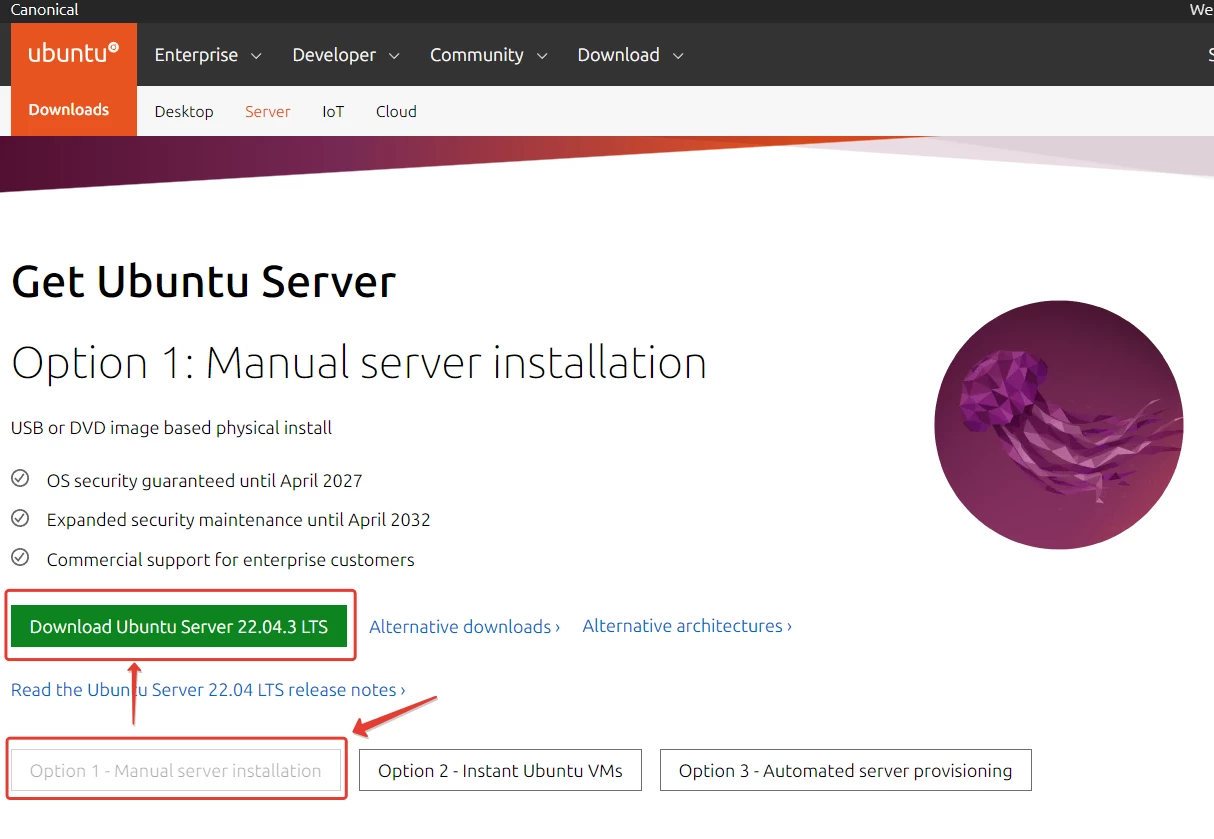
How to Install Linux Ubuntu and Configure as a Server
When we hear the word “server“, we imagine a huge supercomputer that takes up an entire […]
What Is an Endpoint Protection Platform (EPP)?
Defining an Endpoint Protection Platform An Endpoint Protection Platform is an endpoint security capability designed to […]
